- ホーム
- Microsoft
- SC-300J - Microsoft Identity and Access Administrator (SC-300日本語版)
- Microsoft.SC-300J.v2025-09-01.q160
- 質問13
有効的なSC-300J問題集はJPNTest.com提供され、SC-300J試験に合格することに役に立ちます!JPNTest.comは今最新SC-300J試験問題集を提供します。JPNTest.com SC-300J試験問題集はもう更新されました。ここでSC-300J問題集のテストエンジンを手に入れます。
SC-300J問題集最新版のアクセス
「340問、30% ディスカウント、特別な割引コード:JPNshiken」
Microsoft 365 E5 テナントがあります。
App1 という名前のクラウド アプリを購入します。
Microsoft Defender for Cloud Apps を使用して、App1 のリアルタイム セッション レベルの監視を有効にする必要があります。
どの順序でアクションを実行すればよいですか? 回答するには、適切なアクションをアクション リストから回答領域に移動し、正しい順序に並べます。

App1 という名前のクラウド アプリを購入します。
Microsoft Defender for Cloud Apps を使用して、App1 のリアルタイム セッション レベルの監視を有効にする必要があります。
どの順序でアクションを実行すればよいですか? 回答するには、適切なアクションをアクション リストから回答領域に移動し、正しい順序に並べます。

正解:
Explanation:
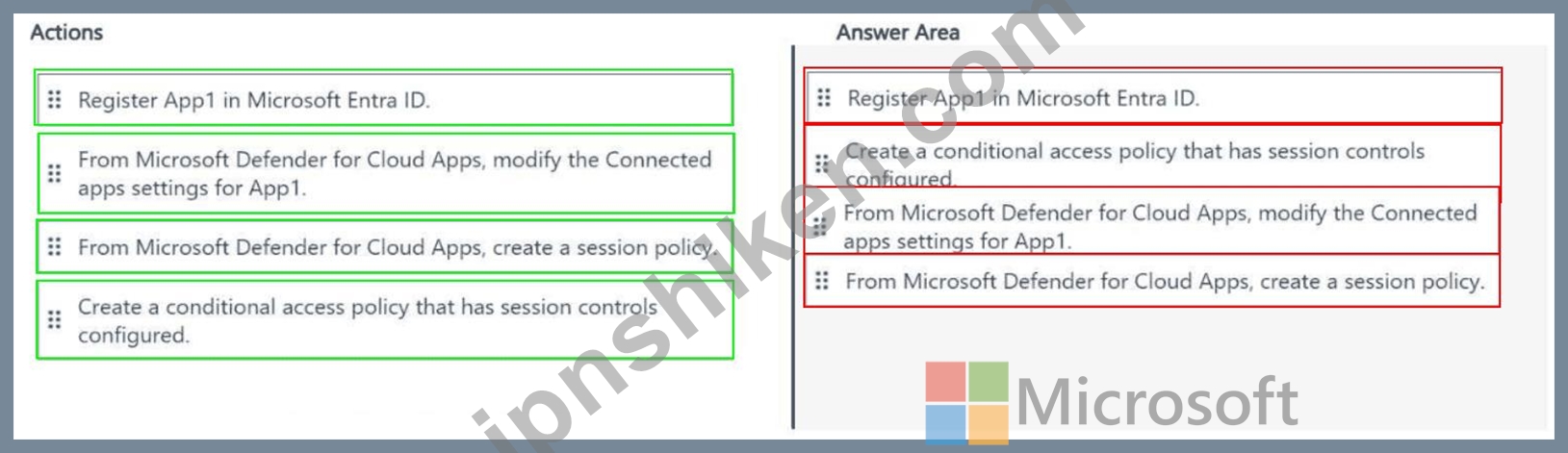
Register App1 in Microsoft Entra ID.
Create a conditional access policy that has session controls configured.
From Microsoft Defender for Cloud Apps, modify the Connected apps settings for App1.
From Microsoft Defender for Cloud Apps, create a session policy.
Let's break this down step by step based on Microsoft Defender for Cloud Apps (MDCA) and Microsoft Entra ID integration for enabling real-time session-level monitoring, as outlined in Microsoft Identity and Access Administrator documentation.
Understanding the Goal: Real-Time Session-Level Monitoring with Microsoft Defender for Cloud Apps:
Microsoft Defender for Cloud Apps (MDCA) is a Cloud Access Security Broker (CASB) solution that provides visibility, control, and threat protection for cloud applications.
Real-time session-level monitoring allows MDCA to inspect and control user activities within a cloud app (App1 in this case) during active sessions. This requires integration with Microsoft Entra ID and the use of Conditional Access policies to route sessions through MDCA for monitoring.
The Microsoft 365 E5 tenant includes licenses for Microsoft Entra ID P2 and Microsoft Defender for Cloud Apps, which are necessary for this functionality.
Step-by-Step Analysis of the Actions:To enable real-time session-level monitoring, the actions must be performed in a logical order that aligns with Microsoft's recommended workflow for integrating a cloud app with MDCA.
Step 1: Register App1 in Microsoft Entra ID.
Before App1 can be monitored by MDCA, it must be registered as an application in Microsoft Entra ID. This step involves adding App1 to the tenant's enterprise applications, which allows Microsoft Entra ID to manage authentication and authorization for the app.
Registering the app in Microsoft Entra ID enables single sign-on (SSO) and allows the app to be governed by Conditional Access policies, which is a prerequisite for session-level monitoring.
This is the first step because none of the other actions can proceed without App1 being recognized by Microsoft Entra ID.
Step 2: Create a conditional access policy that has session controls configured.
Microsoft Defender for Cloud Apps integrates with Microsoft Entra ID Conditional Access to enforce session-level monitoring. A Conditional Access policy must be created to target App1 and include session controls that route user sessions through MDCA.
In the Conditional Access policy, under "Session" controls, you enable the option "Use Conditional Access App Control," which integrates with MDC This step must come after registering the app in Microsoft Entra ID because the Conditional Access policy needs to target an existing app. It must also precede the MDCA-specific steps because the session control integration sets up the connection between Microsoft Entra ID and MDCA.
Step 3: From Microsoft Defender for Cloud Apps, modify the Connected apps settings for App1.
After the Conditional Access policy routes sessions to MDCA, you need to configure App1 within MDCA by modifying its Connected apps settings. This step involves ensuring that App1 is properly connected to MDCA, which may include configuring API connectors or verifying that MDCA can monitor the app's activities.
This step is necessary to ensure MDCA has the necessary permissions and configurations to monitor App1. It comes after the Conditional Access policy because the policy enables the integration, and now MDCA needs to be set up to handle the app.
Step 4: From Microsoft Defender for Cloud Apps, create a session policy.
Finally, you create a session policy in MDCA to define the real-time monitoring and control rules for App1. A session policy in MDCA allows you to monitor user activities (e.g., file downloads, data sharing) and apply actions (e.g., block, notify) based on predefined conditions.
This step is the last because it relies on the previous steps: the app must be registered, the Conditional Access policy must route sessions to MDCA, and the Connected apps settings must be configured for MDCA to recognize App1. Only then can you define session policies to enforce real-time monitoring.
Why This Order?
The order ensures a logical flow:
Registering the app in Microsoft Entra ID establishes the app's identity in the tenant.
The Conditional Access policy enables the integration with MDCA by routing sessions through it.
Modifying the Connected apps settings in MDCA ensures the app is properly set up for monitoring.
Creating a session policy in MDCA defines the specific monitoring and control rules for real-time session-level monitoring.
Deviating from this order would result in errors. For example, creating a session policy in MDCA before registering the app in Microsoft Entra ID would fail because MDCA wouldn't recognize the app.
Additional Considerations:
The Microsoft 365 E5 license includes Microsoft Entra ID P2 and Microsoft Defender for Cloud Apps, so no additional licensing is required for this scenario.
If App1 is not a supported app for MDCA's app connectors, additional steps (e.g., using a custom app connector) might be needed, but the question implies App1 can be monitored with the standard process.
Session policies in MDCA can include actions like blocking downloads or requiring step-up authentication, which are applied in real time during the user's session.
Conclusion:The correct order to enable real-time session-level monitoring of App1 using Microsoft Defender for Cloud Apps is:
Register App1 in Microsoft Entra ID.
Create a conditional access policy that has session controls configured.
From Microsoft Defender for Cloud Apps, modify the Connected apps settings for App1.
From Microsoft Defender for Cloud Apps, create a session policy.
Reference:
Microsoft Defender for Cloud Apps documentation: "Session control with Microsoft Defender for Cloud Apps" (Microsoft Learn:https://learn.microsoft.com/en-us/defender-cloud-apps/session-policy) Microsoft Entra ID Conditional Access documentation: "Session controls in Conditional Access" (Microsoft Learn:https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-conditional-access-session) Microsoft Identity and Access Administrator (SC-300) exam study guide, which covers integrating Microsoft Defender for Cloud Apps with Microsoft Entra ID for session-level monitoring.
- 質問一覧「160問」
- 質問1 Azure Monitorを使用して、Azure Active Directory(Azure AD)...
- 質問2 Microsoft 365 テナントがあります。 Microsoft Entra ID で、使...
- 質問3 あなたの会社は最近、Azure Active Directory(Azure AD)特権ID...
- 質問4 User1という名前のユーザーが、次の誤ったパスワードを入力して...
- 質問5 次の表に示すオブジェクトを含むAzureActive Directory(Azure A...
- 質問6 User1 という名前のユーザーを含む Microsoft 365 サブスクリプ...
- 質問7 ネットワークには、Azure AD と同期するオンプレミスの Active D...
- 質問8 オンプレミス ネットワークには、Microsoft Entra Connect を使...
- 質問9 Group3 という名前のグループと、Department1 という名前の管理...
- 質問10 Microsoft365テナントがあります。 すべてのユーザーは携帯電話...
- 質問11 Azure Active Directory(Azure AD)に登録されているApp1という...
- 質問12 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問13 Microsoft 365 E5 テナントがあります。 App1 という名前のクラ...
- 質問14 次の表に示すグループを含む Microsoft 365 E5 サブスクリプショ...
- 質問15 RemoteNetworkl と RemoteNetwork2 という名前の 2 つのリモート...
- 質問16 Azure Monitorを使用して、Azure Active Directory(Azure AD)...
- 質問17 Azure サブスクリプションをお持ちです。 権限を自動的に監視し...
- 質問18 ADatum ユーザーを同期する必要があります。ソリューションは、...
- 質問19 シミュレーション タスク9 Sg-Operations グループのユーザーが ...
- 質問20 Microsoft Defender for Cloud Apps を使用する Microsoft 365 E...
- 質問21 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問22 Microsoft 365 E5 サブスクリプションがあります。サブスクリプ...
- 質問23 contosso.comのデフォルトドメイン名を使用するように新しいMicr...
- 質問24 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問25 contoso.comという名前のAzureActive Directory(Azure AD)テナ...
- 質問26 Azure AD テナントがある ユーザーの同意設定を構成して、ユーザ...
- 質問27 ActiveDirectoryドメインに同期するAzureActive Directory(Azur...
- 質問28 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問29 Group! と Group2 という 2 つのグループと、次の表に示すユーザ...
- 質問30 Microsoft Entra ID Premium ライセンスを使用する Microsoft En...
- 質問31 User1という名前のユーザーを含むcontoso.comという名前のAzureA...
- 質問32 Azure サブスクリプションをお持ちです。 エンタープライズ SaaS...
- 質問33 5,000 人のユーザーを持つ Microsoft 365 テナントがあります。...
- 質問34 Microsoft 365 E5 サブスクリプションがあります。次のタスクを...
- 質問35 Microsoft365テナントとadatum.comという名前のActiveDirectory...
- 質問36 User1 と User2 という名前の 2 人のユーザーを含む Microsoft 3...
- 質問37 条件付きアクセスポリシーを使用するAzureActive Directory(Azu...
- 質問38 あなたの会社には、Contoso East と Contoso West という名前の ...
- 質問39 あなたは、contoso.com という Microsoft Entra テナントを持つ ...
- 質問40 Microsoft365テナントがあります。 資格情報を漏えいしたユーザ...
- 質問41 マーケティング部門のために計画された変更と技術要件を実装する
- 質問42 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問43 多要素認証 (MFA) が強制され、セルフサービス パスワード リセ...
- 質問44 次の表に示すユーザーを含むAzureActive Directory(Azure AD)...
- 質問45 次の表に示す Azure Active Directory (Azure AD) ユーザーを作...
- 質問46 展示に示されているように、Azure Active Directory(Azure AD)...
- 質問47 Microsoft Entra テナントがあります。 特定の外部ドメインのユ...
- 質問48 User1、User2、User3 という 3 人のユーザーが含まれる Microsof...
- 質問49 ネットワークには、Azure ADConnectを使用してcontoso.comという...
- 質問50 ユーザー管理者ロールの計画された変更を満たす必要があります。
- 質問51 認証要件を満たすには、パスワード制限を実装する必要があります
- 質問52 User1 という名前のユーザーと Vault1 という名前の Azure Key V...
- 質問53 Microsoft Entra テナントがあります。 テナントのリスクの高い...
- 質問54 Sub1 という名前の Azure サブスクリプションがあります。 Micro...
- 質問55 次の表に示すユーザーを含むAzureActive Directory(Azure AD)...
- 質問56 Microsoft Office 365 Enterprise E3 ライセンスが割り当てられ...
- 質問57 以下を含む Microsoft 365 サブスクリプションがあります。 * Az...
- 質問58 User! という名前のユーザーを含む Azure サブスクリプションが...
- 質問59 次の表に示す ID を含む Microsoft Entra テナントがあります。 ...
- 質問60 次の表に示すオブジェクトを含むAzureActive Directory(Azure A...
- 質問61 Microsoft Entra テナントをお持ちです。 次の外部 ID 機能を構...
- 質問62 Microsoft Office 365 EnterpriseE3ライセンスが割り当てられて...
- 質問63 Azure Monitorを使用して、Azure Active Directory(Azure AD)...
- 質問64 次の表に示すホストを含むオンプレミスのデータセンターがあ
- 質問65 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問66 LitwareユーザーへのAzureADライセンスの割り当てを構成する必要...
- 質問67 シミュレーション タスク5 Sg-Retail グループに Windows 10/11 ...
- 質問68 Site1 という名前の Microsoft SharePoint Online サイトを含む ...
- 質問69 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問70 Microsoft365テナントがあります。 すべてのユーザーは、Microso...
- 質問71 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問72 Azure Active Directory(Azure AD)テナントがあります。 テナ...
- 質問73 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問74 contoso.comのデフォルトドメイン名を使用するように新しいMicro...
- 質問75 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問76 Microsoft36Sテナントがあります。 高リスクの国のリストを含むH...
- 質問77 漏洩したクレデンシャルの認証要件を満たす必要があります。 あ
- 質問78 役割の割り当てを管理するために使用する役割を特定する必要があ
- 質問79 db1 という名前の Azure SQL データベースを含む Azure サブスク...
- 質問80 Microsoft 365 E5 サブスクリプションをお持ちです。 サブスクリ...
- 質問81 次の表に示すユーザーを含む Microsoft Entra テナントがありま...
- 質問82 ネットワークには、Azure Active Directory(Azure AD)テナント...
- 質問83 クラウドベースのエンタープライズアプリを含むAzureActive Dire...
- 質問84 Azure AD IdentityProtectionが有効になっているconto.so.comと...
- 質問85 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問86 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問87 Azure サブスクリプションをお持ちです。 資格管理から、カスタ...
- 質問88 Log Analytics ワークスペースを作成します。 監査の技術要件を...
- 質問89 User1 という名前のユーザーを含む Microsoft Entra テナントが...
- 質問90 Package1 に対して計画された変更を実装する必要があります。ア...
- 質問91 Site1 という名前の Microsoft SharePoint Online サイトを含む ...
- 質問92 Groups1、Group2、Group3 という 3 つのグループと、次の表に示...
- 質問93 Microsoft 365 E5 サブスクリプションをお持ちです。 アプリ ガ...
- 質問94 AU1 という管理単位を含む Microsoft Entra テナントがあります...
- 質問95 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問96 fabrikam.comという名前のドメインを使用するMicrosoft365テナン...
- 質問97 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問98 委任の要件を満たすには、AzureADでアプリの登録を構成する必要...
- 質問99 Microsoft Entra テナントがあります。 アプリのサインインの継...
- 質問100 Microsoft 365 テナントがあります。 Azure Active Directory (A...
- 質問101 Microsoft 36S サブスクリプションを持っています。サブスクリプ...
- 質問102 ゲスト ユーザーの招待の問題を解決する必要があります。Azure A...
- 質問103 User1 という名前のユーザーを含む Azure Active Directory (Azu...
- 質問104 Microsoft Entra テナントがあります。 多数の新しいアプリがテ...
- 質問105 Azure AD テナントには、次の表に示すユーザーが含まれています...
- 質問106 Microsoft365テナントがあります。 現在、基本認証を使用する電...
- 質問107 contoso.comのSMTPのアドレス空間を使用するMicrosoftExchange組...
- 質問108 Azure Active Directory(Azure AD)テナントがあります。 リス...
- 質問109 Site1 という名前の Microsoft SharePoint Online サイトと次の...
- 質問110 Microsoft 365E5テナントがあります。 App1という名前のクラウド...
- 質問111 User1という名前のユーザーと次の表に示すグループを含むAzureAc...
- 質問112 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問113 contoso.com と fabrikam.com という 2 つの Microsoft Entra テ...
- 質問114 App1という名前のAzureADエンタープライズアプリケーションを含...
- 質問115 シミュレーション タスク1 多要素認証(MFA)を導入する必要があ...
- 質問116 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問117 ネットワークには、Azure Active Directory(Azure AD)テナント...
- 質問118 Microsoft 365 テナントがあります。 資格情報が漏洩したユーザ...
- 質問119 営業部門のユーザーの問題を解決する必要があります。Azure AD ...
- 質問120 contoso.com という名前の Azure AD テナントがあり、All Compan...
- 質問121 Microsoft Defender for Cloud Apps と Yammer をユーザーする M...
- 質問122 Microsoft365テナントがあります。 Azure Active Directory(Azu...
- 質問123 セキュリティのデフォルトが無効になっているAzureActive Direct...
- 質問124 あなたの会社にはMicrosoft365テナントがあります。 同社には300...
- 質問125 Azure Active Directory(Azure AD)テナントがあります。 次の...
- 質問126 Microsoft Entra テナントがあります。 セルフサービス パスワー...
- 質問127 Microsoft Entta ID P2 ライセンスを持つ Microsoft Entra テナ...
- 質問128 Microsoft Entra テナントがあります。 サインイン失敗回数が 10...
- 質問129 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問130 VM1 という名前の仮想マシンを含む Azure サブスクリプションが...
- 質問131 デフォルトのアプリ登録設定を持つAzureActive Directory(Azure...
- 質問132 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問133 Azure AD テナントがあります。 App1 という名前の新しいエンタ...
- 質問134 Microsoft365テナントがあります。 Azure Active Directory(Azu...
- 質問135 Group1の展示に示されているように、Group1という名前のグループ...
- 質問136 ユーザー ID が侵害された可能性について、技術的な要件を満たす...
- 質問137 Azure AD テナントがあります。 テンプレート ファイルをアップ...
- 質問138 次の表に示すオブジェクトを含むAzureActive Directory(Azure A...
- 質問139 Microsoft365テナントがあります。 Azure Active Directory(Azu...
- 質問140 contoso.comという名前のAzureActive Directory(Azure AD)テナ...
- 質問141 Microsoft Defender for Cloud Apps を使用する Microsoft 365 E...
- 質問142 あなたの会社には、contosri.com という名前の Azure Active Dir...
- 質問143 Microsoft365テナントがあります。 すべてのユーザーは、Microso...
- 質問144 監視要件を満たすには、多段階攻撃の検出を構成する必要がありま
- 質問145 あなたの会社には、contoso.comという名前のAzure Active Direct...
- 質問146 次の表に示すグループを含むAzureActive Directory(Azure AD)...
- 質問147 ActiveDirectoryフォレストに同期するAzureActive Directory(Az...
- 質問148 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問149 Microsoft 365 サブスクリプションをお持ちです。 ユーザーが企...
- 質問150 Azure サブスクリプションがあります。 Role1 と Role2 という名...
- 質問151 管理要件を満たすには、LWGroup1グループを作成する必要がありま...
- 質問152 Microsoft 365 E5 サブスクリプションがあります。 Microsoft De...
- 質問153 オンプレミス ネットワークには、Active Directory ドメイン サ...
- 質問154 シミュレーション タスク4 ユーザープロフィールの読み取り権限...
- 質問155 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問156 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問157 ボストンオフィスから接続するユーザーのMFA設定を構成する必要...
- 質問158 Microsoft365テナントがあります。 すべてのユーザーは、Microso...
- 質問159 Microsoft 365 テナントがあります。 すべてのユーザーは携帯電...
- 質問160 新しい Microsoft 365 E5 テナントを作成します。 ユーザーが匿...

