- ホーム
- Palo Alto Networks
- PCNSE-JPN - Palo Alto Networks Certified Network Security Engineer Exam (PCNSE日本語版)
- PaloAltoNetworks.PCNSE-JPN.v2024-06-20.q315
- 質問227
有効的なPCNSE-JPN問題集はJPNTest.com提供され、PCNSE-JPN試験に合格することに役に立ちます!JPNTest.comは今最新PCNSE-JPN試験問題集を提供します。JPNTest.com PCNSE-JPN試験問題集はもう更新されました。ここでPCNSE-JPN問題集のテストエンジンを手に入れます。
PCNSE-JPN問題集最新版のアクセス
「375問、30% ディスカウント、特別な割引コード:JPNshiken」
ある企業は、パロアルトネットワークスの次世代ファイアウォールの背後で、次の構成情報を備えたパブリックにアクセス可能な Web サーバーをホストしています。
- 社外のユーザーは「Untrust-L3」ゾーンにいます
- Web サーバーは物理的に「Trust-L3」ゾーンに存在します。
- WebサーバーのパブリックIPアドレス:23.54.6.10
- WebサーバーのプライベートIPアドレス:192.168.1.10
untrust-L3 ゾーンのユーザーが Web サーバーにアクセスできるようにするには、NAT ポリシーに含める必要がある 2 つの項目はどれですか? (2つお選びください)
- 社外のユーザーは「Untrust-L3」ゾーンにいます
- Web サーバーは物理的に「Trust-L3」ゾーンに存在します。
- WebサーバーのパブリックIPアドレス:23.54.6.10
- WebサーバーのプライベートIPアドレス:192.168.1.10
untrust-L3 ゾーンのユーザーが Web サーバーにアクセスできるようにするには、NAT ポリシーに含める必要がある 2 つの項目はどれですか? (2つお選びください)
正解:A,D
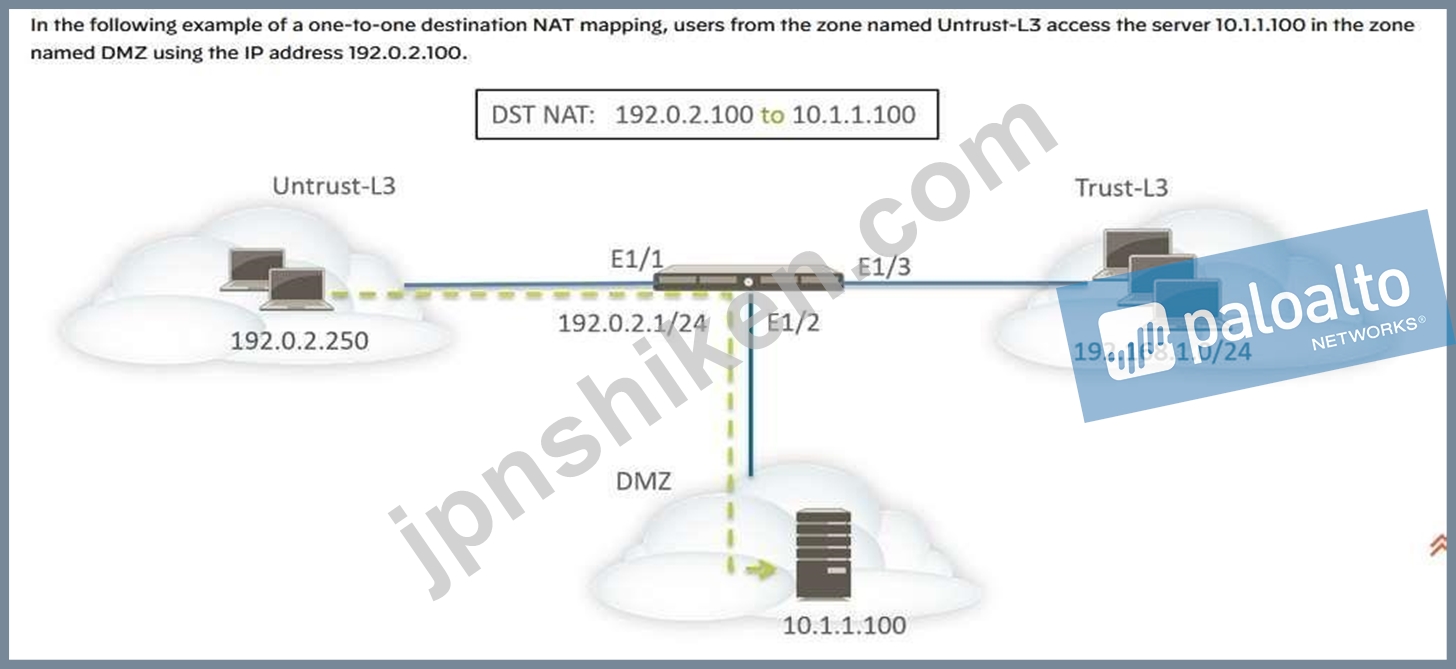
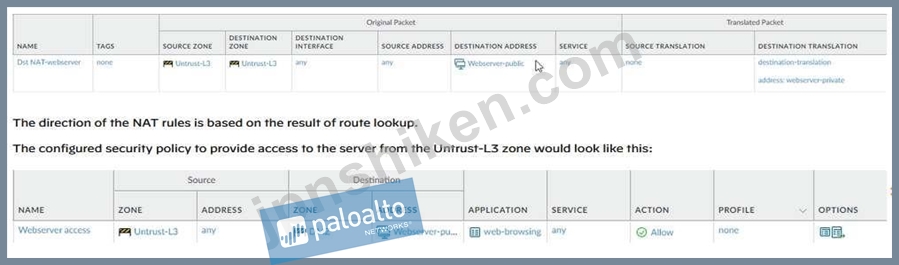
Before configuring the NAT rules, consider the sequence of events for this scenario.
Host 192.0.2.250 sends an ARP request for the address 192.0.2.100 (the public address of the destination server).
The firewall receives the ARP request packet for destination 192.0.2.100 on the Ethernet1/1 interface and processes the request. The firewall responds to the ARP request with its own MAC address because of the destination NAT rule configured.
The NAT rules are evaluated for a match. For the destination IP address to be translated, a destination NAT rule from zone Untrust-L3 to zone Untrust-L3 must be created to translate the destination IP of 192.0.2.100 to 10.1.1.100.
After determining the translated address, the firewall performs a route lookup for destination
10.1.1.100 to determine the egress interface. In this example, the egress interface is Ethernet1/2 in zone DMZ.
The firewall performs a security policy lookup to see if the traffic is permitted from zone Untrust- L3 to DMZ.
The direction of the policy matches the ingress zone and the zone where the server is physically located.
The security policy refers to the IP address in the original packet, which has a destination address of 192.0.2.100.
https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/networking/nat/nat-configuration- examples/ destination-nat-exampleone-to-one-mapping.html#ide8f6a4b3-f875-4855-acb5-
5fd9ad918d04
- 質問一覧「315問」
- 質問1 SSL フォワード プロキシ復号化を構成するためにエンジニアが実...
- 質問2 あなたは、組織に GlobalProtect を導入するよう依頼されました...
- 質問3 パケット フロー プロセス中に、アプリケーション識別で実行され...
- 質問4 WildFire が分析サンプルに対して提供できる 3 つの可能な判定は...
- 質問5 これまで知られていなかったファイル、URL、APK で悪意のあるア...
- 質問6 ファイアウォールは、パケットが新しいセッションの最初のパケッ
- 質問7 管理者は、管理者の自宅で Cisco ASA への IPSec VPN を設定して...
- 質問8 エンジニアは、外部サイトに送信されるトラフィック用に SSL フ...
- 質問9 ネットワーク管理者は、セキュリティ プロファイルを有効にした
- 質問10 ネットワーク セキュリティ エンジニアは、BGP プロトコルを使用...
- 質問11 ネットワーク セキュリティ エンジニアは、ブロック アクション...
- 質問12 ethernet1/3 に接続されているホストはインターネットにアクセス...
- 質問13 ファイアウォール管理者は、会社の syslog サーバーがトラフィッ...
- 質問14 ネットワーク エンジニアは、VPN フェーズ 2 の不一致のトラブル...
- 質問15 クライアントはデータ センターに機密性の高いアプリケーション ...
- 質問16 顧客は従来のリモート アクセス VPN ソリューションを置き換えよ...
- 質問17 同じルートが、3 つの異なるプロトコルを使用してルーティング ...
- 質問18 基本的な WildFire サービスの一部として、分析のために WildFir...
- 質問19 管理者は、DMZ 内の複数の Web サーバーがインターネットから開...
- 質問20 管理者は、リモート システムへの確立された接続を通じてデータ
- 質問21 PAS-OS 7.0 では、ログ パターンを分析し、新しい Application C...
- 質問22 ある組織は、ゲスト トラフィックと BYOD トラフィックの復号化...
- 質問23 管理者は、3 つのリモート ネットワークを持つ Prisma Access Re...
- 質問24 Web サイトのフォームへの企業ログイン情報の送信を妨げる機能は...
- 質問25 正誤問題: 多くの顧客は、これまで不可能だったトラフィック フ...
- 質問26 セキュリティ プロファイルを設定するときに使用できる 3 つの項...
- 質問27 特定の宛先 IP に対するサービス ルートはどこで設定できますか?...
- 質問28 管理者が Web サイトの証明書を所有していない場合、ユーザーが ...
- 質問29 www.2600.com などのブロックされたハッキング Web サイトを...
- 質問30 エンジニアは、内部ユーザーのトラフィックがファイアウォールを
- 質問31 示されているサンプル ログ転送プロファイルを考慮すると、次の ...
- 質問32 セキュリティ プロファイルを設定するときに使用できる 3 つの項...
- 質問33 管理者は、レイヤー 7 署名を含むカスタム アプリケーションを作...
- 質問34 管理者は、すべてのポート上のトラフィックを復号化する SSL 復...
- 質問35 「証明書」ページのスクリーンショットを確認してください。 (Ex...
- 質問36 サイト A とサイト B は、IKEv2 を使用して VPN 接続を確立する...
- 質問37 エンジニアは、ファイアウォールとスイッチ間の帯域幅と冗長性を
- 質問38 管理者は、Citrix XenApp 7 x を介してネットワーク リソースに...
- 質問39 GlobalProtect クライアントレス VPN ではどのプロトコルがサポ...
- 質問40 PAN-OS SD-WAN を展開する場合、ルーティング オーバーレイの構...
- 質問41 Panorama の Templates オブジェクト内で定義されている 3 つの...
- 質問42 アクティブ/パッシブ HA ペアのパッシブ PA-7050 ファイアウォー...
- 質問43 新しいファイアウォールが高可用性 (HA) クラスターに参加すると...
- 質問44 管理者は、GlobalProtect を使用してデバイスを自動的に隔離する...
- 質問45 セキュリティ ポリシーが最も高い優先順位を持つようにするには
- 質問46 復号化プロファイルを復号化ポリシー ルールに割り当てることで
- 質問47 エンジニアはアクティブ/アクティブ高可用性 (HA) ファイアウォ...
- 質問48 ドラッグ アンド ドロップの質問 各 GlobalProtect コンポーネン...
- 質問49 [ネットワーク] > [GlobalProtect] > [ポータル] > [エ...
- 質問50 ある企業は、ネットワークに User-ID を導入しています。ファイ...
- 質問51 ファイアウォールは、検査のために復号化されたトラフィックをセ
- 質問52 NGFW にユーザー ID マッピング情報を提供できる機能はどれです...
- 質問53 A/P ファイアウォール クラスターが IPsec トンネル セキュリテ...
- 質問54 GlobalProtect ゲートウェイのスプリット トンネリングでサポー...
- 質問55 ベスト プラクティスとして、SSL 復号化の最初の対象となる URL ...
- 質問56 パロアルトネットワークスの NGFW (次世代ファイアウォール) の ...
- 質問57 DOS 保護プロファイルで送信元 IP アドレスからの最大同時セッシ...
- 質問58 管理者は、すべての非ネイティブ MFA プラットフォームを PAN-OS...
- 質問59 管理者はアプリケーションベースのセキュリティ ポリシー ルール...
- 質問60 セッション 380280 を正しく説明している 3 つのステートメント...
- 質問61 IPv6 ルーティング プロトコルはどのオプションですか?
- 質問62 管理者には、復号化されたトラフィックをパロアルトネットワーク
- 質問63 ファイアウォールが「ドメイン資格情報フィルター」方式を使用し
- 質問64 管理者は Panorama デバイス グループを設定しています。 構成可...
- 質問65 ファイアウォールは SSL フォワード プロキシ復号化を使用して構...
- 質問66 NGFW で別のライセンスが必要な 2 つの機能はどれですか? (2つお...
- 質問67 エンジニアは、単一セッションの DoS 攻撃から保護するために、...
- 質問68 エンジニアは SSL 復号化の実装を計画しています。 次のステート...
- 質問69 DNS シンクホールが構成されている場合、感染した可能性のあるホ...
- 質問70 管理者は、インターフェイス設定がファイアウォール上でローカル
- 質問71 ある企業には、オンサイト ファイアウォールと、Panorama によっ...
- 質問72 パロアルトネットワーク VM シリーズ ファイアウォールの展開を...
- 質問73 復号化ファイアウォールの展開のサイジングを行う際に考慮すべき
- 質問74 ファイアウォール管理者は、スタンドアロンのパロアルトネットワ
- 質問75 PAN-OS@software が MFA に対してサポートする 3 つの認証要素は...
- 質問76 管理者は、ユーザーを認証するための外部認証サービスとして LDA...
- 質問77 パロアルトネットワークスのファイアウォールが NTP Amplificati...
- 質問78 エンジニアは、継承されたグローバル サービス ルート構成を使用...
- 質問79 ある企業では、Active/Passive High Availability (HA) ペアとし...
- 質問80 Panorama を 10.2 にアップグレードしたので、6 つのログ コレク...
- 質問81 管理者は Panorama と複数の Palo Alto Networks NGFW を使用し...
- 質問82 復号転送インターフェイスのペアでサポートされている復号ブロー
- 質問83 ネットワーク管理者は、SSL フォワード プロキシ復号化を導入し...
- 質問84 ファイアウォール エンジニアは、[監視] > [レポート] > [...
- 質問85 中小企業の管理者は最近、自己署名ルート証明書を使用してパロア
- 質問86 動的ユーザー グループ (DUG) を使用してリアルタイムでトラフィ...
- 質問87 ファイアウォールは MineMeld から IP アドレスをダウンロードし...
- 質問88 SD-WAN は、どの 2 つのネットワーク トポロジ タイプをサポート...
- 質問89 ユーザー マッピングの 3 つの有効な方法は何ですか? (3つお選び...
- 質問90 管理者はパロアルトネットワークファイアウォールでアドバンスル
- 質問91 ファイアウォール エンジニアは PAN-OS GlobalProtect アプリケ...
- 質問92 システム管理者は、脆弱性チェックの一環として、会社のツールを
- 質問93 管理者は、内部システム上のオペレーティング システムの欠陥を
- 質問94 VM-500 の管理者が DoS とゾーン保護を有効にする前に、どのよう...
- 質問95 NGFW では、秘密キーを生成してエクスポートをブロックし、セキ...
- 質問96 HA Lite でサポートされている 3 つのオプションはどれですか? ...
- 質問97 ファイアウォール リソース保護設定を構成できるコンポーネント
- 質問98 ポリシー ルール UUID はどのような利点を提供しますか?
- 質問99 接続されているデバイスに動的更新をプッシュするように Panoram...
- 質問100 パケット バッファ保護に関する情報はどこに記録されますか?
- 質問101 管理者は 2 つのデバイスで HA ハートビート バックアップを有効...
- 質問102 ファイアウォール エンジニアは、[監視] > [レポート] > [...
- 質問103 顧客は、リンク アグリゲーションを使用して複数のイーサネット ...
- 質問104 監査人は Panorama の設定を評価しており、Panorama テンプレー...
- 質問105 クライアントは、サーバーに対する Web シェル攻撃を懸念してい...
- 質問106 セキュリティ ポリシーを Panorama から PA-3020 ファイアウォー...
- 質問107 アクティブ/パッシブ高可用性 (HA) ペアでパロアルトネットワー...
- 質問108 IPV6 DNS クエリはユーザー インターフェイス ethernet1/3 にど...
- 質問109 動的ユーザー グループ メンバーシップの更新は自動的に行われる...
- 質問110 エンジニアは、グローバル テンプレートを介して設定された DNS ...
- 質問111 エンジニアは、管理のためにパロ アルト ネットワーク ファイア...
- 質問112 SSL フォワード プロキシの復号化では、証明書の署名に使用でき...
- 質問113 PA-440 ハードウェア プラットフォームの特徴は何ですか?...
- 質問114 画像を参照してください。管理者は、グローバル テンプレート NT...
- 質問115 図を参照してください。内部システムのユーザーは、SSH サーバー...
- 質問116 ネットワーク セキュリティ エンジニアは、IPv6 アドレスを使用...
- 質問117 管理者は、インターネット トラフィックにどの NAT ポリシーが使...
- 質問118 ファイアウォールは、一般的なアプリケーションを不明な tcp と...
- 質問119 IPv6 ルーティング プロトコルはどのオプションですか?
- 質問120 VMware NSX でサポートされている Palo Alto Networks VM-Series...
- 質問121 エンジニアは、マルチ vsys ファイアウォールの展開を設計してい...
- 質問122 ファイアウォール エンジニアは、IP アドレス 1.1.1.10 を 192.1...
- 質問123 エンタープライズ PKI を使用する管理者は、Panorama と管理対象...
- 質問124 管理者は、Palo Alto Networks NGFW を PAN-OS® ソフトウェアの...
- 質問125 VPN のフェーズ 2 では接続は確立されません。ピアはポリシーベ...
- 質問126 管理者は、更新プログラムのインストールを一定時間遅らせながら
- 質問127 サイト A とサイト B の間に VPN 接続が設定されていますが、サ...
- 質問128 管理者は、リソースの枯渇を防ぐために、パロアルトネットワーク
- 質問129 次の画像に表示されている証明書情報は、どの種類の証明書のもの
- 質問130 展示を参照してください。 (Exhibit) トラフィックの入力インタ...
- 質問131 管理者はパロアルトネットワーク NGFW 上の仮想ルーターで BGP ...
- 質問132 ブートストラップ USB フラッシュ ドライブは、パロ アルト ネッ...
- 質問133 管理者は、SSL フォワード プロキシを展開する任務を負っていま...
- 質問134 ファイアウォールがパケット フロー シーケンスの一部としてパケ...
- 質問135 上記のスクリーンショットに基づくと、テンプレート スタック自
- 質問136 画像から判断すると、コミット警告の原因は何でしょうか? (Exhib...
- 質問137 PAN-OS SD-WAN のどの機能を使用すると、帯域幅を大量に消費する...
- 質問138 これらの表を考慮すると、次のようになります。 (Exhibit) SVR1 ...
- 質問139 管理者は VPN システム ログの次の部分を分析し、次の問題に気付...
- 質問140 トラフィック ログのセッションでは、アプリケーションが「不完
- 質問141 上のスクリーンショットで、表示されている ACC 構成から判断で...
- 質問142 ベスト プラクティスとして、セッション開始時のログ記録はどの
- 質問143 エンジニアは復号化ブローカー機能を構成する必要があります。エ
- 質問144 会社の Panorama サーバー (IP 10.10.10.5) は、最近導入された...
- 質問145 Web サーバーは DMZ でホストされており、サーバーは TCP ポート...
- 質問146 パノラマ サーバーに障害が発生した場合にログをデータ損失から
- 質問147 復号化戦略を策定し、企業ユーザーがアクセスするためにどの Web...
- 質問148 ファイアウォール上でローカルにのみ構成でき、Panorama テンプ...
- 質問149 VM-Series ファイアウォールではどの機能を構成できますか?...
- 質問150 この図に基づいて、「サーバー監視」パネルに表示される出力を正
- 質問151 正誤問題: シングル パス並列処理 (SP3) の利点の 1 つは、最小...
- 質問152 ファイアウォールの管理のために認証と認可の両方を実行する 3 ...
- 質問153 候補または実行コンフィギュレーションを Panorama から外部のホ...
- 質問154 ある企業は、ネットワーク ルーティングを再設計せずに脅威防御
- 質問155 どの操作が管理プレーンのパフォーマンスに影響しますか?
- 質問156 サイト A とサイト B の間にはサイト間 VPN が設定されています...
- 質問157 管理者は、アプリケーションのパフォーマンス低下に関する苦情を
- 質問158 エンジニアはアクティブ/アクティブ高可用性 (HA) ファイアウォ...
- 質問159 図を参照してください。管理者は、NYC で使用できるアドレス オ...
- 質問160 パロアルトネットワークスの NGFW 管理者が、新しいコンテンツ I...
- 質問161 ある組織は、PAN-OS 11.0 の Web プロキシ機能を活用する利点に...
- 質問162 Panorama によって生成されたログを外部のセキュリティ情報およ...
- 質問163 管理者は、アクティブな脅威対策サブスクリプションを持つ PA-82...
- 質問164 エンジニアは、非対称環境ではアプリケーションが動作せず、Web ...
- 質問165 エンジニアは、信頼性の低い高可用性 (HA) リンクのトラブルシュ...
- 質問166 管理者は、パロアルトネットワークス NGFW の管理インターフェイ...
- 質問167 タグ付けを使用したログ転送の組み込みアクションを使用すると、
- 質問168 管理者は、Active Directory で定義された特定のユーザーおよび...
- 質問169 エンジニアは、特定のリアルタイム トラフィックが、定義された
- 質問170 GlobalProtectアプリのPanGPAログからの次のメッセージを考える...
- 質問171 管理者は、WebUI のどこで管理プレーンとデータ プレーンの CPU ...
- 質問172 有効な ACC GlobalProtect アクティビティ タブ ウィジェットは...
- 質問173 ネットワーク セキュリティ エンジニアは、ファイアウォール上で...
- 質問174 復号化ポリシー ルールの一致に有効な 3 つの修飾子は何ですか? ...
- 質問175 非標準の syslog サーバーと互換性のある形式で syslog メッセー...
- 質問176 PAN-OS でサポートされている 4 つの NGFW 多要素認証要素はどれ...
- 質問177 新しいセキュリティ ポリシーを作成するときに有効な 3 つのオプ...
- 質問178 tcpdump キャプチャをエクスポートするにはどの CLI コマンドを...
- 質問179 Panorama でポリシーを定義する場合、どの 3 つのルール タイプ...
- 質問180 ファイアウォールのデフォルトの TCP および UDP 設定では、次の...
- 質問181 Web サーバーは DMZ でホストされており、サーバーは TCP ポート...
- 質問182 管理者は、DMZ とコア ネットワークの間に NGFW を実装する必要...
- 質問183 ターミナル サーバー経由で接続しているユーザーのユーザー名に ...
- 質問184 管理者がデバイスグループとテンプレートスタックの展開のために
- 質問185 新しい NGFW を実装した後、ファイアウォール エンジニアは、フ...
- 質問186 ファイアウォール管理者は、すべての Panorama 設定がコミットさ...
- 質問187 ネットワーク管理者は Panorama を使用して、ブランチ オフィス...
- 質問188 HA フェイルオーバー シナリオでは、SSL フォワード プロキシ復...
- 質問189 次の図を考えてみます。 (Exhibit) サイト A の Trust-L3 ゾーン...
- 質問190 デバイス グループ内で、どの 2 つの構成オブジェクトが定義され...
- 質問191 ファイアウォールが通過するトラフィックをキャプチャできないよ
- 質問192 事前定義されたデフォルトのウイルス対策プロファイルを使用する
- 質問193 SSH プロキシ復号化ポリシーを作成する前に満たす必要がある前提...
- 質問194 アクティブ/アクティブ高可用性ペアを構成する場合、どの 2 つの...
- 質問195 管理者は Panorama を使用して私を管理しており、ファイアウォー...
- 質問196 テンプレートで設定できるオブジェクトは次の 2 つですか? (2つ...
- 質問197 ネットワーク設計を変更するには、既存のファイアウォールが管理
- 質問198 管理者は、パケットドロップを引き起こす問題のトラブルシューテ
- 質問199 脅威ログのタグをリモートの User-ID エージェントと共有する場...
- 質問200 設定ファイルをバックアップおよび保存する場合、ファイアウォー
- 質問201 スクリーンショットを参照してください。コンテキスト スイッチ
- 質問202 管理者は、Panorama デバイス展開オプションを使用して、管理対...
- 質問203 ファイアウォールに次のリンク監視構成がある場合、フェイルオー
- 質問204 Panorama は、感染した VM を隔離するよう VMWare NSX にどのよ...
- 質問205 ある企業がネットワーク内で WildFire の利用を開始しました。 ...
- 質問206 ネットワーク セキュリティ管理者は、組織に User-ID を展開する...
- 質問207 ネットワーク管理者は、ファイアウォール上にゾーン内セキュリテ
- 質問208 図に示すように、アドレス指定構造がアドレスの特定のビットに意
- 質問209 SSL フォワード プロキシの復号化問題のトラブルシューティング...
- 質問210 ブートストラップ USB フラッシュ ドライブは、以前にラボで使用...
- 質問211 PAN-OS® ソフトウェアがアプリケーションを識別するために使用す...
- 質問212 HA ペアの設定を Panorama にインポートする場合、インポートが...
- 質問213 新しいコンプライアンス要件をサポートするために、あなたの会社
- 質問214 ファイアウォール管理者は、ホストされているサービスが悪用され
- 質問215 管理者は、アクティブ ファイアウォールとパッシブ ファイアウォ...
- 質問216 DoS プロテクションとゾーンプロテクションプロファイルに関して...
- 質問217 ポリシー ルール UUID にはどのようなメリットがありますか?...
- 質問218 SD-WAN 構成計画時に重要な考慮事項となる 3 つの項目はどれです...
- 質問219 管理者は、エンドポイントで HIP チェックを実行して、セキュリ...
- 質問220 トラフィックの入力インターフェイスが ethernet1/6 ソースの場...
- 質問221 ネットワーク セキュリティ エンジニアは、環境内のさまざまなア...
- 質問222 次の表を考えます。ファイアウォールのどの構成変更により、ファ
- 質問223 ファイアウォールのペアでアクティブ/パッシブ モードで HA を構...
- 質問224 ドラッグ アンド ドロップの質問 以下は、ファイアウォールおよ...
- 質問225 異なる仮想システムが相互に通信できるのは、どのタイプのゾーン
- 質問226 コンサルタントは、PAN-OS 11.0 での明示的な Web プロキシ展開...
- 質問227 ある企業は、パロアルトネットワークスの次世代ファイアウォール
- 質問228 HA グループ ID が一致しない場合、ファイアウォールのペアはど...
- 質問229 エンジニアは、トラフィックが遅いという問題を解決しようとして
- 質問230 ネットワーク セキュリティ管理者は、ゾーン保護プロファイルで
- 質問231 Panorama を PAN-OS 8.1 より前のバージョンに戻すことを計画す...
- 質問232 ネットワーク セキュリティ管理者は、複数の認証形式を備えた環
- 質問233 最大ストレージ容量に達した場合、Panorama は受信ログをどのよ...
- 質問234 インターネット ゾーン上のユーザーが DMZ ゾーンでホストされて...
- 質問235 展示を参照してください。管理者は DNAT を使用して 2 つのサー...
- 質問236 セキュリティ エンジニアは、会社に導入されているファイアウォ
- 質問237 アプリケーション サーバーのリソース枯渇を軽減するために使用
- 質問238 セキュリティ第一のネットワークでは、アプリと脅威が動的に更新
- 質問239 AutoFocus へのファイアウォールの接続を確認するために使用でき...
- 質問240 外部 Web サイトへのエンド ユーザー SSL トラフィックを制御す...
- 質問241 GlobalProtect ポータル インターフェイスと IP アドレスが設定...
- 質問242 ある企業は、不良と分類したアプリケーションをすべて拒否し、良
- 質問243 SSL フォワード プロキシを有効にせずに、信頼できない証明書を...
- 質問244 PAN-OS 10.2 で実行される Advance Routing Engine を有効にした...
- 質問245 自動コミットリカバリ機能を最もよく説明しているのはどれですか
- 質問246 エンジニアは、組織の SSL フォワード プロキシ復号化を展開する...
- 質問247 ファイル共有アプリケーションが許可されていますが、このアプリ
- 質問248 ユーザー名と IP アドレスのマッピングを取得するために、PAN-OS...
- 質問249 管理者は、NGFW を PAN-OS ソフトウェアの最新バージョンにアッ...
- 質問250 トラフィック ログにアプリケーションが「適用不可」としてリス
- 質問251 ネットワーク管理者は、大規模な VPN ソリューションを導入した...
- 質問252 以下の情報を確認してください。ファイアウォール エンジニアは
- 質問253 パロアルトネットワーク管理ポートと、それに接続されているスイ
- 質問254 管理者は、IP アドレスをユーザー名にマップするように Palo Alt...
- 質問255 セキュリティ ポリシー ルールは、脆弱性保護プロファイルと「拒...
- 質問256 セキュリティ ポリシーには、信頼から非信頼への許可ルールが 2 ...
- 質問257 管理者は認証強制を構成しており、特定のグループを認証から除外
- 質問258 管理者は、アクティブ/パッシブ モードの高可用性を使用してファ...
- 質問259 管理者は、デバイス グループ内の 1 つのファイアウォールに特定...
- 質問260 ネットワーク管理者は、大規模な VPN ソリューションを導入した...
- 質問261 監査人は、セキュリティ チーム内で役割と責任を分割するよう要
- 質問262 あるエンジニアは、すべてのデバイス間で共有される特定の構成セ
- 質問263 ある企業は、ユーザーを認証するためにワイヤレス コントローラ
- 質問264 SSL フォワード プロキシ復号化の実装中に、管理者は会社のエン...
- 質問265 ファイアウォール管理者は、会社のファイアウォールでのパケット
- 質問266 エンジニアは、インターネット ゲートウェイ上でパロ アルト ネ...
- 質問267 PAN-OS 7.0 でアクティブ/アクティブ高可用性 (HA) をサポートす...
- 質問268 管理者は、Palo Alto Networks NGFW のペアに対してアクティブ/...
- 質問269 ある組織は、パロアルトネットワーク VM シリーズ ファイアウォ...
- 質問270 管理者は、(「クラウド」ではなく) ローカルのオンプレミスのラ...
- 質問271 SSL フォワード プロキシ復号化ポリシーが構成されています。次...
- 質問272 エンジニアは、トンネル監視が 1 日間失敗しており、VPN がバッ...
- 質問273 管理者は Panorama と複数の Palo Alto Networks NGFW を使用し...
- 質問274 ネットワーク エンジニアは VPN のトラブルシューティングを行っ...
- 質問275 ネットワーク セキュリティ チームのマネージャーから、パロ ア...
- 質問276 クライアントは、アクティブ/パッシブ モードで高可用性 (HA) を...
- 質問277 GlobalProtect アプリが GlobalProtect ゲートウェイへの IPSec ...
- 質問278 ファイアウォール エンジニアは、インターネットからエッジ ファ...
- 質問279 IP 範囲タイプのアドレス オブジェクトはどのように正しく定義さ...
- 質問280 管理者がパロアルトネットワーク NGFW にログインし、WebUI に [...
- 質問281 顧客はトンネル インターフェイスを使用してサイト間 VPN をセッ...
- 質問282 decrypt-cert-validation エラーを受け取る正当な理由ではないも...
- 質問283 アクセス ルート、宛先ドメイン、アプリケーションごとにスプリ
- 質問284 管理者は、デバイス グループとテンプレート スタックの展開のた...
- 質問285 Palo Alto Networks ファイアウォールの管理プレーン (コントロ...
- 質問286 管理者は、すべての管理サービスにデフォルト ポートを使用する
- 質問287 パケットバッファ保護はどのように設定できますか?
- 質問288 クライアントは、LOT デバイスに対する脆弱なメーカーデフォルト...
- 質問289 管理者は、信頼ゾーン上のユーザーが特定の Web サイトにアクセ...
- 質問290 エンジニアは、環境全体で SSL 復号化を有効にするという任務を...
- 質問291 HA4 キープアライブしきい値 (ミリ秒) を最もよく表すのは何です...
- 質問292 管理者は、フェイルオーバーと中断のない VPN サービスを提供す...
- 質問293 Palo Alto Networks NGFW をアップグレードする前に何をする必要...
- 質問294 ネットワーク エンジニアは、非対称ルーティングが原因でパロア
- 質問295 ファイアウォール エンジニアは、アプリケーションのダウンタイ
- 質問296 ある組織は最近、インフラストラクチャと構成を NGFW に移行し、...
- 質問297 SAML SLO は、どの 2 つのファイアウォール機能でサポートされて...
- 質問298 情報セキュリティは、ネットワーク内の IP からユーザーへのマッ...
- 質問299 管理者は、パノラマ レポートでパロ アルト ネットワーク NGFW ...
- 質問300 ファイル ブロック プロファイルで有効な 3 つのアクションは何...
- 質問301 ネットワーク セキュリティ エンジニアが Microsoft Azure 上で...
- 質問302 スクリーンショットを考えると、ファイアウォールはトラフィック
- 質問303 ネットワーク セキュリティ管理者は、SIP トラフィックがポリシ...
- 質問304 以前は不明だったファイルに関する Wildfire の更新は、WildFire...
- 質問305 パロアルトネットワークファイアウォールのどの種類のポリシーで
- 質問306 ファイアウォール管理者は、侵害されたホストが外部のコマンド
- 質問307 pcap フィルターに含めることができる 3 つのフィールドはどれで...
- 質問308 エンジニアがトラフィック ルーティングの問題のトラブルシュー
- 質問309 管理者は SSL 復号化を構成しており、SSL 受信検査と SSL フォワ...
- 質問310 管理者が送信元に基づいてトラフィックに QoS を適用したい場合...
- 質問311 復号化ミラーを正確に説明している 3 つのステートメントはどれ...
- 質問312 GlobalProtect のどのバージョンが、宛先ドメイン、クライアント...
- 質問313 アプリケーションオーバーライドを実装するには、どの 3 つの項...
- 質問314 新たに発見されたボットネットに関する重要な US-CERT 通知が公...
- 質問315 App-ID はアプリケーションを識別するために何を検査しますか?...

[×]
Download PDF File
Enter your email address to download PaloAltoNetworks.PCNSE-JPN.v2024-06-20.q315.pdf
