- ホーム
- CompTIA
- CAS-004-JPN - CompTIA Advanced Security Practitioner (CASP+) Exam (CAS-004日本語版)
- CompTIA.CAS-004-JPN.v2024-09-24.q221
- 質問88
有効的なCAS-004-JPN問題集はJPNTest.com提供され、CAS-004-JPN試験に合格することに役に立ちます!JPNTest.comは今最新CAS-004-JPN試験問題集を提供します。JPNTest.com CAS-004-JPN試験問題集はもう更新されました。ここでCAS-004-JPN問題集のテストエンジンを手に入れます。
CAS-004-JPN問題集最新版のアクセス
「620問、30% ディスカウント、特別な割引コード:JPNshiken」
セキュリティ アナリストは、悪意のあるコードが Linux システムにダウンロードされたことを懸念しています。いくつかの調査の後、アナリストは、疑わしいコード部分がディスク ドライブ上で大量の入出力 (I/O) を実行していることを突き止めました。
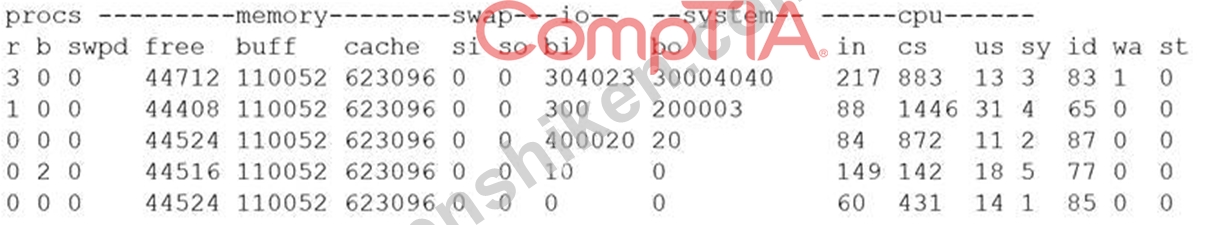
上記の出力に基づいて、アナリストは次のプロセス ID のどれから調査を開始できますか?

上記の出力に基づいて、アナリストは次のプロセス ID のどれから調査を開始できますか?
正解:D
The process ID 87 can be the starting point for an investigation of a possible buffer overflow attack, as it shows a high percentage of CPU utilization (99.7%) and a suspicious command name (graphic.linux_randomization.prg). A buffer overflow attack is a type of attack that exploits a vulnerability in an application or system that allows an attacker to write data beyond the allocated buffer size, potentially overwriting memory segments and executing malicious code. A high CPU utilization could indicate that the process is performing intensive or abnormal operations, such as a buffer overflow attack. A suspicious command name could indicate that the process is trying to disguise itself or evade detection, such as by mimicking a legitimate program or using random characters. The other process IDs do not show signs of a buffer overflow attack, as they have low CPU utilization and normal command names. Verified References:
https://www.comptia.org/blog/what-is-buffer-overflowhttps://partners.comptia.org/docs/default-source/resources
https://www.comptia.org/blog/what-is-buffer-overflowhttps://partners.comptia.org/docs/default-source/resources
- 質問一覧「221問」
- 質問1 ネットワーク防御の取り組み中に、レッド チームは次のレジスト
- 質問2 セキュリティ エンジニアはレガシー サーバーを評価しており、FT...
- 質問3 従業員のデバイスが報告されるまで 96 時間行方不明でした。従業...
- 質問4 SaaS クラウド ベンダーのリスクを管理および軽減する場合、クラ...
- 質問5 内部リソースの制約のため、管理チームは主任セキュリティ アー
- 質問6 脆弱性評価エンドポイントは、最新の調査結果のレポートを生成し
- 質問7 ある企業は、顧客のために大量のデータを BLOB ストレージでホス...
- 質問8 セキュリティ管理者は、侵害された暗号化キーがすべての VPN ト...
- 質問9 法執行当局は捜査が開始されたと組織に通知した。組織が最初にと
- 質問10 暗号化ソリューションを活用して使用中のデータを保護すると、デ
- 質問11 新しい銀行口座にアクセスするための顧客登録プロセスの一環とし
- 質問12 ディザスタ リカバリ チームは、前回のディザスタ リカバリ パラ...
- 質問13 セキュリティ アナリストは、ハッカーがいくつかのキーを発見し
- 質問14 セキュリティ エンジニアは、地域の配電サービスを提供するネッ
- 質問15 セキュリティアーキテクトは、秘密暗号キーの公開が疑われるもの
- 質問16 ある組織は知的財産データをオンプレミスから CSP に移動してお...
- 質問17 次のプロトコルのうち、PAN ネットワークの作成を可能にする低電...
- 質問18 組織は、リモート作業をサポートするために BYOD 標準を検討して...
- 質問19 組織は、次の目的で新しい ID およびアクセス管理アーキテクチャ...
- 質問20 開発チームは、PaaS 環境に格納された企業のバックエンド API に...
- 質問21 セキュリティ エンジニアは、次の要件を満たす新しい Web ベース...
- 質問22 サイバーセキュリティ アナリストは、潜在的なインシデントが発
- 質問23 ネットワーク アーキテクトは、すべてのローカル サイトを中央の...
- 質問24 サイバーアナリストは、提供された画像ファイルから PDF ファイ...
- 質問25 ある企業は、識別属性を追加せずに、独自の文書内に秘密裏に所有
- 質問26 最近、製薬会社がランサムウェアの被害を受けました。プロセス調
- 質問27 ソフトウェア開発会社は、ソーシャル メディア プラットフォーム...
- 質問28 セキュリティ アナリストがクライアントに代わって脆弱性評価を
- 質問29 最高情報責任者 (CIO) は、組織全体にエンタープライズ モビリテ...
- 質問30 クライアントがプロジェクトにスコープを追加しています。クライ
- 質問31 ある組織は、企業のモバイル デバイス ユーザーに対して、企業の...
- 質問32 セキュリティ アーキテクトは、来月開始される侵入テストの範囲
- 質問33 ランサムウェアは、大手金融機関の人事ファイル共有全体を暗号化
- 質問34 セキュリティ アナリストは、次の出力を確認しています。 (Exhib...
- 質問35 銀行のリスク委員会に最新の指標を提供する最高情報セキュリティ
- 質問36 セキュリティ エンジニアは、同社の人気のある Web アプリケーシ...
- 質問37 ヘルプ デスクの技術者は、ユーザーが昨夜 Internet Explorer か...
- 質問38 組織は、新しいオンライン デジタル バンクを展開しており、可用...
- 質問39 企業は、対象データの処理および保管の制約を定義するパートナー
- 質問40 アプリケーション開発者は、アプリケーションにサードパーティの
- 質問41 セキュリティ エンジニアはサイドチャネル攻撃の脅威を懸念して
- 質問42 セキュリティ アナリストは、ネットワーク管理者のワークステー
- 質問43 米国を拠点とする企業の不正調査に取り組んでいる法医学の専門家
- 質問44 ある企業は、CRM プラットフォーム全体をすべてのユーザーに一度...
- 質問45 デジタル トランスフォーメーションを実施中の企業は、CSP の回...
- 質問46 ある会社が新しいビデオカードをリリースしたところです。供給が
- 質問47 ある企業は、データベースに保存されているデータを隠すソリュー
- 質問48 組織マットが提供する SaaS ソリューションでは、最近、顧客デー...
- 質問49 米国のみを拠点とする顧客を持つ企業は、他国の開発者が自社の W...
- 質問50 時間を節約するために、新しい VPN ソリューションを開発してい...
- 質問51 ある医療企業は、データセンターの物理的能力とコンピューティン
- 質問52 企業の最高情報責任者は、現在のシステムのアーキテクチャに IDS...
- 質問53 災害後に企業が存続できなくなる可能性があることを示すものは次
- 質問54 ある銀行は、最新の脅威に対するセキュリティ対策を強化するため
- 質問55 製薬会社は最近、顧客向けの Web ポータルでセキュリティ違反を...
- 質問56 ある企業は、新しい人工知能ベースの分析 SaaS ソリューションを...
- 質問57 立法者に対する新しい要件により、政府のセキュリティ チームは
- 質問58 次のコントロールのうち、特権の乱用を主に検出するが、それを防
- 質問59 市場で競争したいCSPは、ビジネス獲得を目指して企業にアプロー...
- 質問60 最高情報セキュリティ責任者 (CISO) は、会社全体の反論 BCP/DR ...
- 質問61 企業のネットワーク上のホストが、SMB 経由で拡散していると思わ...
- 質問62 セキュリティ アナリストは、最近のデータ損失インシデントの原
- 質問63 法医学捜査官は、提出された記憶媒体(または証拠)から抽出され
- 質問64 サーバーが侵害された後、インシデント対応者はログ ファイルを
- 質問65 システム管理者には、コマンド アンド コントロール サーバーと...
- 質問66 システム管理者は、ネットワークに接続する前にホスト システム
- 質問67 ある企業は、ストレージ コストを節約するために、顧客の PII を...
- 質問68 企業は SSL インスペクションを実装しています。今後 6 か月の間...
- 質問69 新しい Web サーバーは、新しいセキュア バイ デザインの原則と ...
- 質問70 セキュリティ アナリストが、バッファ オーバーフロー攻撃の可能...
- 質問71 セキュリティ アナリストは、データベース管理者のワークステー
- 質問72 ある企業が最近、マルウェアに感染しました。根本原因の分析中。
- 質問73 重大な気象現象により、すべてのシステムが障害復旧サイトに正常
- 質問74 ある企業は、エクストラネット アプリケーションへのサプライヤ
- 質問75 セキュリティ チームは、組織を離れたスタッフ メンバーからの共...
- 質問76 脅威ハンティング チームは、ネットワーク内で発生する可能性の
- 質問77 不正な API キーの共有を防ぐために組織が実装する必要があるの...
- 質問78 セキュリティ アナリストは、組織のコンテナ化の概念を調査して
- 質問79 リスク戦略の一環として、企業はサイバーセキュリティ インシデ
- 質問80 ユーザーが企業のラップトップからインターネット バンキングの ...
- 質問81 セキュリティ アナリストは SIEM イベントをレビューしています...
- 質問82 若手開発者は、Advanced RISC Machine (ARM) CPU に対する新しい...
- 質問83 ソフトウェア開発会社は、そのソフトウェア バージョンを Web ポ...
- 質問84 セキュリティ エンジニアは、社内で開発された基幹業務ソフトウ
- 質問85 セキュリティ インシデントの後、ネットワーク セキュリティ エ...
- 質問86 DNP3 にとってセキュリティ上の懸念があるのは次のうちどれです...
- 質問87 次のうち、パスワードレス認証ソリューションを実装することの最
- 質問88 セキュリティ アナリストは、悪意のあるコードが Linux システム...
- 質問89 組織は、データをバックアップしてすぐに利用できるようにするこ
- 質問90 セキュリティ エンジニアは、関連データに前方機密性と認証され
- 質問91 地域と予算の制約により、組織のサテライト オフィスには、組織
- 質問92 モバイル アプリケーション開発者は、グローバルで拡張性の高い
- 質問93 会社の財務部門は、システム上の暗号化されていないファイルにデ
- 質問94 侵入テスターは、Windows サーバーでルート アクセス権を取得し...
- 質問95 サーバーレス コンピューティングを実装する場合、組織は引き続
- 質問96 ソフトウェア開発会社の管理者は、デジタル署名を使用して会社の
- 質問97 組織は、OT ネットワーク内のシステムの自動化機能を研究してい...
- 質問98 組織が ISO 27018 規格を満たすために必要なものは次のうちどれ...
- 質問99 あなたは、会社の特権ネットワークからの Nmap スキャン出力を解...
- 質問100 企業は、自社のワークロードを専らオンプレミスの IT インフラス...
- 質問101 最近のデータ侵害により、ある企業のストレージ環境全体に顧客デ
- 質問102 監査人は、保存されている文書をスキャンして機密テキストを見つ
- 質問103 セキュリティ アナリストは、ワークステーションからの代替アウ
- 質問104 多数の電子メールが報告されており、セキュリティ アナリストが
- 質問105 セキュリティ管理者は、組織をゼロトラスト アーキテクチャに移
- 質問106 CSP の観点から最も重要なクラウド固有のリスクは次のうちどれで...
- 質問107 捜査または訴訟中に証拠の検索と収集が含まれるプロセスは次のど
- 質問108 セキュリティ アナリストは、サード パーティの侵入テスターに...
- 質問109 セキュリティ アーキテクトは、分散した新しい従業員をサポート
- 質問110 開発者は、安全な外部向け Web アプリケーションを開発したいと...
- 質問111 自治体の部門がサードパーティのプロバイダーからテレメトリ デ
- 質問112 ソフトウェア ハウスが新しいアプリケーションを開発しています
- 質問113 攻撃チームは、新しいスマート カード システムで侵入テストを実...
- 質問114 ネットワーク チームは、会社の全従業員に安全なリモート アクセ...
- 質問115 組織は、最新の評価で特定されたリスクを修復または軽減するため
- 質問116 ネットワーク チームは、セキュリティ管理者に Web ブラウザで F...
- 質問117 セキュリティ エンジニアは、組織の機密データを保護するクラウ
- 質問118 会社 A は、会社 B と契約を結んでいます。契約の条件は、支払い...
- 質問119 大学は、独自のアイデンティティ管理システムを通じて、すべての
- 質問120 ある企業は、社内サーバーで実行されている Web アプリケーショ...
- 質問121 ある企業は、ホリデー シーズンの準備として、小売販売を管理す
- 質問122 セキュリティ アナリストは、企業のクラウド ログでネットワーク...
- 質問123 組織の既存のインフラストラクチャには、データセンター間のサイ
- 質問124 開発者は、可能な限り効率的かつ労働効率の高い方法で自動運転車
- 質問125 セキュリティ アーキテクトは、RDP の次の要件に対応するために...
- 質問126 小規模銀行は、次の要件に対処し、解決するためのさまざまな方法
- 質問127 セキュリティ アーキテクトは、次の提案されている企業ファイア
- 質問128 セキュリティ エンジニアは、会社のマルチホーム SFTP サーバー...
- 質問129 PCI DSS v3.4 に基づいて、ある特定のデータベース フィールドに...
- 質問130 セキュリティ アナリストは、次の脅威に対する修復を推奨する必
- 質問131 最高セキュリティ責任者 (CSO) は、セキュリティ チームに対し、...
- 質問132 多国籍組織がハッキングされ、インシデント対応チームのタイムリ
- 質問133 最高情報セキュリティ責任者 (CISO) は、企業の対応計画のあらゆ...
- 質問134 セキュリティ管理者は、セキュリティ実装ガイドラインに従ってア
- 質問135 セキュリティ アーキテクトは、データベース バックエンドを使用...
- 質問136 監査人は、Web アプリケーションからのログを確認して、インシデ...
- 質問137 最高情報セキュリティ責任者 (CISO) は、モバイル デバイスが会...
- 質問138 セキュリティ アーキテクトはセキュリティ ポリシーを更新し、2 ...
- 質問139 ある組織は最近、エンドポイント デバイス上の OS ブートローダ...
- 質問140 セキュリティ コンプライアンス要件では、機密データを処理する
- 質問141 ネットワーク管理者は、ラップトップを再起動しようとしているリ
- 質問142 企業は、管理された検出および応答サービスを実行する MSSP にア...
- 質問143 リモートから電話をかけてくる従業員を認証するには、企業のヘル
- 質問144 組織は、参照データを新しいシステムに組み込むためにレガシー
- 質問145 署名されたアプリケーションは、以下によってリスクを軽減します
- 質問146 最高情報責任者 (CIO) は、フォーマット パートナーシップを確立...
- 質問147 組織内のセキュリティ チームとビジネス ユニットの間の期待値を...
- 質問148 ある企業は最近 SIEM を導入し、ファイアウォール、ファイル サ...
- 質問149 会社 A が会社 B を買収しました。初期評価中に、両社は同じ SSO...
- 質問150 最高情報責任者 (CIO) は、システム管理者に、次の要件に基づい...
- 質問151 ある脆弱性アナリストが、社内で開発されたソフトウェアにゼロデ
- 質問152 セキュリティ アナリストは、次のアクティビティを示す多数の SI...
- 質問153 ある企業が最近 SaaS プロバイダーを買収し、顧客のエクスペリエ...
- 質問154 コストを節約するために、ある企業は低コストのプロバイダーを使
- 質問155 ユーザーは、最近ネットワークに追加された新しいクラウド アプ
- 質問156 企業は、接続文字列が確実に保護されるように、秘密キーと公開キ
- 質問157 攻撃者が発電サイトに侵入し、安全計装システムを無効にしました
- 質問158 会社 A が会社を買収しました。監査中に、セキュリティ エンジニ...
- 質問159 過去 1 年間の攻撃パターンを振り返ると、攻撃者は侵害を受けや...
- 質問160 ICS に出力する電力量を伝えるメッセージを制御するために暗号化...
- 質問161 ホスピタリティ企業は、顧客 PLL を含むデータ侵害を経験しまし...
- 質問162 セキュリティ アナリストには、CVE を識別するために確認して会...
- 質問163 複数のサードパーティ組織を使用してサービスを提供する大手銀行
- 質問164 IT 管理者が組織内のすべてのサーバーを調べていると、root アク...
- 質問165 エネルギー会社は、過去四半期に使用された天然ガスの平均圧力を
- 質問166 ある企業は、ミッション クリティカルなプロセスの運用に使用さ
- 質問167 アナリストは政府機関から IOC のリストを受け取りました。この...
- 質問168 セキュリティ アーキテクトは、リモート ワーカーが高度に分散し...
- 質問169 ストリーミング コンテンツへの継続的な可用性を必要とする大手
- 質問170 セキュリティ エンジニアは、企業ネットワークからのセキュリテ
- 質問171 セキュリティアナリストは、リスク登録簿に重要な情報を提供する
- 質問172 次のうち、平文を知らなくても暗号文内のデータの計算と分析を可
- 質問173 電子商取引 Web サイトの一部のエンド ユーザーは、ページの閲覧...
- 質問174 衛星通信 ISP は、非推奨のハードウェアとソフトウェアを使用し...
- 質問175 CI/CD パイプラインでは、コードに欠陥と脆弱性がほぼゼロである...
- 質問176 リスク担当者がリスク評価を行う前にセキュリティ境界を決定する
- 質問177 ある企業のセキュリティ エンジニアが、新製品の市場投入で企業
- 質問178 金融部門の企業は、電子メールを介してかなりの数の顧客取引要求
- 質問179 企業は、住宅ローン承認の要求を処理するために、EU に居住する...
- 質問180 組織は、以下を含む契約文書を必要とします * 対象となるものの...
- 質問181 ある会社は、会社所有の電話からモバイル デバイスの BYOD 戦略...
- 質問182 ある企業は、自社の知的財産を盗難から保護したいと考えています
- 質問183 ある組織は、電子商取引サイトをクラウドで実行しています。この
- 質問184 予算の制約のため、ある組織は、CVSS に従って高および重大と評...
- 質問185 ある組織が最近、ランサムウェア攻撃を受けました。セキュリティ
- 質問186 プライベート暗号化/復号化ファイルを安全に保管するためにサー
- 質問187 ある銀行は、セキュリティ アーキテクトと協力して、データベー
- 質問188 e コマース企業はオンプレミスで Web サーバーを実行しており、...
- 質問189 企業は、セキュリティ管理の有効性を数値化して伝達したいと考え
- 質問190 ある組織がリスク評価を実施したところ、従業員の 50% 未満しか...
- 質問191 会社の最高情報セキュリティ責任者は、会社が提案したクラウドへ
- 質問192 システム侵入テスト中に、セキュリティ エンジニアは標準ユーザ
- 質問193 小さな会社が最近、軍事計画のプロトタイプ技術を開発しました。
- 質問194 捜査または訴訟中に証拠の検索と収集が含まれるプロセスは次のど
- 質問195 エンジニアリング チームは、特殊な在庫管理目的に使用するモバ
- 質問196 セキュリティ エンジニアは、会社の Web サイトでユーザーが次の...
- 質問197 組織は、会社所有の資産がネットワーク外にある場合、または VPN...
- 質問198 ある組織は、PKI を実装することで、より堅牢なセキュリティ対策...
- 質問199 金融機関は、新しく作成されたアカウントと機密情報のリストを毎
- 質問200 世界的な拠点を持つ地元の大学は、Web サイトと関連システムの全...
- 質問201 セキュリティ アーキテクトは、環境内で重要なセキュリティ機能
- 質問202 ユーザーは、Web サーバーにアクセスできないと主張しています。...
- 質問203 世界的メーカーの主任セキュリティ アナリストは、ICS ネットワ...
- 質問204 セキュリティ管理者は、電子メールのエンベロープ内の潜在的な偽
- 質問205 ISP は、一部の顧客から、ISP の Web サイトの URL の一部を入力...
- 質問206 開発者は、プログラムの各モジュールの整合性を維持し、悪意のあ
- 質問207 サイバーセキュリティ アナリストは、企業が改善された電子メー
- 質問208 組織のハント チームは、永続的な脅威が存在し、企業ネットワー
- 質問209 会社のセキュリティ エンジニアが職場に到着すると、次のシナリ
- 質問210 (Exhibit) 組織は災害復旧と業務継続を計画しています。 説明書 ...
- 質問211 ある企業は、インフラストラクチャ全体を更新中です。 この企業
- 質問212 次の用語のうち、CASB またはサードパーティ エンティティへの暗...
- 質問213 あるソフトウェア会社は、以下を必要とする暗号でデータを暗号化
- 質問214 セキュリティ アナリストは、最近の侵入テストから提供されたデ
- 質問215 セキュリティ エンジニアは、次の要件を満たすためにネットワー
- 質問216 組織は、パスポート番号などの機密 Pll および ID 情報を処理す...
- 質問217 セキュリティ エンジニアは、組織の現在のソフトウェア開発プラ
- 質問218 オンライン小売業者の最高経営責任者は、売上の突然の減少に気づ
- 質問219 小さな会社は、運用コストを削減する必要があります。ベンダーは
- 質問220 レコードレベルの暗号化が一般的に使用されるのは次のうちどれで
- 質問221 新人開発者は、高度な RISC マシン (ARM) CPU に対する新しいマ...

