- ホーム
- CompTIA
- PT0-002J - CompTIA PenTest+ Certification (PT0-002日本語版)
- CompTIA.PT0-002J.v2024-04-16.q169
- 質問31
有効的なPT0-002J問題集はJPNTest.com提供され、PT0-002J試験に合格することに役に立ちます!JPNTest.comは今最新PT0-002J試験問題集を提供します。JPNTest.com PT0-002J試験問題集はもう更新されました。ここでPT0-002J問題集のテストエンジンを手に入れます。
PT0-002J問題集最新版のアクセス
「460問、30% ディスカウント、特別な割引コード:JPNshiken」
評価中に、ペネトレーション テスターがログを検査し、単一の IP アドレスから同じ URL に送信される一連の数千のリクエストを発見しました。ご要望の一部を以下に挙げます。
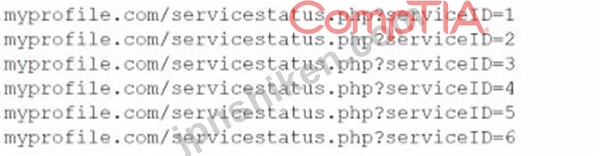
攻撃者が悪用しようとしたのは次の脆弱性のうちどれですか?

攻撃者が悪用しようとしたのは次の脆弱性のうちどれですか?
正解:C
The vulnerability that the attacker was trying to exploit is SQL injection, which is a type of attack that exploits a vulnerability in a web application that allows an attacker to execute malicious SQL statements on a database server. SQL injection can allow an attacker to perform various actions on the database, such as reading, modifying, deleting, or creating data, or executing commands on the underlying OS. The log shows that the attacker was sending thousands of requests to the same URL with different parameters, such as id=1' OR 1=1;-, id=1' AND 1=2;-, or id=1' UNION SELECT * FROM users;-. These parameters are examples of SQL injection payloads, which are crafted SQL statements that are designed to manipulate or bypass the intended SQL query. For example, id=1' OR 1=1;-- is a payload that terminates the original query with a single quote and a semicolon, appends an OR condition that is always true (1=1), and comments out the rest of the query with two dashes (-). This payload can cause the web application to return all records from the database table instead of just one record with id=1. The other options are not vulnerabilities that match the log entries. Session hijacking is a type of attack that exploits a vulnerability in a web application that allows an attacker to take over an active session of another user by stealing or guessing their session identifier or cookie. URL manipulation is a type of attack that exploits a vulnerability in a web application that allows an attacker to modify parameters or values in the URL to access unauthorized resources or functions. Insecure direct object reference is a type of attack that exploits a vulnerability in a web application that allows an attacker to access objects or resources directly by modifying their identifiers or references in the URL or request.
- 質問一覧「169問」
- 質問1 侵入テスターは、dirb ユーティリティを使用して Web サーバーを...
- 質問2 セキュリティの専門家は、TCP ポート 3011 でリッスンしている独...
- 質問3 ある企業が侵入テスターを雇って、従業員に対してソーシャル エ
- 質問4 侵入テスターは最近、企業環境内のコア ネットワーク デバイスの...
- 質問5 赤いチームのテスターは、企業のネットワーク上の悪意のあるイン
- 質問6 侵入テスターは、Nmap スキャンから次の結果を受け取ります。 (E...
- 質問7 API で HTTP 応答をインターセプトし、その内容を変更し、元のモ...
- 質問8 企業に対する内部侵入テスト中に、侵入テスト担当者はネットワー
- 質問9 Python スクリプト内で、print (var) と記述された行は次を出力...
- 質問10 ペネトレーション テスターが Web ベースのショッピング カタロ...
- 質問11 侵入テスターは、検出されることなく偵察を実行したいと考えてい
- 質問12 侵入テストを行うために、セキュリティ エンジニアは IT ヘルプ ...
- 質問13 侵入テスト中、テスト担当者は、Bluetooth フレームをブロードキ...
- 質問14 ペネトレーション テスターが、明示的な許可なしに、内部クライ
- 質問15 ペネトレーション テスターは、未知の Linux 64 ビット実行可能...
- 質問16 ペネトレーション テスターは、アカウントをロックせずに、ドメ
- 質問17 enum4linux.pl コマンドを実行した後、ペネトレーション テスタ...
- 質問18 次の PowerShell スニペットは、攻撃者のマシンのログから抽出さ...
- 質問19 ある企業が、企業の SSO ポータルを模倣したサイトへのリンクを...
- 質問20 最高情報セキュリティ責任者は、ペネトレーション テスターに
- 質問21 ペネトレーション テスターは Nmap スキャンを実行しており、接...
- 質問22 評価者は、ステートフル ファイアウォール ルール セットの計画...
- 質問23 次の出力は、一般向けの銀行 Web サイトでの偵察からのものです...
- 質問24 侵入テスターがサーバーを侵害し、権限をエスカレートすることが
- 質問25 侵入テスターが Web サイトをクロールし、Web サイトのパスワー...
- 質問26 会社のセキュリティ慣行の物理的評価を行っているペネトレーショ
- 質問27 侵入テスターが、保護されていない内部ソース コード リポジトリ...
- 質問28 Web サイトで侵入テストを実行しているテスターは、次の出力を受...
- 質問29 侵入テスターは、システムで次のコマンドを実行します。 検索 / ...
- 質問30 Python ソケット プログラミングでは、SOCK_DGRAM タイプは次の...
- 質問31 評価中に、ペネトレーション テスターがログを検査し、単一の IP...
- 質問32 企業は、共有ネットワーク帯域幅を持つクラウド プロバイダーを
- 質問33 コンサルタントは、断続的な接続の問題が報告された後、次の出力
- 質問34 顧客は、侵入テストの範囲に、アクティビティは通常の営業時間中
- 質問35 クライアントは、スケジュールされたメンテナンス期間の 1 週間...
- 質問36 侵入テスターは、Web アプリケーションのテスト中に次のトラフィ...
- 質問37 侵入テスターは、ワイヤレス セキュリティを確認するために契約
- 質問38 ある企業は、すべてのハイパーバイザーに最新の利用可能なパッチ
- 質問39 侵入テスターは、保護されていないネットワーク ファイル リポジ...
- 質問40 文字列値を別の文字列に追加すると、次のように呼び出されます。
- 質問41 幹部は出張中に Wi-Fi を使用して会社のサーバーに接続する必要...
- 質問42 侵入テスターは、営業時間外にクライアントの建物に侵入しようと
- 質問43 ペネトレーション テスターは、Web サーバーを侵害し、Linux Web...
- 質問44 ユーザーがログインした後、侵入テスターがHTTPプロトコルの状態...
- 質問45 侵入テスターは、サーバーから MD5 ハッシュを収集し、レインボ...
- 質問46 侵入テスターは、クライアントが会社の電子メール システムとし
- 質問47 評価中、ペネトレーション テスターは、Aircrack-ng を実行して...
- 質問48 最近、ペネトレーション テスターがソーシャル エンジニアリング...
- 質問49 クライアントは、セキュリティ評価会社に、そのホット サイトに
- 質問50 侵入テスターは、Web サーバーに対して脆弱性スキャンを実行する...
- 質問51 侵入テスターは、VoIP コール マネージャーで新たにリリースされ...
- 質問52 ペネトレーション テスターにはパブリック ドメイン名のみが...
- 質問53 ペネトレーションテスターは、アクティブなシステムを迅速に特定
- 質問54 侵入テスターは、評価の対象となった 16 ビットのネットワーク ...
- 質問55 侵入テストのスキャン段階の実行中に、侵入テスターは次のコマン
- 質問56 ペネトレーション テスターは、エンゲージメント中に使用する次
- 質問57 ペネトレーション テスターは、1 分あたり 100 を超える接続があ...
- 質問58 インターネットに直接接続されている IoT デバイスに関連する最...
- 質問59 侵入テスト中に CentOS コンピューターが悪用されました。最初の...
- 質問60 侵入テスターは、エンゲージメントで使用する資格情報を探すため
- 質問61 シミュレーション 出力を使用して、さらに調査する必要がある潜
- 質問62 侵入テスターが lsass.exe メモリ プロセスからパスワード ハッ...
- 質問63 侵入テスト中にセキュリティ アラームがトリガーされると、企業
- 質問64 侵入テスターは、公開されている Web サーバーのグループに対し...
- 質問65 いつ URL http://192.168.0-1/validate/user.php にアクセスする...
- 質問66 侵入テスト会社を評価しているクライアントが、その作業の例を要
- 質問67 OWASP Top 10 v2017 に含まれる Web アプリケーションのセキュリ...
- 質問68 侵入テスト中、テスターは URL の値を example.com/login.php?id...
- 質問69 あなたは、Web ブラウザーを介してクライアントの Web サイトを...
- 質問70 PCI DSS では、侵入テスト プロセスの一部として次のどれを要求...
- 質問71 エンゲージメント中に、侵入テスターがファイル内に次の文字列の
- 質問72 許可されていない開示を防止するための侵入テスターとクライアン
- 質問73 侵入テスト担当者が侵入テストを実施していて、クライアントが所
- 質問74 Nmap スキャンの結果は次のとおりです。 Nmap 7.80 ( https://nm...
- 質問75 ペネトレーション テスターが、明示的な許可なしに、内部クライ
- 質問76 次のコードがあるとします。 $p = (80, 110, 25) $network = (19...
- 質問77 侵入テスターは、評価対象の会社によって作成されたさまざまなソ
- 質問78 ペネトレーション テスターは、ネットワーク スイッチの脆弱性を...
- 質問79 ソフトウェア会社は、侵入テスト担当者を雇って、データベース
- 質問80 侵入テスターは、Web アプリケーションのコマンド インジェクシ...
- 質問81 ペネトレーション テスターは、内部の Web サーバーに対してブル...
- 質問82 システム管理者と技術スタッフが閲覧できる侵入テストレポートの
- 質問83 次のツールのうち、Web アプリケーションのセキュリティ評価を手...
- 質問84 侵入テスターは、ROE によって許可されている概念実証攻撃を...
- 質問85 ペネトレーション テスターは、新しいクライアントと共にスコー
- 質問86 次のうち、攻撃者が使用する一般的な戦術と手法のマトリックスと
- 質問87 ion tester は、ターゲット企業からより多くの人々に実行可能フ...
- 質問88 クライアントの関与中に、ペネトレーション テスターは次の Nmap...
- 質問89 赤いチームはエンゲージメントを完了し、レポートで次の例を提供
- 質問90 あ 侵入テスターは、Web アプリケーションの手動評価を行ってい...
- 質問91 アプリケーション開発者チームを対象読者として作成された静的ア
- 質問92 侵入テスターが企業のラボ ネットワークをスキャンして、潜在的
- 質問93 IoT デバイスが受動的偵察をサポートするためにベンダーやその他...
- 質問94 組織は、安全性の低いプロトコルがワイヤレス ネットワークで使
- 質問95 特定のネットワーク インフラストラクチャ製品に対するペイロー
- 質問96 セキュリティ エンジニアは、スキャンが 1 分あたり 100 パケッ...
- 質問97 ペネトレーションテスターは最終報告書に次のコメントを書いた:
- 質問98 侵入テスターは、次のスクリプトを作成します。 (Exhibit) テス...
- 質問99 企業組織との契約を準備する際に、侵入テスト活動を開始する前に
- 質問100 コンサルタントは、リモート ホストで開いているすべてのポート
- 質問101 侵入テスターは、モバイル クライアントのラップトップ上の Wind...
- 質問102 侵入テスト担当者は、侵入テストの最後にトラックをクリーンアッ
- 質問103 侵入テスターはターゲットに対して Nmap スキャンを実行し、次の...
- 質問104 ネットワーク スイッチの Nmap スキャンでは、次のことが明らか...
- 質問105 侵入テスト ツールからの出力は、不適切なパッチ管理による検出
- 質問106 侵入テスターは、クライアントの重要なサーバーに対して脆弱性ス
- 質問107 評価中、ペネトレーション テスターは、対象企業の IT システム...
- 質問108 ユーザー資格情報は、評価中にデータベースから取得され、レイン
- 質問109 積極的な偵察の一環として、ペネトレーション テスターは、API ...
- 質問110 次の評価方法のうち、ICS 環境に害を及ぼす可能性が最も高いのは...
- 質問111 コンサルティング会社は、スコーピング中に ROE を完成させてい...
- 質問112 侵入テスターが Web サーバーで評価を実施しました。このセッシ...
- 質問113 評価を行っているペネトレーション テスターは、管理者が企業の
- 質問114 侵入テスターは、サンドボックス環境でモバイル アプリケーショ
- 質問115 ある企業は、自社のクラウド VM がサイバー攻撃に対して脆弱であ...
- 質問116 ソーシャル エンジニアリング攻撃に対するトップ レベルの幹部の...
- 質問117 侵入テスターは、MITRE ATT&CK フレームワークを企業の主任...
- 質問118 ペネトレーション テスターは次のコマンドを実行します。 nmap -...
- 質問119 SCADA デバイスのある環境に対して侵入テストを実行すると、次の...
- 質問120 侵入テスターは、SSHD が実行されている Linux サーバーで実行す...
- 質問121 以前に正常にスキャンされたサーバーを侵入テスターがスキャンで
- 質問122 侵入テスターは、評価の途中で評価チームに加わります。クライア
- 質問123 次の行番号付きの Python コード スニペットは、偵察に使用され...
- 質問124 赤いチームは、エンゲージメント中にクライアントの内部ネットワ
- 質問125 ペネトレーション テスターは、侵害されたシステム上で次のスク
- 質問126 クライアントのクラウドおよびオンプレミス環境の評価中に、ペネ
- 質問127 カスタム構築された Web アプリケーションのテスト中に、ペネト...
- 質問128 ペネトレーション テスターは、デフォルト構成の Windows サーバ...
- 質問129 侵入テスターは、Windows サーバーで次のコマンドを実行しました...
- 質問130 侵入テスターは、1 つのエンゲージメントで使用される次のスクリ...
- 質問131 侵入テスターはマシンで unshadow コマンドを実行します。次のツ...
- 質問132 侵入テスターがコマンド sdelete mimikatz を実行する理由を説明...
- 質問133 侵入テスト活動が終了し、最初の調査結果がクライアントとレビュ
- 質問134 侵入テスターは、インターネットに接続されたネットワーク デバ
- 質問135 侵入テストの最終レポートに含める最も重要な項目は次のうちどれ
- 質問136 ペネトレーションテスターが 192.168.1.112 の評価を実施してい...
- 質問137 次のうち、アプリケーション コードでサードパーティのオープン
- 質問138 日常業務の中断を最小限に抑える必要がある企業には、企業の Web...
- 質問139 ある企業が、ネットワーク上で脆弱性スキャンを実施する侵入テス
- 質問140 計画された侵入テスト中に禁止されるアクティビティについて説明
- 質問141 セキュリティ エンジニアは、ネットワーク上に新しいサーバーを
- 質問142 あるソフトウェア会社は、会社のソフトウェア開発プラクティスの
- 質問143 ペネトレーション テスターは Web サーバーにアクセスし、システ...
- 質問144 外部のコンサルティング会社を雇って侵入テストを実施しますが、
- 質問145 次のツールのうち、侵入テスターがワイヤレス ハンドシェイクを
- 質問146 侵入テストでは、次の場合に競合解消が必要です。
- 質問147 ペネトレーション テスターは次の Nmap コマンドを実行し、次の...
- 質問148 ペネトレーション テスターが Linux Web サーバーでリバース シ...
- 質問149 ペネトレーションテスターは未知の環境テストを実施し、後の評価
- 質問150 メール サービス会社は、侵入テスターを雇って、SMTP サーバー上...
- 質問151 侵入テスト チームは、建物に侵入するための物理的な侵入テスト
- 質問152 侵入テスターがサーバーに対してスキャンを実行し、次の出力を取
- 質問153 侵入テスターは、ステージング サーバーで次のコマンドを実行し
- 質問154 セキュリティ アナリストが 192.168.3.3 から未知の環境テストを...
- 質問155 ペネトレーションテスターは企業のネットワーク境界を評価してい
- 質問156 侵入テスターは、サブネット上のライブ ホストをすばやく検出し
- 質問157 侵入テスターは、会社の業務の中断を最小限に抑える必要があるク
- 質問158 次のコードがあるとします。 <SCRIPT>var+img=new+Image()...
- 質問159 侵入テスターは、クライアントのシステムの評価中にいくつかの重
- 質問160 非特権アカウントで Linux システムにアクセスした後、ペネトレ...
- 質問161 侵入テスターは次のコマンドを実行します。 curl -I -http2 http...
- 質問162 ソフトウェア会社のネットワーク上のすべてのサーバーの認証スキ
- 質問163 侵入テスターはシステムへのアクセスを取得し、ユーザー プロセ
- 質問164 侵入テスターは、Nmap を使用してホスト 64.13.134.52 をスキャ...
- 質問165 コード レビュー評価中に、ペネトレーション テスターは、Web ア...
- 質問166 エクスプロイトの開発者は、サーバーが侵害されるまで、非常に多
- 質問167 次のスクリプトがあるとします。 (Exhibit) 次のうち、5行目と6...
- 質問168 次のタイプの評価のうち、特定のデータにアクセスする目的で脆弱
- 質問169 侵入テスターは、攻撃者が物理アクセス制御システムに使用される

