有効的なSY0-501問題集はJPNTest.com提供され、SY0-501試験に合格することに役に立ちます!JPNTest.comは今最新SY0-501試験問題集を提供します。JPNTest.com SY0-501試験問題集はもう更新されました。ここでSY0-501問題集のテストエンジンを手に入れます。
SY0-501問題集最新版のアクセス
「715問、30% ディスカウント、特別な割引コード:JPNshiken」
A security analyst reviews the following output:
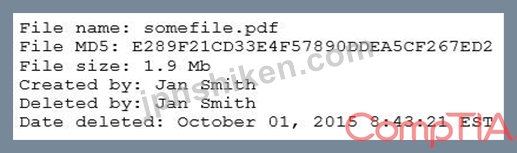
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
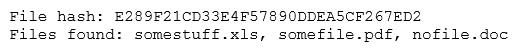
Which of the following is the MOST likely cause of the hash being found in other areas?

The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:

Which of the following is the MOST likely cause of the hash being found in other areas?
正解:B
- 質問一覧「301問」
- 質問1 A member of the admins group reports being unable to modify ...
- 質問2 During a third-party audit, it is determined that a member o...
- 質問3 A company is performing an analysis of the corporate enterpr...
- 質問4 Which of the following is the BEST choice for a security con...
- 質問5 Which of the following must be intact for evidence to be adm...
- 質問6 A manager wants to distribute a report to several other mana...
- 質問7 Ann, a user, reports she is unable to access an application ...
- 質問8 A security administrator needs an external vendor to correct...
- 質問9 A user suspects someone has been accessing a home network wi...
- 質問10 A security analyst notices anomalous activity coming from se...
- 質問11 A company determines that it is prohibitively expensive to b...
- 質問12 A security analyst is acquiring data from a potential networ...
- 質問13 A company's user lockout policy is enabled after five unsucc...
- 質問14 A penetration tester is crawling a target website that is av...
- 質問15 Anne, the Chief Executive Officer (CEO), has reported that s...
- 質問16 A software developer is concerned about DLL hijacking in an ...
- 質問17 A company is developing a new secure technology and requires...
- 質問18 A security administrator is evaluating three different servi...
- 質問19 Joe, a technician, is working remotely with his company prov...
- 質問20 A system administrator needs to implement 802.1x whereby whe...
- 質問21 A server administrator needs to administer a server remotely...
- 質問22 A company has noticed multiple instances of proprietary info...
- 質問23 A user is presented with the following items during the new-...
- 質問24 Which of the following penetration testing concepts is being...
- 質問25 After a recent internal breach, a company decided to regener...
- 質問26 A security analyst is reviewing the following output from an...
- 質問27 Which of the following is an asymmetric function that genera...
- 質問28 A company wants to ensure that the validity of publicly trus...
- 質問29 An employee receives an email, which appears to be from the ...
- 質問30 A malicious system continuously sends an extremely large num...
- 質問31 Ann a security analyst is monitoring the IDS console and not...
- 質問32 A mobile device user is concerned about geographic positioni...
- 質問33 During an application design, the development team specifics...
- 質問34 When performing data acquisition on a workstation, which of ...
- 質問35 An organization plans to implement multifactor authenticatio...
- 質問36 An administrator has configured a new Linux server with the ...
- 質問37 A company is planning to encrypt the files in several sensit...
- 質問38 A software development company needs to share information be...
- 質問39 A home invasion occurred recently in which an intruder compr...
- 質問40 Due to regulatory requirements, a security analyst must impl...
- 質問41 A company has a security policy that specifies all endpoint ...
- 質問42 A web server, which is configured to use TLS with AES-GCM-25...
- 質問43 Which of the following is the BEST explanation of why contro...
- 質問44 A security analyst has been asked to perform a review of an ...
- 質問45 After a user reports stow computer performance, a systems ad...
- 質問46 Which of the following best describes routine in which semic...
- 質問47 A security technician is configuring an access management sy...
- 質問48 Audit logs from a small company's vulnerability scanning sof...
- 質問49 When configuring settings in a mandatory access control envi...
- 質問50 An external attacker can modify the ARP cache of an internal...
- 質問51 An organization is trying to decide which type of access con...
- 質問52 A Chief Information Officer (CIO) drafts an agreement betwee...
- 質問53 A security administrator needs to implement a system that de...
- 質問54 An attacker uses a network sniffer to capture the packets of...
- 質問55 A security engineer is configuring a wireless network that m...
- 質問56 An application team is performing a load-balancing test for ...
- 質問57 A security analyst is hardening an authentication server. On...
- 質問58 A user has attempted to access data at a higher classificati...
- 質問59 A company wants to ensure confidential data from storage med...
- 質問60 A company exchanges information with a business partner. An ...
- 質問61 Company XYZ has decided to make use of a cloud-based service...
- 質問62 Which of the following differentiates a collision attack fro...
- 質問63 A technician receives a device with the following anomalies:...
- 質問64 Which of the following is a document that contains detailed ...
- 質問65 A security engineer wants to implement a site-to-site VPN th...
- 質問66 A security analyst is investigating a suspected security bre...
- 質問67 Which of the following security controls does an iris scanne...
- 質問68 An organization is moving its human resources system to a cl...
- 質問69 Which of the following allows an auditor to test proprietary...
- 質問70 Which of the following BEST describes an attack where commun...
- 質問71 Which of the following should be used to implement voice enc...
- 質問72 Legal authorities notify a company that its network has been...
- 質問73 An attacker compromises a public CA and issues unauthorized ...
- 質問74 A security administrator suspects that data on a server has ...
- 質問75 A remote user (User1) is unable to reach a newly provisioned...
- 質問76 Users in a corporation currently authenticate with a usernam...
- 質問77 A user receives an email from ISP indicating malicious traff...
- 質問78 Which of the following is the appropriate network structure ...
- 質問79 An organization wants to utilize a common, Internet-based th...
- 質問80 A security engineer is faced with competing requirements fro...
- 質問81 Which of the following is the BEST reason for salting a pass...
- 質問82 An organization has implemented an IPSec VPN access for remo...
- 質問83 A vulnerability scan is being conducted against a desktop sy...
- 質問84 When designing a web based client server application with si...
- 質問85 Which of the following would verify that a threat does exist...
- 質問86 The Chief Executive Officer (CEO) of a major defense contrac...
- 質問87 A security analyst is investigating a potential breach. Upon...
- 質問88 A company is terminating an employee for misbehavior. Which ...
- 質問89 A security analyst is inspecting the results of a recent int...
- 質問90 An audit has revealed that database administrators are also ...
- 質問91 Following the successful response to a data-leakage incident...
- 質問92 Which of the following encryption methods does PKI typically...
- 質問93 A company has two wireless networks utilizing captive portal...
- 質問94 A company wants to implement an access management solution t...
- 質問95 Which of the following types of cloud infrastructures would ...
- 質問96 Joe, a security administrator, needs to extend the organizat...
- 質問97 An analyst wants to implement a more secure wireless authent...
- 質問98 Which of the following can affect electrostatic discharge in...
- 質問99 A company hires a consulting firm to crawl its Active Direct...
- 質問100 A portable data storage device has been determined to have m...
- 質問101 Which of the following are used to increase the computing ti...
- 質問102 A small company's Chief Executive Officer (CEO) has asked it...
- 質問103 A systems administrator has isolated an infected system from...
- 質問104 A Chief Information Security Officer (CISO) has tasked a sec...
- 質問105 Which of the following are methods to implement HA in a web ...
- 質問106 Which of the following delineates why it is important to per...
- 質問107 A security administrator wants to configure a company's wire...
- 質問108 The availability of a system has been labeled as the highest...
- 質問109 A security administrator is tasked with implementing central...
- 質問110 Which of the following could occur when both strong and weak...
- 質問111 A company researched the root cause of a recent vulnerabilit...
- 質問112 Which of the following allows an application to securely aut...
- 質問113 A help desk is troubleshooting user reports that the corpora...
- 質問114 A security analyst is mitigating a pass-the-hash vulnerabili...
- 質問115 Phishing emails frequently take advantage of high-profile ca...
- 質問116 After an identified security breach, an analyst is tasked to...
- 質問117 Which of the following threats has sufficient knowledge to c...
- 質問118 A system's administrator has finished configuring firewall A...
- 質問119 A datacenter recently experienced a breach. When access was ...
- 質問120 A security administrator wants to implement a company-wide p...
- 質問121 A technician has installed new vulnerability scanner softwar...
- 質問122 A security administrator is reviewing the following PowerShe...
- 質問123 Which of the following describes the key difference between ...
- 質問124 Before an infection was detected, several of the infected de...
- 質問125 Ann, a customer, is reporting that several important files a...
- 質問126 An organization's primary datacenter is experiencing a two-d...
- 質問127 Given the log output: Max 15 00:15:23.431 CRT: #SEC_LOGIN-5-...
- 質問128 Ann, a user, states that her machine has been behaving errat...
- 質問129 A security administrator is diagnosing a server where the CP...
- 質問130 An administrator is configuring access to information locate...
- 質問131 A systems administrator is attempting to recover from a cata...
- 質問132 Which of the following would meet the requirements for multi...
- 質問133 Which of the following is the proper order for logging a use...
- 質問134 Joe is exchanging encrypted email with another party. Joe en...
- 質問135 A third-party penetration testing company was able to succes...
- 質問136 When generating a request for a new x.509 certificate for se...
- 質問137 An administrator discovers the following log entry on a serv...
- 質問138 An employer requires that employees use a key-generating app...
- 質問139 Upon entering an incorrect password, the logon screen displa...
- 質問140 A copy of a highly confidential salary report was recently f...
- 質問141 A technician is configuring a load balancer for the applicat...
- 質問142 Which of the following should identify critical systems and ...
- 質問143 As part of a new industry regulation, companies are required...
- 質問144 Which of the following is an important step to take BEFORE m...
- 質問145 A systems administrator found a suspicious file in the root ...
- 質問146 Which of the following precautions MINIMIZES the risk from n...
- 質問147 An application was recently compromised after some malformed...
- 質問148 A network administrator needs to allocate a new network for ...
- 質問149 Which of the following attack types BEST describes a client-...
- 質問150 A company recently replaced its unsecure email server with a...
- 質問151 Which of the following technologies would be MOST appropriat...
- 質問152 Joe notices there are several user accounts on the local net...
- 質問153 A computer emergency response team is called at midnight to ...
- 質問154 An incident response manager has started to gather all the f...
- 質問155 An external contractor, who has not been given information a...
- 質問156 A security engineer must install the same x.509 certificate ...
- 質問157 A forensic expert is given a hard drive from a crime scene a...
- 質問158 When systems, hardware, or software are not supported by the...
- 質問159 A database backup schedule consists of weekly full backups p...
- 質問160 The Chief Security Officer (CISO) at a multinational banking...
- 質問161 Which of the following are MOST susceptible to birthday atta...
- 質問162 A web developer improves client access to the company's REST...
- 質問163 A Chief Information Officer (CIO) recently saw on the news t...
- 質問164 A network administrator at a small office wants to simplify ...
- 質問165 A security administrator has been assigned to review the sec...
- 質問166 A security manager is creating an account management policy ...
- 質問167 A security analyst reviews the following output: (Exhibit) T...
- 質問168 A network operations manager has added a second row of serve...
- 質問169 A system administrator wants to implement an internal commun...
- 質問170 Which of the following is commonly used for federated identi...
- 質問171 The Chief Information Security Officer (CISO) is asking for ...
- 質問172 Which of the following vulnerability types would the type of...
- 質問173 When attackers use a compromised host as a platform for laun...
- 質問174 A new hire wants to use a personally owned phone to access c...
- 質問175 A security program manager wants to actively test the securi...
- 質問176 A security analyst is diagnosing an incident in which a syst...
- 質問177 A user typically works remotely over the holidays using a we...
- 質問178 A user needs to send sensitive information to a colleague us...
- 質問179 An organization's internal auditor discovers that large sums...
- 質問180 A security administrator wants to implement a logon script t...
- 質問181 A hacker has a packet capture that contains: (Exhibit) Which...
- 質問182 Which of the following could help detect trespassers in a se...
- 質問183 Which of the following metrics are used to calculate the SLE...
- 質問184 An organization recently moved its custom web applications t...
- 質問185 An attacker exploited a vulnerability on a mail server using...
- 質問186 An information security analyst needs to work with an employ...
- 質問187 An organization finds that most help desk calls are regardin...
- 質問188 A security administrator suspects that a DDoS attack is affe...
- 質問189 A technician is investigating a potentially compromised devi...
- 質問190 A security analyst is reviewing the following packet capture...
- 質問191 Which of the following is the LEAST secure hashing algorithm...
- 質問192 New magnetic locks were ordered for an entire building. In a...
- 質問193 A business has recently deployed laptops to all sales employ...
- 質問194 A company is deploying a new VoIP phone system. They require...
- 質問195 While performing surveillance activities, an attacker determ...
- 質問196 Which of the following components of printers and MFDs are M...
- 質問197 A number of employees report that parts of an ERP applicatio...
- 質問198 A Chief Executive Officer (CEO) suspects someone in the lab ...
- 質問199 A forensic investigator has run into difficulty recovering u...
- 質問200 Joe, a user, has been trying to send Ann, a different user, ...
- 質問201 After a merger between two companies a security analyst has ...
- 質問202 Which of the following solutions should an administrator use...
- 質問203 A member of a digital forensics team, Joe arrives at a crime...
- 質問204 A security engineer is configuring a system that requires th...
- 質問205 A security analyst receives an alert from a WAF with the fol...
- 質問206 An audit takes place after company-wide restricting, in whic...
- 質問207 A business sector is highly competitive, and safeguarding tr...
- 質問208 Company A agrees to provide perimeter protection, power, and...
- 質問209 An organization has determined it can tolerate a maximum of ...
- 質問210 Ann, a security administrator, wants to ensure credentials a...
- 質問211 A cybersecurity analyst is looking into the payload of a ran...
- 質問212 Which of the following would MOST likely appear in an uncred...
- 質問213 A new security administrator ran a vulnerability scanner for...
- 質問214 A security administrator has been tasked with improving the ...
- 質問215 Which of the following controls allows a security guard to p...
- 質問216 Which of the following cryptographic algorithms is irreversi...
- 質問217 A penetration tester finds that a company's login credential...
- 質問218 The data backup window has expanded into the morning hours a...
- 質問219 A website administrator has received an alert from an applic...
- 質問220 A workstation puts out a network request to locate another s...
- 質問221 Two users need to send each other emails over unsecured chan...
- 質問222 A penetration testing is preparing for a client engagement i...
- 質問223 A system administrator wants to provide balance between the ...
- 質問224 In a corporation where compute utilization spikes several ti...
- 質問225 A global gaming console manufacturer is launching a new gami...
- 質問226 The IT department needs to prevent users from installing unt...
- 質問227 An active/passive configuration has an impact on:...
- 質問228 A company's loss control department identifies theft as a re...
- 質問229 Which of the following is the BEST reason to run an untested...
- 質問230 A systems administrator is configuring a system that uses da...
- 質問231 Joe a computer forensic technician responds to an active com...
- 質問232 Joe, a user, wants to send Ann, another user, a confidential...
- 質問233 An analyst is reviewing a simple program for potential secur...
- 質問234 A new intern in the purchasing department requires read acce...
- 質問235 Which of the following is a deployment concept that can be u...
- 質問236 Which of the following cryptographic attacks would salting o...
- 質問237 A network administrator adds an ACL to allow only HTTPS conn...
- 質問238 A security administrator determined that users within the co...
- 質問239 The security administrator has noticed cars parking just out...
- 質問240 A wireless network has the following design requirements: Au...
- 質問241 Which of the following types of penetration test will allow ...
- 質問242 An organization wants to conduct secure transactions of larg...
- 質問243 A security administrator is trying to encrypt communication....
- 質問244 Which of the following network vulnerability scan indicators...
- 質問245 The administrator installs database software to encrypt each...
- 質問246 The help desk is receiving numerous password change alerts f...
- 質問247 Joe, an employee, wants to show his colleagues how much he k...
- 質問248 Which of the following locations contain the MOST volatile d...
- 質問249 Which of the following would be considered multifactor authe...
- 質問250 A systems administrator wants to protect data stored on mobi...
- 質問251 Two users must encrypt and transmit large amounts of data be...
- 質問252 A botnet has hit a popular website with a massive number of ...
- 質問253 Every morning, a systems administrator monitors failed login...
- 質問254 A security administrator has configured a RADIUS and a TACAC...
- 質問255 The POODLE attack is an MITM exploit that affects:...
- 質問256 An attacker captures the encrypted communication between two...
- 質問257 An auditor has identified an access control system that can ...
- 質問258 During a routine vulnerability assessment, the following com...
- 質問259 Which of the following best describes the initial processing...
- 質問260 A security consultant discovers that an organization is usin...
- 質問261 A system administrator wants to provide for and enforce wire...
- 質問262 An organization has several production-critical SCADA superv...
- 質問263 A company has a data classification system with definitions ...
- 質問264 A security analyst is working on a project that requires the...
- 質問265 Company policy requires the use if passphrases instead if pa...
- 質問266 A supervisor in your organization was demoted on Friday afte...
- 質問267 A security administrator learns that PII, which was gathered...
- 質問268 Which of the following should a security analyst perform FIR...
- 質問269 Technicians working with servers hosted at the company's dat...
- 質問270 Which of the following types of attacks precedes the install...
- 質問271 A consultant has been tasked to assess a client's network. T...
- 質問272 Several workstations on a network are found to be on OS vers...
- 質問273 A security analyst is securing smartphones and laptops for a...
- 質問274 An information security specialist is reviewing the followin...
- 質問275 As part of a new BYOD rollout, a security analyst has been a...
- 質問276 A vulnerability scanner that uses its running service's acce...
- 質問277 A dumpster diver recovers several hard drives from a company...
- 質問278 An administrator has concerns regarding the traveling sales ...
- 質問279 A new firewall has been places into service at an organizati...
- 質問280 While working on an incident, Joe, a technician, finished re...
- 質問281 An organization is using a tool to perform a source code rev...
- 質問282 A chief Financial Officer (CFO) has asked the Chief Informat...
- 質問283 Six months into development, the core team assigned to imple...
- 質問284 The help desk received a call after hours from an employee w...
- 質問285 An auditor is reviewing the following output from a password...
- 質問286 An organization needs to implement a large PKI. Network engi...
- 質問287 A computer on a company network was infected with a zero-day...
- 質問288 Recently several employees were victims of a phishing email ...
- 質問289 An organization has hired a penetration tester to test the s...
- 質問290 Ann, a college professor, was recently reprimanded for posti...
- 質問291 A security administrator has written a script that will auto...
- 質問292 Ann is the IS manager for several new systems in which the c...
- 質問293 The security administrator receives an email on a non-compan...
- 質問294 Ann, a security administrator, has been instructed to perfor...
- 質問295 Which of the following is the GREATEST risk to a company by ...
- 質問296 Which of the following specifically describes the exploitati...
- 質問297 A security analyst is updating a BIA document. The security ...
- 質問298 The process of applying a salt and cryptographic hash to a p...
- 質問299 A security analyst has received the following alert snippet ...
- 質問300 A technician must configure a firewall to block external DNS...
- 質問301 After a security incident, management is meeting with involv...

