- ホーム
- CompTIA
- SY0-601-JPN - CompTIA Security+ Certification Exam (SY0-601日本語版)
- CompTIA.SY0-601-JPN.v2024-01-16.q299
- 質問108
有効的なSY0-601-JPN問題集はJPNTest.com提供され、SY0-601-JPN試験に合格することに役に立ちます!JPNTest.comは今最新SY0-601-JPN試験問題集を提供します。JPNTest.com SY0-601-JPN試験問題集はもう更新されました。ここでSY0-601-JPN問題集のテストエンジンを手に入れます。
SY0-601-JPN問題集最新版のアクセス
「1061問、30% ディスカウント、特別な割引コード:JPNshiken」
セキュリティ アナリストは、脅威ハンティング演習を実行しているときに、ユーザーが表示名を変更したときにアプリケーションで異常な動作が発生していることに気付きました。セキュリティ アナリストは静的コード分析を実行することを決定し、次の疑似コードを受け取ります。
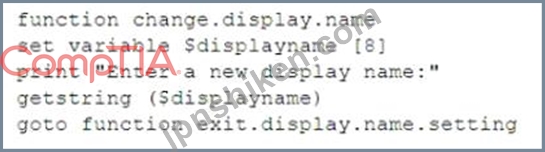
次の攻撃タイプのうち、異常な動作の根本原因を最もよく説明しているものはどれですか?

次の攻撃タイプのうち、異常な動作の根本原因を最もよく説明しているものはどれですか?
正解:D
Explanation
SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input12. A SQL injection attack consists of insertion or
"injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system3.
According to the pseudocode given in the question, the application takes a user input for display name and concatenates it with a SQL query to update the user's profile. This is a vulnerable practice that allows an attacker to inject malicious SQL code into the query and execute it on the database. For example, an attacker could enter something like this as their display name:
John'; DROP TABLE users; --
This would result in the following SQL query being executed:
UPDATE profile SET displayname = 'John'; DROP TABLE users; --' WHERE userid = 1; The semicolon (;) terminates the original update statement and starts a new one that drops the users table. The double dash (-) comments out the rest of the query. This would cause a catastrophic loss of data for the application.
SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input12. A SQL injection attack consists of insertion or
"injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system3.
According to the pseudocode given in the question, the application takes a user input for display name and concatenates it with a SQL query to update the user's profile. This is a vulnerable practice that allows an attacker to inject malicious SQL code into the query and execute it on the database. For example, an attacker could enter something like this as their display name:
John'; DROP TABLE users; --
This would result in the following SQL query being executed:
UPDATE profile SET displayname = 'John'; DROP TABLE users; --' WHERE userid = 1; The semicolon (;) terminates the original update statement and starts a new one that drops the users table. The double dash (-) comments out the rest of the query. This would cause a catastrophic loss of data for the application.
- 質問一覧「299問」
- 質問1 ポート 80 経由で会社のデータを盗んでいるハッカーを検出するた...
- 質問2 セキュリティ エンジニアは、重要ではないアプリケーションが侵
- 質問3 次の環境のうち、ハードウェアとソフトウェアの両方のレベルでシ
- 質問4 セキュリティ アナリストは、会社の最高経営責任者 (CEO) に向け...
- 質問5 監査により、重要なアプリケーションの開発環境で Pll が利用さ...
- 質問6 セキュリティ アナリストは、新しいデバイスの導入を強化する際
- 質問7 次のうち、潜在的な脆弱性に対処するために定期的に更新する必要
- 質問8 企業は現在、会社所有のデバイスへのログインにパスワードを使用
- 質問9 大規模なグローバル企業の技術部門は、本社ビルの Wi-Fi ネット...
- 質問10 否認防止を実装する際に、セキュリティ エンジニアが利用する暗
- 質問11 セキュリティ アナリストは Web サーバー ログの出力を確認し、...
- 質問12 最近の侵入テスト中に、テスターは誰もいない会議室のイーサネッ
- 質問13 企業は事業継続戦略を策定しており、中断が発生した場合に事業を
- 質問14 組織は、個々の AV からのイベントを関連付けることが困難です。...
- 質問15 セキュリティ アナリストは、会社用に新しい WiFi ネットワーク...
- 質問16 会社のヘルプ デスクには、ワイヤレス ネットワークがダウンし、...
- 質問17 セキュリティ アナリストは、異常な量のトラフィックがネットワ
- 質問18 セキュリティ管理者は最近、内部 CA を使用してパブリック アプ...
- 質問19 非常に機密性の高いプロジェクトでこれらの製品の使用を検討する
- 質問20 ユーザーがブラウザの拡張機能をダウンロードしたところ、その後
- 質問21 /etc/shadow ファイルを確認しているときに、セキュリティ管理者...
- 質問22 大規模産業システムのスマート発電機はシステムのステータスを監
- 質問23 セキュリティ インシデント中に、セキュリティ運用チームは悪意
- 質問24 ユーザーは携帯電話で銀行口座の詳細を尋ねる SMS を受信しまし...
- 質問25 金融機関は、顧客データをクラウドに保存しながら、暗号化された
- 質問26 組織は、不満を抱いた従業員がファイルをアップロードして大量の
- 質問27 悪意のある人物が、資金にアクセスするために電話で財務情報を提
- 質問28 セキュリティ アナリストが企業でのマルウェア インシデントを調...
- 質問29 ある企業が、クラウド バックアップ、VM の弾力性、安全なネット...
- 質問30 セキュリティ管理者が新しい Web サーバーをインストールしまし...
- 質問31 セキュリティ アナリストは、ネットワークが 1 日の特定の時間帯...
- 質問32 最近、ある企業でデータ侵害が発生しましたが、その情報源は公共
- 質問33 セキュリティ アナリストは、2 週間休暇をとっているユーザーが...
- 質問34 セキュリティ研究者は、組織の機密ユーザー データが Web サイト...
- 質問35 アナリストは、管理チーム向けのセキュリティ レポートを生成し
- 質問36 ある企業は、従業員がモバイル デバイス上のオペレーティング シ...
- 質問37 サーバー管理者は、多数の仮想サーバー間でコンピューティング
- 質問38 セキュリティ チームは、最近の電力消費の過負荷の原因は、ネッ
- 質問39 最近ローカル サーバーがクラッシュしたため、チームはバックア
- 質問40 次の条件のうち、データ主権に影響を与えるのはどれですか?
- 質問41 最近、Windows システムの SMB プロトコルに新たな脆弱性が発見...
- 質問42 セキュリティ運用技術者は、/vax/messages という名前のログを検...
- 質問43 顧客の PLL を含むファイルを誤って電子メールで送信した従業員...
- 質問44 地理的に分散した 2 つのデータ センターを持つ大規模な銀行は、...
- 質問45 次のうち、資産を標的とする脅威によって予想される年間の総損失
- 質問46 金融アナリストは、クライアントから機密情報を含む電子メールを
- 質問47 次のうち、組織がクラウド プロバイダーの読み取り使用可能なア
- 質問48 セキュリティ アナリストは、企業 LAN からダーク Web に向けて...
- 質問49 ペネトレーション テスターは、以前にキャプチャしたネットワー
- 質問50 セキュリティ アナリストは、コーディングのベスト プラクティス...
- 質問51 次のうち、研究者が脆弱性を発見したことを補償する手法を説明し
- 質問52 ネットワークに接続する前に、セキュリティ デバイスで最初に対
- 質問53 /etc/shadow ディレクトリに保存されているファイルを強化するの...
- 質問54 教訓フェーズの一環として、SOC は以前のインシデントが再び発生...
- 質問55 封じ込め前に行われるインシデント対応手順は次のうちどれですか
- 質問56 ビジネス プロセスやシステムに影響を与える可能性のある壊滅的
- 質問57 大手衣料品会社は最近、大量の専有情報を失いました。セキュリテ
- 質問58 組織の最高セキュリティ責任者 (CSO) は、インシデント対応計画...
- 質問59 ある会社は、データ漏えいリスクを対象とした情報セキュリティ対
- 質問60 攻撃者は、標的の被害者がアクセスすることがわかっている Web ...
- 質問61 セキュリティ アナリストは、ポリシーを適用して MDM インフラス...
- 質問62 次のうち、物理的な盗難のリスクを軽減するための予防的、発見的
- 質問63 新しい脆弱性により、システムからのデータの不正な移動を可能に
- 質問64 会社のヘルプ デスクは、Mimikatz がリモート システム上で実行...
- 質問65 最近、ある組織が ISO 27001 認証を取得しました。次のうち、こ...
- 質問66 組織はデータ管理の役割と責任の概要を説明しています。データの
- 質問67 地元のコーヒー ショップで作業しているときに、ユーザーがワイ
- 質問68 システム アナリストは、特定の国のネットワーク ブロックに属す...
- 質問69 フォレンジック調査中に整合性を証明するのに役立つテストは次の
- 質問70 次のソーシャル エンジニアリング攻撃のうち、受信者を誤解させ
- 質問71 企業は、スケーラブルなクラウド インフラストラクチャを維持す
- 質問72 組織内のリモート ワーカーは、アプリケーションがローカルにイ
- 質問73 ある大規模な多国籍組織のセキュリティ アーキテクトは、複数の
- 質問74 ローカル オフィスの WiFi スキャンが実行された後、不明な無線...
- 質問75 サイバーセキュリティ アナリストが Web サーバー側のログ ファ...
- 質問76 障害が発生した場合に組織がデータを回復する時点を特定するのは
- 質問77 ユーザーは、内部ワークステーションからアプリケーションへのア
- 質問78 監査レポートは、会社リソースへのアクセスに対する不審な試みが
- 質問79 組織は、管理者/ルートの資格情報とサービス アカウントに対して...
- 質問80 Web アプリケーションの安全なコーディング手法を改善したいと考...
- 質問81 セキュリティ エンジニアは、SSL を介した悪意のある Web リクエ...
- 質問82 小規模な地元企業がランサムウェア攻撃を受けました。この会社に
- 質問83 会社 A のサイバーセキュリティ アナリストは、3,000 マイル (4....
- 質問84 次のコンポーネントのうち、受信インターネット トラフィックを
- 質問85 最高経営責任者は、戦略的ベンダーとの新しいパートナーシップを
- 質問86 脆弱性が発見されましたが、その脆弱性に対処する既知のパッチは
- 質問87 ある企業は、インターネットに接続された Web サイトに PKI を展...
- 質問88 次のうち、指紋リーダーを使用しているオンボーディングに成功し
- 質問89 最近、大手小売店のネットワークが侵害されました。そしてこのニ
- 質問90 セキュリティ エンジニアは、SSL を介した悪意のある Web リクエ...
- 質問91 ネットワーク アナリストが、僻地にあるホーム オフィス用のワイ...
- 質問92 VoIP 関連の一般的な脆弱性は次のうちどれですか? (2 つ選択して...
- 質問93 ある組織は、インシデント発生後の損傷を修復しています。次のど
- 質問94 ある組織は、インシデント発生後の損害の修復を行っています。次
- 質問95 デスクトップ サポート技術者が最近、新しいドキュメント スキャ...
- 質問96 ネットワーク管理者は、サーバー ファームのログの順序を決定す
- 質問97 ベンダー サポートが期限切れになり、すぐに交換できるシステム
- 質問98 セキュリティ管理者は、UDP ポート 514 を使用して、セキュリテ...
- 質問99 組織がインシデント対応プロセスを改善するために使用すべき演習
- 質問100 最高情報セキュリティ責任者 (CISO) は、従業員がオファーに参加...
- 質問101 最高情報セキュリティ責任者 (CISO) は、管理チームへの報告書の...
- 質問102 最高情報セキュリティ責任者 (CISO) は、会社の新しい ERP シス...
- 質問103 セキュリティ アナリストは、スマートフォン全体にセキュリティ
- 質問104 セキュリティ アナリストが会社の認証ログを確認し、複数の認証
- 質問105 次のうち、保護された領域へのアクセスを取得するときに許可され
- 質問106 セキュリティ アナリストは、ネットワーク デバイスとリモート ...
- 質問107 次のうち、パブリック クラウドでのアプリケーションのヘスティ
- 質問108 セキュリティ アナリストは、脅威ハンティング演習を実行してい
- 質問109 セキュリティ研究者が攻撃者のインフラストラクチャと TTP を使...
- 質問110 フォレンジック調査中に否認防止を実現するものは次のうちどれで
- 質問111 従業員は、 Updates という名前の通常とは異なるファイルが添付...
- 質問112 制限エリアへのアクセスを取得するための対話型プロセスの悪用に
- 質問113 次のうち、固定長のビットで動作する暗号化の概念はどれですか?
- 質問114 組織は、退職した従業員による知的財産の盗難を懸念しています。
- 質問115 セキュリティ アナリストは、組織の 70 レベルの脆弱性を経営陣...
- 質問116 現在の秘密鍵が侵害された場合、すべての履歴データの復号化に使
- 質問117 攻撃者は、デジタル署名されたドキュメントを気付かれない別のバ
- 質問118 複数のオンプレミスのセキュリティ ソリューションがクラウドに
- 質問119 脆弱性の重大度を判断する場合、次のどれを使用するのが最適です
- 質問120 管理者は、DHCP、Web ページ、および SFTP にのみアクセスし、特...
- 質問121 システム管理者は、社内のすべてのサーバーを監査して、最低限の
- 質問122 最高情報責任者は、従業員が会社支給のラップトップを使用してネ
- 質問123 ポート 80 経由で企業データを盗むハッカーを検出するために使用...
- 質問124 このアラートは、攻撃者が Web フォームのテキスト ボックスに何...
- 質問125 セキュリティ管理者は、サーバー上で不要なサービスが実行されて
- 質問126 いくつかの大学が共同研究プロジェクトに参加しており、コンピュ
- 質問127 最高情報責任者は、従業員が会社支給のラップトップを使用してネ
- 質問128 企業が新しいベンダーの継続的なセキュリティの成熟度を監視する
- 質問129 最高情報責任者は、電子メールに記載されているアカウントに 20,...
- 質問130 脆弱性の重大度を定量的に測定するために使用されるのは次のうち
- 質問131 ある企業は、訪問者がインターネットにアクセスできるように、ゲ
- 質問132 ヘルプ デスクの技術者は、最高情報責任者 (C/O) からドキュメン...
- 質問133 組織の利害関係者は、インシデントを常に認識し、ステータスの変
- 質問134 ある製造会社には、ソフトウェアの互換性の問題により、新しい O...
- 質問135 ネットワーク エンジニアは、同じスイッチ上にある複数の LAN 接...
- 質問136 ソフトウェア会社は、可能な限り早い段階でソフトウェアの脆弱性
- 質問137 ユーザーが、企業のラップトップの使用に関する問題を報告してい
- 質問138 セキュリティ管理者は、外部パートナーに内部ネットワークへの安
- 質問139 ファイアウォール構成のトラブルシューティング中に、技術者は「
- 質問140 バックアップ オペレータは、実稼働システムに影響を与えずに、
- 質問141 組織の最高情報セキュリティ責任者は、バックアップが適切に維持
- 質問142 ユーザーが財務部門から要求された税務書類をアップロードしよう
- 質問143 企業はログを一元管理してベースラインを作成し、セキュリティ
- 質問144 組織は、EAR のクライアント側およびサーバー側の証明書の使用か...
- 質問145 年次情報セキュリティ評価により、同社が使用している古い強化基
- 質問146 セキュリティインシデントが解決されました次のベストのうち、イ
- 質問147 データセンターの長期停止により Web ベースの販売に影響が出た...
- 質問148 エンジニアは、クラウド環境で Web サーバーのクラスターへのト...
- 質問149 システム エンジニアが、生産用の新しいシステムを構築していま
- 質問150 最高セキュリティ責任者 (CSO) は、クラウドベースのサービスが...
- 質問151 従業員は、モバイル デバイスで複数のメッセージを受信しました
- 質問152 次のうち、企業でより一般的になりつつある新しい 1CS デバイス...
- 質問153 セキュリティ アナリストは現在、アクティブなサイバー インシデ...
- 質問154 セキュリティ管理者は、組織の電子メール システムを介した攻撃
- 質問155 ある企業は、Tier 0 および Tier 1 システムへの管理者権限が必...
- 質問156 セキュリティ チームは、企業ネットワークの IP 空間から著作権...
- 質問157 ある企業は、リスク登録簿に記載されている項目に対処するために
- 質問158 ビル管理者は、勤務時間外にオフィスに出入りする人々を懸念して
- 質問159 セキュリティ管理者は、すべてのクラウド サーバーに、脆弱性ス
- 質問160 従業員の会社アカウントがデータ侵害に使用された 従業員へのイ
- 質問161 調査中に、インシデント対応チームは、複数の管理者アカウントが
- 質問162 ある会社は、個人が車を運転して建物に侵入することを懸念してい
- 質問163 セキュリティ エンジニアは、悪意のある攻撃者によるプロトコル
- 質問164 ある金融機関は、顧客データをクラウドに保存したいと考えていま
- 質問165 セキュリティ エンジニアは、ビジネス パートナーにファイルを送...
- 質問166 セキュリティ管理者は、ファイル サーバーからバックアップ スト...
- 質問167 下級人事管理者は、従業員に関するデータを収集して、新会社の表
- 質問168 ある企業は最近、認証インフラストラクチャをアップグレードし、
- 質問169 次のうち、資格証明付きスキャンで識別される可能性が最も高く、
- 質問170 ハードウェアとソフトウェアのインベントリ、脆弱性管理、および
- 質問171 従業員が誤って企業システムにマルウェアをインストールすること
- 質問172 ヘルプ デスクは、コア ネットワーク サービスにアクセスできな...
- 質問173 アナリストは、ターゲットがワームを含む添付ファイルを開いた電
- 質問174 ある会社は、一般向けの e コマース Web サイトを所有しています...
- 質問175 セキュリティアーキテクトは、機密データを大画面に表示できるワ
- 質問176 ハードウェア インシデントの後、問題を修正するために予定外の
- 質問177 応答時間、エスカレーション ポイント、パフォーマンス指標を定
- 質問178 世界的な製造会社が電子メール アカウントの侵害に遭遇していま
- 質問179 ある組織の事務所が自然災害により破壊されたため、その組織は現
- 質問180 ユーザーが Web ベースのアプリケーションをロードしようとしま...
- 質問181 動的アプリケーション脆弱性スキャンにより、Web フォームを使用...
- 質問182 Web サーバーのログには 200 万行が含まれます。セキュリティ ア...
- 質問183 ある企業は BYOD ポリシーを採用しており、ユーザー デバイス上...
- 質問184 ある組織は、セキュリティ体制に対する攻撃をシミュレートするた
- 質問185 セキュリティ アナリストは、午前 2 時から午前 4 時の間に外部 ...
- 質問186 悪意のあるドメインへの複数のビーコン アクティビティが確認さ
- 質問187 セキュリティ アナリストは、ワークステーションと会社のサーバ
- 質問188 大手製造会社が内部インフラストラクチャを更新し、OAuth アプリ...
- 質問189 アナリストは、複数のホストに対する複数のアラートを使用して調
- 質問190 最近、会社が侵害されました。同社の新しいサイバーセキュリティ
- 質問191 次の脆弱性のうち、攻撃者が悪用するのはどれですか? 実行パスを...
- 質問192 研究開発事業部門の従業員は広範なトレーニングを受け、企業デー
- 質問193 次のうち、侵入テストの演習中に審判として機能するチームを最も
- 質問194 特定のファイル セットの保護タイプと分類タイプの定義を担当す
- 質問195 次のうち、初期構成の一部として新しいネットワーク デバイスに
- 質問196 セキュリティ アナリストが SIEM からのアラートに対応していま...
- 質問197 技術者は、ネットワークを強化しながらインターネットへの Web ...
- 質問198 次の環境のうち、通常、現在のバージョンの構成とコードをホスト
- 質問199 コンテナ化されたアプリケーション環境でバックドアが検出されま
- 質問200 攻撃者は、機密データを盗み出すために無害なファイル内にデータ
- 質問201 最高情報セキュリティ責任者は、セキュリティおよびネットワーク
- 質問202 コードの再利用を回避することで脆弱性を減らすことができるのは
- 質問203 仮想環境の構築を計画する場合、管理者は次のことを達成する必要
- 質問204 新しいセキュリティ エンジニアがシステムの強化を開始しました
- 質問205 BYOD プログラムを設定する際のセキュリティ上の主な懸念事項は...
- 質問206 ある企業の最高情報セキュリティ責任者(CISO)は最近、セキュリ...
- 質問207 新しく購入した企業 WAP は、可能な限り最も安全な方法で構成す...
- 質問208 サイバー セキュリティ管理者は、iptables をエンタープライズ ...
- 質問209 組織は、IT チームが新しいラップトップをどの程度効果的に強化...
- 質問210 ある会社は、個人が車を建物に押し込んでゲームにアクセスするこ
- 質問211 セキュリティ エンジニアが初めてパスワードなしの認証を設定し
- 質問212 セキュリティ管理者は、LAN 上のワークステーションがマルウェア...
- 質問213 ある企業は、脅威アクターを誘惑し、攻撃者について詳しく知るた
- 質問214 次の制御のうち、制限された遠隔地の軍事訓練エリアの境界での侵
- 質問215 ある企業は最近、生体認証、コンテキスト認識型認証、デバイス全
- 質問216 セキュリティ管理者は、企業ネットワーク上の転送中のファイルを
- 質問217 リスク回避の例は次のうちどれですか?
- 質問218 フォレンジック調査中に否認防止を実現するのは次のうちどれです
- 質問219 ネットワーク アナリストが侵害された企業情報を調査しています
- 質問220 最高情報セキュリティ責任者は、シャドー IT のリスク削減を指示...
- 質問221 ある企業は、ヨーロッパの顧客の個人情報がどのように扱われるか
- 質問222 新しい脆弱性が公開されたときに、セキュリティ アナリストが組
- 質問223 セキュリティ アセスメント中に、セキュリティ担当者が権限が過
- 質問224 最高情報セキュリティ責任者 (CISO) は、セキュリティ スタッフ...
- 質問225 次のクラウド モデルのうち、クライアントにサーバー、ストレー
- 質問226 出席者の 1 人が接続の遅延に気付き始めます。HTTPS サイト要求...
- 質問227 ある組織が最近、セキュリティ コントロールの評価を完了しまし
- 質問228 ネットワーク アーキテクトは、サーバーが接続されているネット
- 質問229 業界標準のガイドラインを利用するために、最高情報セキュリティ
- 質問230 セキュリティ アーキテクトは、ビジネス パートナー向けのリモー...
- 質問231 電子商取引組織が誤った購入を防ぐために適用すべきセキュリティ
- 質問232 セキュリティ アナリストは、大量の従業員の資格情報が盗まれ、
- 質問233 コンプライアンス チームは、特権ユーザー アクセスと非特権ユー...
- 質問234 ハードドライブに保存されているデータを破壊する方法として、最
- 質問235 次のうち、インターネットボットによって常にスキャンされ、デフ
- 質問236 動的アプリケーション脆弱性スキャンにより、Web フォームを使用...
- 質問237 セキュリティ エンジニアは、会社の Web サイトが Web アプリケ...
- 質問238 ある開発者は、複数のファイアウォールを持つ顧客に一元的な管理
- 質問239 企業に対して攻撃が発生しました。 手順 あなたには次のことを行...
- 質問240 ある会社は、許可されていないデバイスが WiFi ネットワークを使...
- 質問241 次の安全なアプリケーション開発の概念のうち、詳細なエラー メ
- 質問242 組織は、すべてのラップトップで組み込みの FDE を有効にしたい...
- 質問243 Web アーキテクトは、会社の Web サイトのプレゼンスをクラウド...
- 質問244 ヘルプ デスク技術者は、組織のサイバーセキュリティ インシデン...
- 質問245 システム管理者は、認証されたゲスト アクセスのために新しいワ
- 質問246 あるグローバル企業は、ブルート フォース攻撃による資格情報の
- 質問247 今後のプロジェクトは、外部関係者間の安全な通信と信頼に焦点を
- 質問248 法執行当局は、電子的に保存された情報と紙の文書は破棄できない
- 質問249 次の役割のうち、上級管理職チームに直接アクセスできる可能性が
- 質問250 次のうち、現在のサイバー侵入、フィッシング、およびその他の悪
- 質問251 セキュリティ アナリストは、数時間後に大量の機密データがさま
- 質問252 データセンターは、低電圧イベントの増加を経験しました 施設外
- 質問253 評価中に、システム管理者は FTP を実行している複数のホストを...
- 質問254 セキュリティ アナリストは侵入テストのレポートを調査していま
- 質問255 フォレンジック調査中に、セキュリティ アナリストは、侵害され
- 質問256 クラウド セキュリティ エンジニアは、データ セキュリティを強...
- 質問257 ネットワーク侵入テスターがターゲット マシンへのアクセスに成
- 質問258 航空管制官は、朝の航空機のフライト プランの変更を電話で受け
- 質問259 攻撃の可能性を減らすために、ネットワークのセクションとその外
- 質問260 ユーザーの資格情報を狙ったフィッシング詐欺の後、赤いチームは
- 質問261 セキュリティ アナリストは、企業 Web アプリケーションへの不正...
- 質問262 大企業のデジタル フォレンジック チームは、悪意のあるコードが...
- 質問263 セキュリティ管理者は、機密性の高いシステムへの管理アクセスを
- 質問264 サイバーセキュリティ管理者は、ネットワークにレイヤー 7 セキ...
- 質問265 地震が発生しやすい地域にある重要なコンピューティング機器と比
- 質問266 次の認証方法のうち、特定の秒数内で使用される一意のパスワード
- 質問267 同じセクターの他の企業が自社のシステムに対して同様の悪意のあ
- 質問268 セキュリティ管理者は、企業全体の重要なイベントを監視するため
- 質問269 大企業は、すべてのデータを強力な認証と暗号化の背後にあるクラ
- 質問270 次のうち、コードが書かれるとすぐにメインのコードベースにコー
- 質問271 次のシナリオのうち、トークン化が使用するのに最適なプライバシ
- 質問272 セキュリティ アナリストは、侵害されたラップトップに対して攻
- 質問273 アプリケーション開発チームは、新しいヘルスケア アプリケーシ
- 質問274 LOT デバイスを使用して自動化を実装する場合、ネットワークの安...
- 質問275 攻撃者がクライアントの Web サイトでユーザーの資格情報を収集...
- 質問276 若手セキュリティ アナリストが Web サーバーのログを調査し、ロ...
- 質問277 ローカル ガイドラインでは、すべての情報システムが準拠するた
- 質問278 次のタイプのコントロールのうち、回転式改札口はどれですか?
- 質問279 セキュリティ アナリストは、企業に展開されているすべてのプロ
- 質問280 セキュリティ アーキテクトは、小規模な企業向けの新しいアウト
- 質問281 ネットワーク エンジニアは、ユーザーから報告されたワイヤレス ...
- 質問282 セキュリティ研究者は、その機能、インフラストラクチャ、および
- 質問283 実際の機密データを保存する必要なく、ユーザーの資格情報を検証
- 質問284 年次監査要件の一環として、セキュリティ チームは、特定のユー
- 質問285 ある企業は最近、データセンターからクラウドへの移行を完了しま
- 質問286 地元の大学の最高技術責任者は、訪問者に学校の WiFi を利用して...
- 質問287 新しいセキュリティ エンジニアがシステムの強化を開始しました
- 質問288 会社は最近侵害されました 会社の新しいサイバーセキュリティ戦
- 質問289 ある顧客が会社のセキュリティ チームに電話し、過去 5 日間に会...
- 質問290 組織の SIEM は、内部ネットワーク内のワークステーションからの...
- 質問291 データ センター内の組織のサーバーに物理的にアクセスするには
- 質問292 次のうち、実際のインシデント対応シナリオに対応するためのクロ
- 質問293 インシデントが発生している間、企業の CIRT は、コールバック ...
- 質問294 次のセキュリティ制御のうち、複数の人が一意のカードスワイプを
- 質問295 企業は、重要なサービスをサポートするためにレガシー ソフトウ
- 質問296 ネットワーク管理者は、データセンターのファイアウォールがオフ
- 質問297 ユーザーが SMS 経由で画像を送信しようとして失敗しました。ユ...
- 質問298 次のうち、攻撃者が DDoS またはランサムウェア サービスを購入...
- 質問299 システム管理者は、IT インフラストラクチャ用のさまざまなバッ...

