- ホーム
- Microsoft
- SC-300J - Microsoft Identity and Access Administrator (SC-300日本語版)
- Microsoft.SC-300J.v2025-07-03.q137
- 質問77
有効的なSC-300J問題集はJPNTest.com提供され、SC-300J試験に合格することに役に立ちます!JPNTest.comは今最新SC-300J試験問題集を提供します。JPNTest.com SC-300J試験問題集はもう更新されました。ここでSC-300J問題集のテストエンジンを手に入れます。
SC-300J問題集最新版のアクセス
「340問、30% ディスカウント、特別な割引コード:JPNshiken」
オンプレミス ネットワークには、Microsoft Entra Connect を使用して Microsoft Entra テナントと同期する Active Directory ドメインが含まれています。
次の要件を満たすように Microsoft Entra Connect を構成する必要があります。
* Microsoft Entra サインインは、Active Directory ドメイン コントローラーによって認証される必要があります。
* Active Directory ドメイン ユーザーは、Microsoft Entra セルフサービス パスワード リセット (SSPR) を使用できる必要があります。
* 管理上の労力を最小限に抑えます。
各要件には何を使用すればよいですか? 回答するには、回答領域で適切なオプションを選択してください。

次の要件を満たすように Microsoft Entra Connect を構成する必要があります。
* Microsoft Entra サインインは、Active Directory ドメイン コントローラーによって認証される必要があります。
* Active Directory ドメイン ユーザーは、Microsoft Entra セルフサービス パスワード リセット (SSPR) を使用できる必要があります。
* 管理上の労力を最小限に抑えます。
各要件には何を使用すればよいですか? 回答するには、回答領域で適切なオプションを選択してください。

正解:
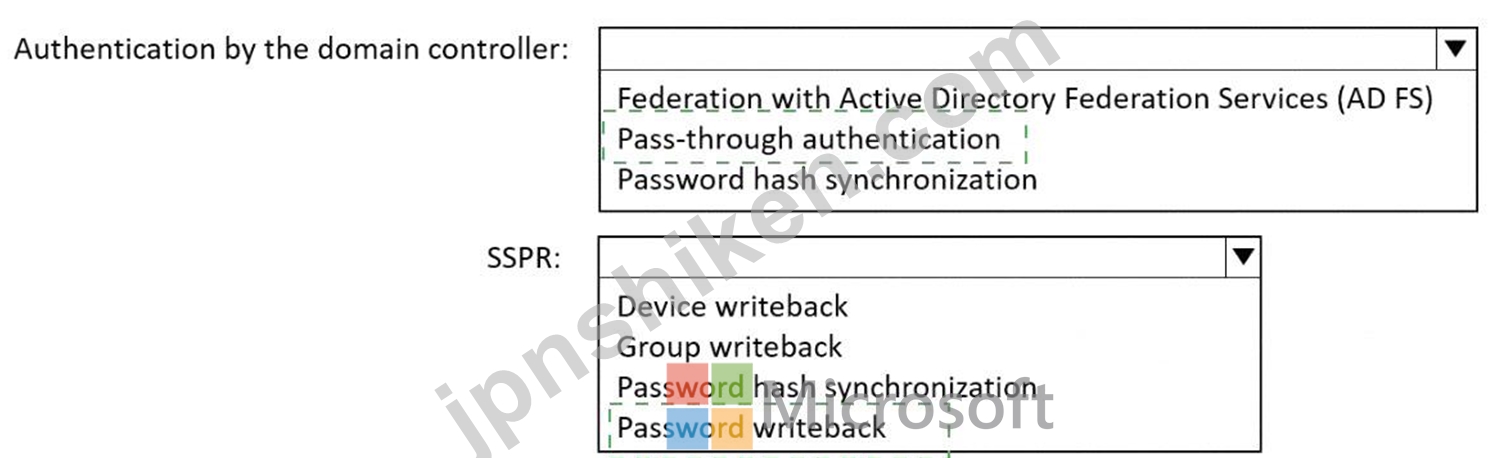
Explanation:
Microsoft Entra sign-ins must be authenticated by an Active Directory domain controller: Pass-through authentication Active Directory domain users must be able to use Microsoft Entra self-service password reset (SSPR):
Password writeback
Let's break this down step by step based on Microsoft Entra Connect, authentication methods, and SSPR requirements, as outlined in Microsoft Identity and Access Administrator documentation.
Requirement 1: Microsoft Entra sign-ins must be authenticated by an Active Directory domain controller
* Understanding the Requirement:
* The requirement states that Microsoft Entra sign-ins must be authenticated by an on-premises Active Directory domain controller. This means that the authentication process must occur on- premises rather than in the cloud.
* Microsoft Entra Connect supports several authentication methods for hybrid identity:
* Password Hash Synchronization (PHS):Password hashes are synchronized to Microsoft Entra ID, and authentication occurs in the cloud. This does not meet the requirement because the domain controller is not involved in the authentication process.
* Pass-through Authentication (PTA):Users sign in to Microsoft Entra ID, but the authentication request is passed to an on-premises Active Directory domain controller for validation. This meets the requirement because the domain controller performs the authentication.
* Federation with Active Directory Federation Services (AD FS):Users are redirected to an on-premises AD FS server, which authenticates them against the domain controller. This also meets the requirement because the domain controller is involved via AD FS.
* Comparing the Options:
* Federation with Active Directory Federation Services (AD FS):
* AD FS provides federated authentication, where users are redirected to an on-premises AD FS server for authentication. The AD FS server communicates with the domain controller to validate credentials.
* This meets the requirement because the domain controller authenticates the user.
* However, AD FS requires significant infrastructure (e.g., AD FS servers, Web Application Proxy servers) and ongoing maintenance, which increases administrative effort.
* Pass-through Authentication (PTA):
* PTA allows Microsoft Entra ID to pass the authentication request directly to an on- premises domain controller via a lightweight agent installed on a server in the on-premises environment.
* This meets the requirement because the domain controller performs the authentication.
* PTA is simpler to deploy and manage than AD FS. It requires only the Microsoft Entra Connect server and the PTA agent, with no additional infrastructure like AD FS servers.
This aligns with the requirement to "minimize administrative effort."
* Minimizing Administrative Effort:
* The question emphasizes minimizing administrative effort.
* AD FS requires deploying and maintaining a federation infrastructure, including AD FS servers, Web Application Proxy servers, certificates, and load balancers. This involves significant administrative overhead.
* PTA, on the other hand, is lightweight. It uses the existing Microsoft Entra Connect server and a small agent, with no additional infrastructure required. It also supports high availability by allowing multiple PTA agents.
* Therefore, PTA is the better choice to minimize administrative effort while meeting the requirement.
* Conclusion for Requirement 1:
* Both options meet the requirement for domain controller authentication, but PTA is the better choice because it minimizes administrative effort.
* The correct answer for this requirement isPass-through authentication.
Requirement 2: Active Directory domain users must be able to use Microsoft Entra self-service password reset (SSPR)
* Understanding the Requirement:
* The requirement states that Active Directory domain users must be able to use Microsoft Entra self-service password reset (SSPR).
* SSPR allows users to reset their passwords via a web portal (e.g., aka.ms/sspr) without contacting an administrator. In a hybrid environment (with Microsoft Entra Connect), SSPR must be configured to work with on-premises Active Directory accounts.
* For SSPR to work in a hybrid environment, the password reset must be written back to the on- premises Active Directory so that the user's password is updated in both Microsoft Entra ID and Active Directory.
* Understanding the Options:
* Device writeback:
* Device writeback synchronizes device objects (e.g., for Conditional Access or Windows Hello for Business) between Microsoft Entra ID and Active Directory.
* This is unrelated to SSPR or password management.
* Group writeback:
* Group writeback synchronizes Microsoft 365 groups from Microsoft Entra ID to Active Directory, allowing on-premises applications to use these groups.
* This is also unrelated to SSPR or password management.
* Password hash synchronization:
* Password hash synchronization (PHS) synchronizes the hash of a user's Active Directory password to Microsoft Entra ID, enabling cloud authentication.
* While PHS is often used in hybrid environments, it only synchronizes passwords from Active Directory to Microsoft Entra ID (one-way). It does not support writing password changes (e.g., from SSPR) back to Active Directory, which is required for SSPR in a hybrid environment.
* Password writeback:
* Password writeback is a feature of Microsoft Entra Connect that allows password changes made in Microsoft Entra ID (e.g., via SSPR) to be written back to the on-premises Active Directory.
* This is specifically designed for SSPR in hybrid environments. When a user resets their password using SSPR, the new password is written back to Active Directory, ensuring the user's credentials are consistent across both environments.
* Password writeback requires Microsoft Entra ID P1 or P2 licenses and must be enabled in Microsoft Entra Connect.
* SSPR in a Hybrid Environment:
* For SSPR to work for Active Directory domain users, password writeback must be enabled.
Without password writeback, a password reset in Microsoft Entra ID would not update the on- premises Active Directory, rendering the user unable to sign in to on-premises resources.
* Password writeback ensures that when a user resets their password via SSPR, the new password is synchronized to Active Directory, meeting the requirement.
* Conclusion for Requirement 2:
* The only option that enables SSPR for Active Directory domain users in a hybrid environment is Password writeback.
* The other options (Device writeback, Group writeback, Password hash synchronization) do not support writing password changes back to Active Directory, which is necessary for SSPR.
Final Answer Summary:
* Microsoft Entra sign-ins must be authenticated by an Active Directory domain controller:Pass- through authentication (meets the requirement and minimizes administrative effort compared to AD FS).
* Active Directory domain users must be able to use Microsoft Entra self-service password reset (SSPR):Password writeback (required for SSPR in a hybrid environment).
References:
Microsoft Entra Connect documentation: "Choose the right authentication method" (Microsoft Learn:
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/choose-ad-authn) Microsoft Entra Connect documentation: "Password writeback for SSPR" (Microsoft Learn:https://learn.
microsoft.com/en-us/entra/identity/authentication/howto-sspr-writeback) Microsoft Identity and Access Administrator (SC-300) exam study guide, which covers Microsoft Entra Connect authentication methods and SSPR configuration in hybrid environments.
- 質問一覧「137問」
- 質問1 User1 という名前のユーザーを含む Azure AD テナントがあります...
- 質問2 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問3 Microsoft365テナントがあります。 すべてのユーザーは携帯電話...
- 質問4 Package1 に対して計画された変更を実装する必要があります。ア...
- 質問5 監視要件を満たすには、多段階攻撃の検出を構成する必要がありま
- 質問6 Log Analytics ワークスペースを作成します。 監査の技術要件を...
- 質問7 User1 という名前のユーザーを含む Sub1 という名前の Azure サ...
- 質問8 Microsoft365テナントがあります。 資格情報を漏えいしたユーザ...
- 質問9 Microsoft Office 365 Enterprise E3 ライセンスが割り当てられ...
- 質問10 Department1という名前の管理ユニットを含むAzureActive Directo...
- 質問11 ボストンオフィスから接続するユーザーのMFA設定を構成する必要...
- 質問12 あなたの会社には、contosri.com という名前の Azure Active Dir...
- 質問13 セキュリティのデフォルトが無効になっているAzureActive Direct...
- 質問14 contoso.com と fabrikam.com という 2 つの Microsoft Entra テ...
- 質問15 Azure サブスクリプション、Google Cloud Platform (GCP) アカウ...
- 質問16 次の仮想マシン名を含む Azure サブスクリプションがあります: V...
- 質問17 ユーザー ID が侵害された可能性について、技術的な要件を満たす...
- 質問18 Azure AD IdentityProtectionが有効になっているconto.so.comと...
- 質問19 新しいユーザーにライセンスを割り当てる必要があります。 デー
- 質問20 Azure Monitorを使用して、Azure Active Directory(Azure AD)...
- 質問21 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問22 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問23 Group1の展示に示されているように、Group1という名前のグループ...
- 質問24 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問25 会社では、2 つの新しい Microsoft 365 ES サブスクリプションと...
- 質問26 ネットワークには、Microsoft Entra Connect を使用して Microso...
- 質問27 タスク 3 Linkedln アプリケーションをリソースとして Sales and...
- 質問28 Sub1 という名前の Azure サブスクリプションがあります。 Micro...
- 質問29 Microsoft Office 365 EnterpriseE3ライセンスが割り当てられて...
- 質問30 Azure Active Directory(Azure AD)テナントがあります。 次の...
- 質問31 User1 という名前のユーザーを含む Azure Active Directory (Azu...
- 質問32 オンプレミス ネットワークには、Azure AD Connect を使用して A...
- 質問33 Azure Active Directory(Azure AD)テナントがあります。 過去...
- 質問34 Azure Active Directory PremiumP2テナントがあります。 LogAnal...
- 質問35 App1 の計画された変更と技術要件を満たす必要があります。 何を...
- 質問36 Microsoft 365 E5 サブスクリプションがあります。 ユーザーは、...
- 質問37 Azure Active Directory(Azure AD)テナントがあります。 過去...
- 質問38 SSPR の計画された変更を実装します。 User3 が SSPR を使用しよ...
- 質問39 contoso.comという名前のMicrosoft365テナントがあります。 ゲス...
- 質問40 ActiveDirectoryドメインに同期するAzureActive Directory(Azur...
- 質問41 あなたの会社は最近、Azure Active Directory(Azure AD)特権ID...
- 質問42 Microsoft Entra ID Premium ライセンスを使用する Microsoft En...
- 質問43 マーケティング部門のために計画された変更と技術要件を実装する
- 質問44 Microsoft 365 テナントがあります。 条件付きアクセス ポリシー...
- 質問45 Azure AD テナントには、次の表に示すユーザーが含まれています...
- 質問46 User1 と User2 という名前の 2 人のユーザーを含む Azure AD テ...
- 質問47 Terms1 という名前の使用条件 (ToU) とアクセス パッケージを含...
- 質問48 次の表に示すユーザーを含む Azure サブスクリプションがありま...
- 質問49 次の表に示すホストを含むオンプレミスのデータセンターがあ
- 質問50 You have a Microsoft Entra tenant that contains the groups s...
- 質問51 Microsoft Entra テナントがあります。 多数の新しいアプリがテ...
- 質問52 contoso.com という名前の Azure AD テナントがあり、All Compan...
- 質問53 App1 という名前の Web アプリを含む Microsoft 365 E5 サブスク...
- 質問54 contoso.comのSMTPのアドレス空間を使用するMicrosoftExchange組...
- 質問55 Azure AD テナントがあります。 App1 という名前の新しいエンタ...
- 質問56 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問57 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問58 ゲスト ユーザーの招待の問題を解決する必要があります。Azure A...
- 質問59 Azure AD テナントがある ユーザーの同意設定を構成して、ユーザ...
- 質問60 Site1 という名前の Microsoft SharePoint Online サイトと次の...
- 質問61 タスク6 Sg-Executive のメンバーが会社のアプリにアクセスでき...
- 質問62 VM1 という名前の仮想マシンと Vault1 という名前の Azure Key V...
- 質問63 Appl という名前のオンプレミス アプリがあります。Microsoft En...
- 質問64 contoso.comという名前のAzureActive Directory(Azure AD)テナ...
- 質問65 新しい Azure AD テナントをデプロイする予定です。 テナントに...
- 質問66 役割の割り当てを管理するために使用する役割を特定する必要があ
- 質問67 contoso.com という名前の Microsoft Entra テナントにリンクさ...
- 質問68 展示に示されているように、Azure Active Directory(Azure AD)...
- 質問69 App1という名前のAzureADエンタープライズアプリケーションを含...
- 質問70 5,000 人のユーザーを持つ Microsoft 365 テナントがあります。...
- 質問71 タスク 4 ユーザー プロファイルの読み取り権限を必要とするアプ...
- 質問72 Microsoft36Sテナントがあります。 高リスクの国のリストを含むH...
- 質問73 タスク 2 Salesforce アプリケーションにアクセスできるゲストユ...
- 質問74 Automation1 という名前の Azure Automation アカウントと Vault...
- 質問75 contoso.com と fabhkam.com という 2 つの Microsoft Entra テ...
- 質問76 Azure Active Directory(Azure AD)テナントがあります。 次の...
- 質問77 オンプレミス ネットワークには、Microsoft Entra Connect を使...
- 質問78 Microsoft365テナントがあります。 すべてのユーザーは携帯電話...
- 質問79 ネットワークには、contoso.com という名前のオンプレミスの Act...
- 質問80 ネットワークには、Microsoft Entra テナントと同期するオンプレ...
- 質問81 米国東部 Azure リージョンに Managed1 というユーザー割り当て...
- 質問82 Microsoft 365 E5 サブスクリプションをお持ちです。 Gateway1 ...
- 質問83 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問84 SecAdmin1という名前のユーザーを含むAzureActive Directory(Az...
- 質問85 注: この質問は、同じシナリオを提示する一連の質問の一部です。...
- 質問86 次の表に示すリソースを含むAzureサブスクリプションがあります...
- 質問87 次の表に示すリソースを含む contoso.com という名前の Azure AD...
- 質問88 次のクラウド プラットフォームのアカウントがあります。 * アズ...
- 質問89 contoso.comのデフォルトドメイン名を使用するように新しいMicro...
- 質問90 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問91 User1 という名前のユーザーを含む Microsoft 365 ES サブスクリ...
- 質問92 Microsoft Entra テナントをお持ちです。 次の外部 ID 機能を構...
- 質問93 LitwareユーザーへのAzureADライセンスの割り当てを構成する必要...
- 質問94 User1 という名前のユーザーを含む Microsoft 365 サブスクリプ...
- 質問95 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問96 contoso.onmicrosoft.comのドメイン名を使用する新しいMicrosoft...
- 質問97 ActiveDirectoryフォレストに同期するAzureActive Directory(Az...
- 質問98 User1 という名前のユーザーを含む Microsoft Entra テナントが...
- 質問99 計画された変更をサポートし、MFA の技術要件を満たす必要があり...
- 質問100 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問101 Sub1 ilia1 という名前の Azure サブスクリプションがあり、stor...
- 質問102 会社では、ユーザーが企業アプリケーションにアクセスする前に、
- 質問103 Microsoft Entra テナントがあります。 アプリのサインインの継...
- 質問104 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問105 User1、User2、およびUser3という名前の3人のユーザーを含むMicr...
- 質問106 User1 という名前のユーザーが Microsoft Defender for Cloud Ap...
- 質問107 Microsoft365テナントがあります。 Azure Active Directory(Azu...
- 質問108 litware.com の計画された変更を実装する必要があります。何を設...
- 質問109 Azure Monitorを使用して、Azure Active Directory(Azure AD)...
- 質問110 次の表に示すオブジェクトを含むAzureActive Directory(Azure A...
- 質問111 Microsoft Entra ID P1 ライセンスを持つ Microsoft Entra テナ...
- 質問112 以下を含む Microsoft 365 サブスクリプションがあります。 * Az...
- 質問113 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問114 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問115 ネットワークには、Azure ADConnectを使用してcontoso.comという...
- 質問116 Microsoft 365 テナントがあります。 資格情報が漏洩したユーザ...
- 質問117 ネットワークには、Azure Active Directory(Azure AD)テナント...
- 質問118 次の表に示す Azure リソースがあります。 (Exhibit) RG1 の共同...
- 質問119 新しい Microsoft 365 E5 テナントを作成します。 ユーザーが匿...
- 質問120 Azure AD テナントがあります。 テンプレート ファイルをアップ...
- 質問121 漏洩したクレデンシャルの認証要件を満たす必要があります。 あ
- 質問122 ユーザーが High 70 サインイン アラートをトリガーしたときにア...
- 質問123 Microsoft 365 E5 サブスクリプションがあります。次のタスクを...
- 質問124 User1という名前のユーザーと次の表に示すグループを含むAzureAc...
- 質問125 認証要件とアクセス要件を満たすには、オンプレミスアプリケーシ
- 質問126 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問127 Microsoft 365 テナントがあります。 Microsoft Entra ID で、使...
- 質問128 あなたの会社にはMicrosoft365テナントがあります。 同社には300...
- 質問129 contoso.com という名前の Azure Active Directory (Azure AD) ...
- 質問130 Microsoft365テナントがあります。 ユーザーは、それぞれのユー...
- 質問131 Microsoft 365 サブスクリプションをお持ちです。 次の構成を持...
- 質問132 Azure Active Directory Premium Plan 2 ライセンスを持つ Azure...
- 質問133 Microsoft Entra テナントがあります。 テナントのリスクの高い...
- 質問134 Microsoft 365 E5 サブスクリプションをお持ちです。 アプリ ガ...
- 質問135 ネットワークには、Azure AD テナントに同期するオンプレミスの ...
- 質問136 User1、User2、User3 という 3 人のユーザーが含まれる Microsof...
- 質問137 管理要件を満たすには、LWGroup1グループを作成する必要がありま...

