- ホーム
- CompTIA
- CS0-003J - CompTIA Cybersecurity Analyst (CySA+) Certification Exam (CS0-003日本語版)
- CompTIA.CS0-003J.v2025-01-30.q174
- 質問84
有効的なCS0-003J問題集はJPNTest.com提供され、CS0-003J試験に合格することに役に立ちます!JPNTest.comは今最新CS0-003J試験問題集を提供します。JPNTest.com CS0-003J試験問題集はもう更新されました。ここでCS0-003J問題集のテストエンジンを手に入れます。
CS0-003J問題集最新版のアクセス
「622問、30% ディスカウント、特別な割引コード:JPNshiken」
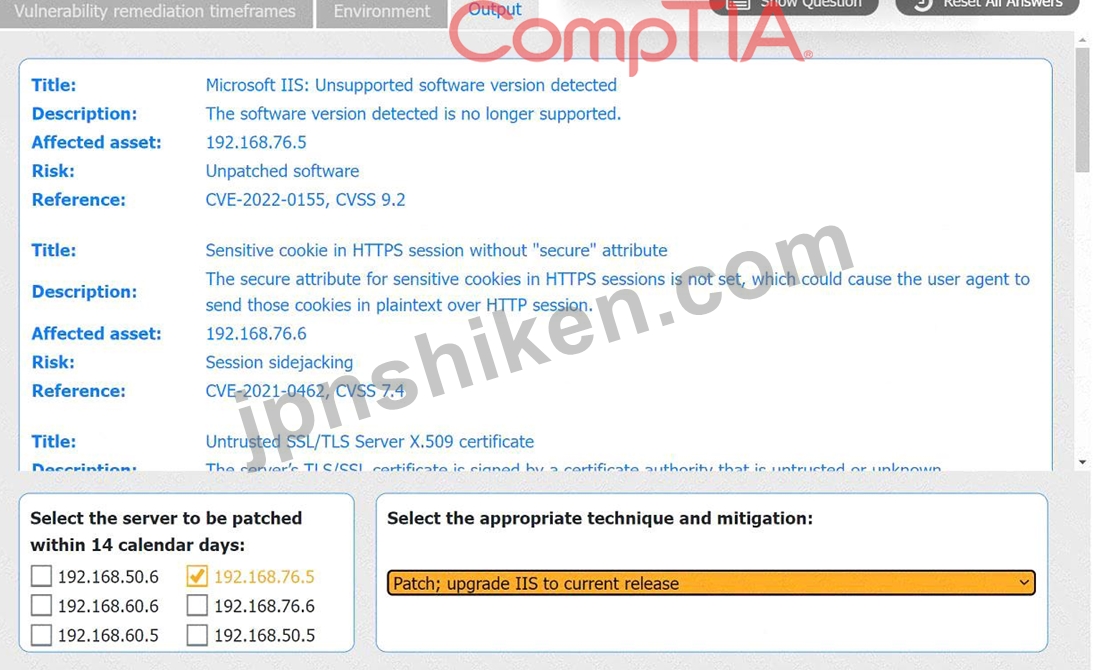
システム管理者が脆弱性スキャンの出力を確認しています。
説明書
各タブの情報を確認します。
組織の環境アーキテクチャと修復基準に基づいて、14 日以内にパッチを適用するサーバーを選択し、適切な手法と緩和策を選択します。




説明書
各タブの情報を確認します。
組織の環境アーキテクチャと修復基準に基づいて、14 日以内にパッチを適用するサーバーを選択し、適切な手法と緩和策を選択します。




正解:
see the explanation for step by step solution.
Explanation:
Step 1: Reviewing the Vulnerability Remediation Timeframes
The remediation standards require servers to be patched based on their CVSS score:
* CVSS > 9.0: Patch within 7 days
* CVSS 7.9 - 9.0: Patch within 14 days
* CVSS 5.0 - 7.9: Patch within 30 days
* CVSS 0 - 5.0: Patch within 60 days
Step 2: Analyzing the Output Tab
From the Output tab:
* Server 192.168.76.5 has a CVSS score of 9.2 for an unsupported Microsoft IIS version, indicating a critical vulnerability requiring a patch within 7 days.
* Server 192.168.76.6 has a CVSS score of 7.4 for a missing secure attribute on HTTPS cookies, which falls in the 5.0 - 7.9 range, requiring a patch within 30 days.
Since the question asks for the server to be patched within 14 days, we need to focus on servers with CVSS
7.9 - 9.0:
* None of the servers have a CVSS score that falls precisely in the 7.9 - 9.0 range.
* However, 192.168.76.5, with a CVSS score of 9.2, has a vulnerability that necessitates a quick response and fits as it must be patched within the shortest timeframe (7 days, which includes 14 days).
The server that fits within a 14-day urgency, based on standard practices, would be 192.168.76.5.
Step 3: Reviewing the Environment Tab
The Environment Tab provides additional context for 192.168.76.5:
* It's in the dev environment, which is internal and not publicly accessible.
* MFA is required, indicating security measures are already present.
Step 4: Selecting the Appropriate Technique and Mitigation
For 192.168.76.5, with the Microsoft IIS unsupported version:
* Patch; upgrade IIS to the current release is the most suitable option, as upgrading IIS will resolve the unsupported software vulnerability by bringing it up-to-date with supported versions.
* This technique addresses the root cause, which is the unpatched, outdated software.
Summary
* Server to be patched within 14 calendar days: 192.168.76.5
* Appropriate technique and mitigation: Patch; upgrade IIS to the current release This approach ensures that the most critical vulnerabilities are addressed promptly, maintaining security compliance.
Explanation:
Step 1: Reviewing the Vulnerability Remediation Timeframes
The remediation standards require servers to be patched based on their CVSS score:
* CVSS > 9.0: Patch within 7 days
* CVSS 7.9 - 9.0: Patch within 14 days
* CVSS 5.0 - 7.9: Patch within 30 days
* CVSS 0 - 5.0: Patch within 60 days
Step 2: Analyzing the Output Tab
From the Output tab:
* Server 192.168.76.5 has a CVSS score of 9.2 for an unsupported Microsoft IIS version, indicating a critical vulnerability requiring a patch within 7 days.
* Server 192.168.76.6 has a CVSS score of 7.4 for a missing secure attribute on HTTPS cookies, which falls in the 5.0 - 7.9 range, requiring a patch within 30 days.
Since the question asks for the server to be patched within 14 days, we need to focus on servers with CVSS
7.9 - 9.0:
* None of the servers have a CVSS score that falls precisely in the 7.9 - 9.0 range.
* However, 192.168.76.5, with a CVSS score of 9.2, has a vulnerability that necessitates a quick response and fits as it must be patched within the shortest timeframe (7 days, which includes 14 days).
The server that fits within a 14-day urgency, based on standard practices, would be 192.168.76.5.
Step 3: Reviewing the Environment Tab
The Environment Tab provides additional context for 192.168.76.5:
* It's in the dev environment, which is internal and not publicly accessible.
* MFA is required, indicating security measures are already present.
Step 4: Selecting the Appropriate Technique and Mitigation
For 192.168.76.5, with the Microsoft IIS unsupported version:
* Patch; upgrade IIS to the current release is the most suitable option, as upgrading IIS will resolve the unsupported software vulnerability by bringing it up-to-date with supported versions.
* This technique addresses the root cause, which is the unpatched, outdated software.
Summary
* Server to be patched within 14 calendar days: 192.168.76.5
* Appropriate technique and mitigation: Patch; upgrade IIS to the current release This approach ensures that the most critical vulnerabilities are addressed promptly, maintaining security compliance.

- 質問一覧「174問」
- 質問1 アナリストは、企業インフラストラクチャの定期的な脆弱性評価を
- 質問2 インシデント対応チームは、法執行機関と協力して、アクティブな
- 質問3 サイバーセキュリティインシデントが発生した際、境界ネットワー
- 質問4 クラウド顧客とクラウド サービスの間でセキュリティ ポリシーを...
- 質問5 インシデント対応アナリストは、会社の管理者だけをターゲットに
- 質問6 電子メール クライアントを最新のパッチに更新した後、従業員の
- 質問7 脆弱性アナリストが、過去 1 か月間に特定された最新の、最も重...
- 質問8 セキュリティ マネージャーは、CVSSv3 に依存する会社の現在の方...
- 質問9 セキュリティ アナリストがフィッシングメールを調査中に、進行
- 質問10 最高情報セキュリティ責任者は、ゼロトラスト アプローチの一環
- 質問11 中小企業には、給与管理における誤りや不正を防ぐために職務を効
- 質問12 アナリストは、一見無制限の時間とリソースを使って、攻撃者から
- 質問13 従業員がフリーウェア プログラムをダウンロードして、デスクト
- 質問14 フィッシングに関連するインシデントが発生した場合、セキュリテ
- 質問15 最高経営責任者 (CEO) から、機密の企業秘密が漏洩したとの通知...
- 質問16 クラウド チームは、未承認のリソースが自動プロビジョニングさ
- 質問17 新しい SOC マネージャーは、改善を行うために、前回のテーブル...
- 質問18 アナリストは、Web プロキシとファイアウォールで以前にブロック...
- 質問19 脆弱性管理チームは評価中に 4 つの主要な脆弱性を発見し、さら...
- 質問20 発電所の遠心ポンプを駆動する組み込みソフトウェアに必要な保証
- 質問21 セキュリティ アナリストが最近チームに加わり、実稼働スクリプ
- 質問22 ある組織は最近、BC 計画と DR 計画を変更しました。インシデン...
- 質問23 侵入分析のダイヤモンド モデルの利点は次のどれですか?
- 質問24 アナリストが突然、ファイアウォールからデータを拡充できなくな
- 質問25 セキュリティ アナリストは、組織に影響を与えた新しいマルウェ
- 質問26 地理的に多様な従業員と動的 IP を抱える企業は、ネットワーク ...
- 質問27 インシデント発生中、ネットワークのセグメント内のサーバー群で
- 質問28 アナリストは複数のシステムでイベントを調査していますが、デー
- 質問29 セキュリティ アナリストは、インフラストラクチャ チームが新し...
- 質問30 ベストプラクティスとして、インシデント報告を一般の人々に伝え
- 質問31 セキュリティ アナリストは、顧客のネットワーク上で制御不能に
- 質問32 SOC マネージャーは動揺した顧客から電話を受けました。顧客は 2...
- 質問33 ゼロデイ コマンド インジェクションの脆弱性が公開されました。...
- 質問34 次の利害関係者のうち、脆弱性スキャン レポートを受け取る可能
- 質問35 会社のユーザー アカウントが侵害されました。また、ユーザーか
- 質問36 セキュリティ アナリストは、監査プロセスのために企業のネット
- 質問37 最近、攻撃者が金融機関のデータベースに不正アクセスしました。
- 質問38 侵入テスターは、組織のソフトウェア開発 Web サイトでテストを...
- 質問39 セキュリティ アナリストは、ネットワーク ルーティング上の異常...
- 質問40 あなたは、会社のサーバーからのスキャンデータを解釈する任務を
- 質問41 組織が侵害され、全従業員のユーザー名とパスワードがオンライン
- 質問42 ある組織は、大量のデータがネットワークから送信されていること
- 質問43 会社が所有し管理しているラップトップにマルウェアが感染してい
- 質問44 セキュリティ アナリストは、Burp Suite を使用して Web アプリ...
- 質問45 社内コードレビュー中に、「ACE」と呼ばれるソフトウェアに、任...
- 質問46 インシデント発生中、アナリストは調査チームとリーダーシップ
- 質問47 既知の脅威を所定の期間内に修復する必要があるプロセスを最もよ
- 質問48 レポートには、Web アプリケーションの特定のバージョンの脆弱性...
- 質問49 脆弱性アナリストは、社内で使用されているワークステーションに
- 質問50 従業員が Web サイトにアクセスしたため、デバイスが侵入的なマ...
- 質問51 攻撃者がインフラストラクチャ上で技術を使用してターゲットの情
- 質問52 組織は、クラウド インフラストラクチャの構成が強化されている
- 質問53 SOC マネージャーは、脆弱性を管理するための報告プロセスを確立...
- 質問54 次のCVSS文字列があるとします。 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/...
- 質問55 あなたの会社の従業員約 100 名がフィッシング メールを受信しま...
- 質問56 アナリストは、次のエントリを含むサーバー環境の脆弱性レポート
- 質問57 規制対象の組織でセキュリティ侵害が発生し、顧客名とそれに対応
- 質問58 OWASP Web セキュリティ テスト ガイドに記載されている脅威モデ...
- 質問59 MOU を実施する最も適切な理由は次のどれですか?
- 質問60 従業員はブラウザを更新した後、アカウントにログインできなくな
- 質問61 SIEM アラート内の IP アドレスが既知の悪意のある IP アドレス...
- 質問62 セキュリティアナリストは、Web サーバー ログに次のエントリが...
- 質問63 セキュリティ運用チームは、ツールとポータルが冗長であるため、
- 質問64 セキュリティ アナリストは、企業の Web アプリケーションに関す...
- 質問65 パッチ適用は午前 2 時から午前 4 時までの間にのみ行われるとい...
- 質問66 セキュリティ チームは、セキュリティ イベント後に誰が次のステ...
- 質問67 サイバーセキュリティ アナリストが脅威ハンティング チームに配...
- 質問68 セキュリティ アナリストは、USB インターフェイスを介してソフ...
- 質問69 悪意のある攻撃者がソーシャル エンジニアリングを使用して内部
- 質問70 ある企業が脆弱性管理プログラムを実装し、オンプレミス環境から
- 質問71 長期休暇中に、ある会社でセキュリティ インシデントが発生しま
- 質問72 情報セキュリティ プログラムを成功させるための重要な要素を最
- 質問73 境界ネットワーク内の Web サーバーのスキャン中に、ポート 3389...
- 質問74 過去 1 時間に、重要なサーバーで大量の失敗した RDP 認証試行が...
- 質問75 組織の有力な営業担当者であるジョーは、現在の雇用主と競合する
- 質問76 脆弱性評価チームが定期レポートを他のチームと共有するたびに、
- 質問77 従業員はブラウザを更新した後、アカウントにログインできなくな
- 質問78 セキュリティ アナリストは、Web サーバーに対して実行された脆...
- 質問79 脅威アクターは、技術フォーラムから収集したオープンソースの情
- 質問80 アナリストはフィッシング インシデントを調査しており、調査の
- 質問81 アナリストがウェブサイトを調査し、次の結果を得ました。 2022-...
- 質問82 アナリストは次のログ エントリを表示します。 (Exhibit) 組織に...
- 質問83 インシデント対応レポートを提供する際のタイムラインの重要性を
- 質問84 システム管理者が脆弱性スキャンの出力を確認しています。 説明
- 質問85 新しいサイバーセキュリティ アナリストは、組織に対する潜在的
- 質問86 サイバーセキュリティ アナリストは SIEM ログを調査し、内部ホ...
- 質問87 セキュリティ アナリストが、組織の POS アプリケーションで中程...
- 質問88 ある組織が顧客トランザクションの侵害を経験しました。PCI DSS ...
- 質問89 ある企業は最近、すべてのエンド ユーザー ワークステーションか...
- 質問90 起こり得るインシデントへの備えとしての災害復旧演習の目標を最
- 質問91 SOC アナリストは、デバイスのオペレーティング システムに関係...
- 質問92 セキュリティ アナリストが、内部ネットワークで侵害された電子
- 質問93 ある組織では、次の表にリストされているいくつかのインシデント
- 質問94 広く使用されている OS のサポート終了日が発表されました。ビジ...
- 質問95 セキュリティ アナリストが Web サーバーのログを確認していると...
- 質問96 組織に影響を与えるインシデントに関連する公式の公開コミュニケ
- 質問97 SOC チーム リーダーは、調査のために DNS 情報を収集することが...
- 質問98 セキュリティ アナリストは、次のコマンドを含むエクスプロイト
- 質問99 次のどれを使用すると、さまざまなアプリケーションや内部アプリ
- 質問100 セキュリティ アナリストは、重要なシステム上の FIM によってト...
- 質問101 ある組織が企業の Web サイトに対して Web アプリケーションの脆...
- 質問102 組織外への PII の漏洩を防ぐために最も効果的なツールは次のう...
- 質問103 最高情報セキュリティ責任者は、新しい脆弱性スキャン プロジェ
- 質問104 統合されたダッシュボードを更新するために使用される可能性が高
- 質問105 組織は、無効なデータ、予期しないデータ、またはランダムなデー
- 質問106 企業には次のセキュリティ要件があります。 。パブリックIPはあ...
- 質問107 セキュリティ アナリストは、複数の Windows マルウェア バイナ...
- 質問108 ある組織が弁護士から法的保留要求を受け取りました。この要求は
- 質問109 脅威を特定した後、企業は脆弱性を修復するためにパッチ管理プロ
- 質問110 ある組織が電子商取引アプリケーションのパイロット展開を実施し
- 質問111 AXSS 脆弱性が、ある企業の機密性やミッションクリティカル性に...
- 質問112 電子メール ホスティング プロバイダーは、新しいパブリック IP ...
- 質問113 インシデント対応チームは、インターネット障害の調査を開始する
- 質問114 サイバー キル チェーンの方法論を最も正確に説明しているのは次...
- 質問115 ある企業は、システムを評価するために新しい脆弱性スキャン ソ
- 質問116 アナリストのチームは、さまざまなソースからの情報を相関させる
- 質問117 脆弱性管理チームは、毎週のスキャンで見つかったすべての脆弱性
- 質問118 サイバーセキュリティ侵害に関する最近のインシデントに関する「
- 質問119 Web アプリケーションには、内部 URL からコンテンツを取得して...
- 質問120 根本原因分析を実施する最適な理由は次のうちどれですか?
- 質問121 最高情報セキュリティ責任者 (CISO) は、企業の業種をターゲット...
- 質問122 会社のウイルス対策ソフトによって適切に阻止されなかった新たな
- 質問123 ある企業が自動化ソフトウェアを使用してサーバーにパッチを適用
- 質問124 セキュリティ アナリストは、ネットワークへの悪意のある攻撃を
- 質問125 暗号通貨サービス会社は、自社システム上のデータの正確性を確保
- 質問126 悪用される可能性の高い 2 つの脆弱性に対するパッチが、同じ金...
- 質問127 医療機関は、リスク評価の結果に基づいて行動計画を策定する必要
- 質問128 セキュリティ アナリストは、インシデントに関連するデジタル証
- 質問129 セキュリティ アナリストは、特定のユーザーによる複数の MFA ロ...
- 質問130 会社のデバイスに関連するインシデントが発生したため、インシデ
- 質問131 複数の SaaS アプリケーションのクラウド移行に着手する際、組織...
- 質問132 アナリストは銀行のメッセージ システムを設計しています。アナ
- 質問133 すべてのネットワーク ユーザーが既知のソースからの添付ファイ
- 質問134 ある組織がデータ侵害を発見し、その結果 Pll が一般に公開され...
- 質問135 ネットワーク アナリストは、WAN 接続の反対側にある 2 つの IP ...
- 質問136 机上演習の目標を最もよく表しているものは次のうちどれですか?
- 質問137 サイバーセキュリティ チームは最近、オペレーティング システム...
- 質問138 アナリストは脆弱性レポートをレビューしており、経営陣に勧告を
- 質問139 セキュリティ アナリストは、基盤となるホストから資格情報を抽
- 質問140 アナリストは、侵害の可能性があるホストを調査しているときに、
- 質問141 SIEM、SOAR、チケット発行システムへの最近の投資を考慮すると、...
- 質問142 国民国家の主体として最も関心が低いのは次のうちどれですか?
- 質問143 開発チームは、Web アプリケーションのベータ版の公開を準備して...
- 質問144 ある会社が社内ネットワークで新しいアプリケーションを立ち上げ
- 質問145 ローカルにホストされているサーバーに関連するセキュリティ リ
- 質問146 組織の電子メール アカウントが悪意のある人物によって侵害され
- 質問147 インシデント中に、セキュリティ アナリストは、大量の Pll が従...
- 質問148 セキュリティ アナリストがネットワーク上の脆弱性スキャンを実
- 質問149 インターネットに公開されている Web サーバーの脆弱性スキャン...
- 質問150 攻撃者が LAN 上の syslog サーバーにアクセスしたところです。s...
- 質問151 ファイル共有サービスを介して機密情報が開示されたという報告が
- 質問152 攻撃者が悪用に成功したターゲットとの通信を確立しようとするの
- 質問153 脅威アクターの行動を伝達するために一般的に使用される 4 つの...
- 質問154 通常のセキュリティ監視アクティビティ中に、次のアクティビティ
- 質問155 卓上演習中に、エンジニアはハードウェアのバージョンの非互換性
- 質問156 ゼロ トラスト アーキテクチャの一部としてのネットワーク マイ...
- 質問157 最近のゼロデイ脆弱性が積極的に悪用されており、ユーザーの操作
- 質問158 脆弱性スキャン中に、いくつかの重大なバグが特定されました。SL...
- 質問159 インシデント発生中、アナリストは後の調査のために証拠を入手す
- 質問160 1 時間以内に、重要なサーバーで大量の失敗した RDP 認証試行が...
- 質問161 組織の環境内の 2 つのワークステーションで疑わしいワンライナ...
- 質問162 企業のセキュリティ チームは、リソースの不適切な使用 (オフィ...
- 質問163 脅威インテリジェンス プログラムの一部として TAXII を実装する...
- 質問164 セキュリティ アナリストは、潜在的に侵害されたマシンからの FT...
- 質問165 セキュリティ アナリストは、分析するために悪意のあるバイナリ ...
- 質問166 アナリストは、最近の脆弱性スキャンに基づいて推奨事項を提供す
- 質問167 サイバーセキュリティ アナリストが、最近侵害を受けたサーバー
- 質問168 インシデント対応チームが重要なサーバーで IoC を発見しま...
- 質問169 システム管理者は、運用サーバー上に見慣れないディレクトリ名が
- 質問170 調査を開始するとき、最初に行う必要があるのは次のうちどれです
- 質問171 最高情報セキュリティ責任者 (CISO) は、学んだ教訓と関連する事...
- 質問172 SOC アナリストは、重複を削除することで、報告されたアラームの...
- 質問173 攻撃を受けた後、アナリストは最高情報セキュリティ責任者にイベ
- 質問174 セキュリティアナリストが組織の既知のさまざまな敵対者間の TTP...

