- ホーム
- Microsoft
- AZ-220J - Microsoft Azure IoT Developer (AZ-220日本語版)
- Microsoft.AZ-220J.v2023-08-11.q82
- 質問21
有効的なAZ-220J問題集はJPNTest.com提供され、AZ-220J試験に合格することに役に立ちます!JPNTest.comは今最新AZ-220J試験問題集を提供します。JPNTest.com AZ-220J試験問題集はもう更新されました。ここでAZ-220J問題集のテストエンジンを手に入れます。
AZ-220J問題集最新版のアクセス
「205問、30% ディスカウント、特別な割引コード:JPNshiken」
Hub1という名前のAzureIoTハブと、CA1という名前のルート証明機関(CA)があります。 Hub1は、X.509証明書デバイス認証を使用するように構成されています。
あなたとカスタム製造パートナーは、所有フローの証明を完成させます。
カスタム製造パートナーによって製造されたIoTデバイスを展開することを計画しています。各デバイスには、中間CAによって生成された証明書があります。デバイスは、パートナーによって署名されたデバイス証明書を使用して認証されます。
カスタムデバイスがHub1に正常に接続できることを確認する必要があります。
順番に実行する必要がある3つのアクションはどれですか?回答するには、適切なアクションをアクションのリストから回答領域に移動し、正しい順序に並べます。

あなたとカスタム製造パートナーは、所有フローの証明を完成させます。
カスタム製造パートナーによって製造されたIoTデバイスを展開することを計画しています。各デバイスには、中間CAによって生成された証明書があります。デバイスは、パートナーによって署名されたデバイス証明書を使用して認証されます。
カスタムデバイスがHub1に正常に接続できることを確認する必要があります。
順番に実行する必要がある3つのアクションはどれですか?回答するには、適切なアクションをアクションのリストから回答領域に移動し、正しい順序に並べます。

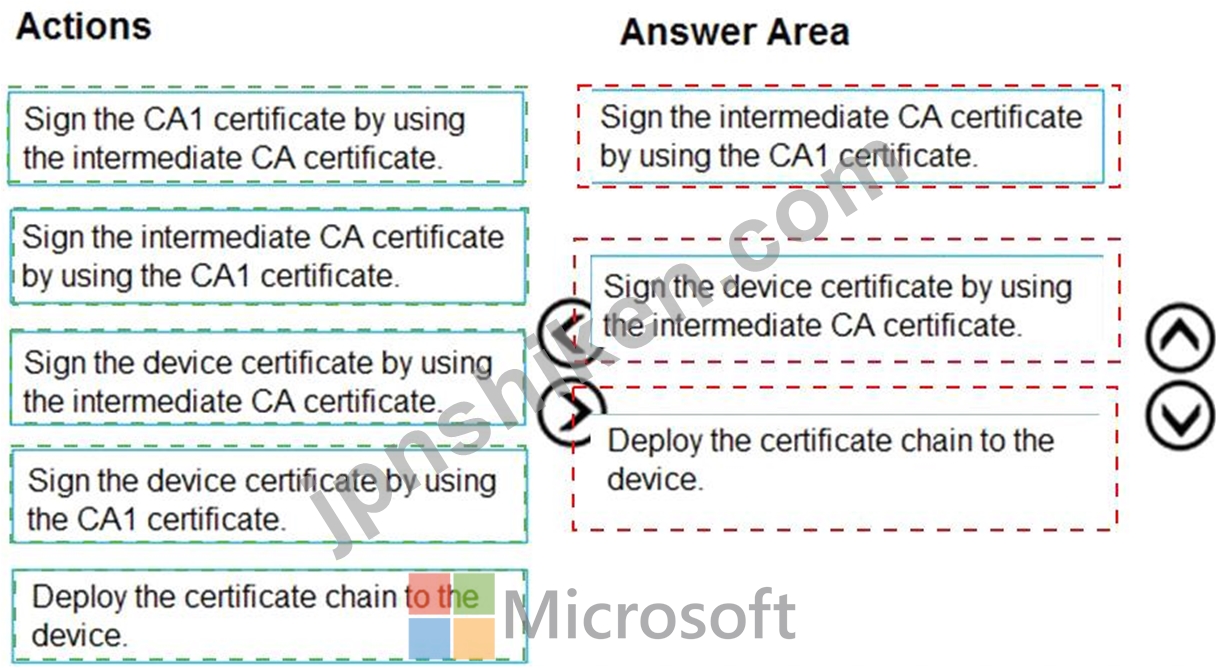
正解:
Explanation
Graphical user interface, text, application, chat or text message Description automatically generated

Box 1: Sign the intermediate CA certificate by using the CA1 certificate.
X.509 certificates are typically arranged in a certificate chain of trust in which each certificate in the chain is signed by the private key of the next higher certificate, and so on, terminating in a self-signed root certificate.
This arrangement establishes a delegated chain of trust from the root certificate generated by a trusted root certificate authority (CA) down through each intermediate CA to the end-entity "leaf" certificate installed on a device.
Box 2: Sign the device certificate by using the intermediate CA
An intermediate certificate is an X.509 certificate, which has been signed by the root certificate (or by another intermediate certificate with the root certificate in its chain). The last intermediate certificate in a chain is used to sign the leaf certificate. An intermediate certificate can also be referred to as an intermediate CA certificate.
Box 3: Deploy the certificate chain to the device.
The leaf certificate, or end-entity certificate, identifies the certificate holder. It has the root certificate in its certificate chain as well as zero or more intermediate certificates. The leaf certificate is not used to sign any other certificates. It uniquely identifies the device to the provisioning service and is sometimes referred to as the device certificate. During authentication, the device uses the private key associated with this certificate to respond to a proof of possession challenge from the service.
Reference:
https://docs.microsoft.com/en-us/azure/iot-dps/concepts-x509-attestation
- 質問一覧「82問」
- 質問1 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問2 Azure サブスクリプションがある Azure Resource Manager (ARM) ...
- 質問3 次の構成のIoTデバイスがあります。 ハードウェア:Raspberry Pi...
- 質問4 iothub1にdevice1という名前の新しいIoTデバイスを作成します。 ...
- 質問5 地理的に異なる場所にある複数のAzureIoTハブと単一のデバイスプ...
- 質問6 Azure IoT Edge デプロイを含む Azure ソリューションがあります...
- 質問7 Azure IoTCentralアプリケーションを開発しています。 新しいカ...
- 質問8 Azure IoTソリューションでAzure Security Centerを使用します。...
- 質問9 デバイスプロビジョニングサービスインスタンスを使用してAzure ...
- 質問10 Azure IoTハブをデプロイします。 IoTハブがデバイスからメッセ...
- 質問11 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問12 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問13 既存のAzure IoTハブがあります。 接続されたデバイスで長時間実...
- 質問14 Azure IoTハブがあります。 次の表に示すように、3種類のIoTデバ...
- 質問15 Azure IoTハブと、Device1およびDevice2という名前の2つのAzure ...
- 質問16 IoT ハブからのデバイス テレメトリ データを受け入れるようにデ...
- 質問17 500 台のデバイスが登録されている Azure IoT ハブがあります。 ...
- 質問18 Azure IoTEdgeソリューションがあります。 IoTセキュリティエー...
- 質問19 Azure IoTハブを使用する概念実証(POC)を計画しています。 Cer...
- 質問20 Azure IoTハブに接続する10,000のIoTデバイスがあります。デバイ...
- 質問21 Hub1という名前のAzureIoTハブと、CA1という名前のルート証明機...
- 質問22 あなたの会社は、Azure IoT Hubを使用する新しいカメラセキュリ...
- 質問23 Azure Digital Twins クエリを作成しています。 Twin1 の ID を...
- 質問24 Azure IoT Edgeデバイスがあります。 コンテナーレジストリへの...
- 質問25 次のクエリを使用する Asjob1 という名前の Azure Stream Analyt...
- 質問26 Azure Security Center for IoTを有効にします。 デバイスをAzur...
- 質問27 Azure IoTEdgeソリューションのモジュールを開発することを計画...
- 質問28 次の図に示すように、Azure IoT ハブを作成します。 (Exhibit) ...
- 質問29 既存のAzureIoTハブがあります。 IoT Hubジョブを使用して、接続...
- 質問30 Hub1という名前のAzure IoTハブに接続する10個のIoTデバイスがあ...
- 質問31 標準階層のAzure IoTハブとIoTデバイスを含むAzure IoTソリュー...
- 質問32 デバイスプロビジョニングサービスインスタンスを含むAzure IoT ...
- 質問33 既存のAzure IoTハブがあります。 物理IoTデバイスをIoTハブに接...
- 質問34 あなたの会社はカスタムモジュールを開発し、そのモジュールをLi...
- 質問35 Azure 10T ハブと I0T デバイスがあります。 IoT デバイスがジオ...
- 質問36 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問37 次の表に示す Azure IoT ハブと Azure IoT Edge ゲートウェイを...
- 質問38 デバイスプロビジョニングサービスインスタンスを使用するAzureI...
- 質問39 メッセージエンリッチメントを使用して、報告された温度がクリテ
- 質問40 Azure IoT ソリューションがあります。 X.509 自己署名証明書を...
- 質問41 Hub1という名前のAzureIoTハブに接続する100台のデバイスがあり...
- 質問42 Azure IoTCentralアプリケーションがあります。 Oven1という名前...
- 質問43 POV要件を満たすには、テレメトリメッセージの形式を推奨する必...
- 質問44 パイロット要件を満たすには、ソリューションにTime Series Insi...
- 質問45 Hub1445という名前のAzure IoTハブにストリーミングデータソース...
- 質問46 RG1という名前のリソースグループを含むAzureサブスクリプション...
- 質問47 Edge1という名前のAzureIoTEdgeデバイスがあります。 モジュール...
- 質問48 標準階層のAzure IoTハブのデプロイを計画しています。 スケジュ...
- 質問49 POV 要件を満たすように Stream Analytics を構成する必要があり...
- 質問50 POVフェーズでは、IoT Hubからのテレメトリがホットパスへのフロ...
- 質問51 AzureIoTハブに接続するIoTデバイスがあります。 IoT Hubから、...
- 質問52 あなたは海運会社向けのAzureIoTソリューションを開発しています...
- 質問53 次の図に示すように、モジュールがトラフィックをルーティングす
- 質問54 AzureIoTハブへのデバイスの接続とAzureIoTハブからの切断のトラ...
- 質問55 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問56 Hub1 という名前の Azure IoT ハブと tsi1 という名前の Azure T...
- 質問57 Azure Time Series Insightsのインスタンスと、IoTデバイスから...
- 質問58 Hub1 という名前の Azure IoT ハブと 20 個の IoT デバイスを含...
- 質問59 Hub1 という名前の Azure IoT ハブと、次の表に示す IoT デバイ...
- 質問60 プロトタイプから本番環境に移行するAzure IoTハブがあります。 ...
- 質問61 hub1 という名前の Azure IoT ハブと 5 つの IoT デバイスがあり...
- 質問62 Azure IoTCentralアプリケーションがあります。 最初にデバイス...
- 質問63 次の表に示すデバイスがあります。 (Exhibit) Azure IoTソリュー...
- 質問64 AzureIoTハブと温度を監視する15,000台のIoTデバイスがあります...
- 質問65 Azure IoTハブのデプロイを計画しています。 IoTハブは以下をサ...
- 質問66 AzureIoTソリューションがあります。 デジタルツインモデルを作...
- 質問67 contoso-hub.azure-devices.net というホスト名を持つ Azure IoT...
- 質問68 複数のIoTEdgeデバイスを含むAzureIoTEdgeソリューションを展開...
- 質問69 接続の問題の原因を特定するにはどうすればよいですか?
- 質問70 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問71 Azure IoT ハブと 100 個の IoT デバイスを含む Azure サブスク...
- 質問72 IoTデバイス用に次のデバイスツインがあります。 (Exhibit) 次の...
- 質問73 複数のAzure IoTハブを含むAzure IoTソリューションがあります。...
- 質問74 AzureIoTハブがあります。 Azure EventGridを使用してIoTHubイベ...
- 質問75 Windows 10 IoT Enterpriseを実行する新しいデバイスにAzure IoT...
- 質問76 Streaming Analyticsの要件を満たすには、GROUP BY句をどのよう...
- 質問77 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問78 IoTデバイスからメッセージを受信するAzureIoTハブがあります。...
- 質問79 Sensors.csvという名前のCSVファイルにデータを収集するIoTデバ...
- 質問80 Azure IoT ハブと 3 つの Azure IoT Edge デバイスがあります。...
- 質問81 AzureIoTハブと100台のAzureIoTEdgeデバイスを含むAzureIoTソリ...
- 質問82 追加の処理のために、Azure DigitalTwinsのイベントをダウンスト...

