- ホーム
- Microsoft
- MS-102J - Microsoft 365 Administrator (MS-102日本語版)
- Microsoft.MS-102J.v2025-06-30.q223
- 質問9
有効的なMS-102J問題集はJPNTest.com提供され、MS-102J試験に合格することに役に立ちます!JPNTest.comは今最新MS-102J試験問題集を提供します。JPNTest.com MS-102J試験問題集はもう更新されました。ここでMS-102J問題集のテストエンジンを手に入れます。
MS-102J問題集最新版のアクセス
「527問、30% ディスカウント、特別な割引コード:JPNshiken」
ホットスポット
ネットワークにはオンプレミスの Active Directory ドメインが含まれています。
Microsoft 365 E5 サブスクリプションをお持ちです。
ディレクトリ同期を実装する予定です。
ドメインの潜在的な同期の問題を特定する必要があります。解決策では、最小権限の原則を使用する必要があります。
何を使うべきでしょうか? 回答するには、回答エリアで適切なオプションを選択してください。
注意: 正しい選択ごとに 1 ポイントが付与されます。

ネットワークにはオンプレミスの Active Directory ドメインが含まれています。
Microsoft 365 E5 サブスクリプションをお持ちです。
ディレクトリ同期を実装する予定です。
ドメインの潜在的な同期の問題を特定する必要があります。解決策では、最小権限の原則を使用する必要があります。
何を使うべきでしょうか? 回答するには、回答エリアで適切なオプションを選択してください。
注意: 正しい選択ごとに 1 ポイントが付与されます。

正解:
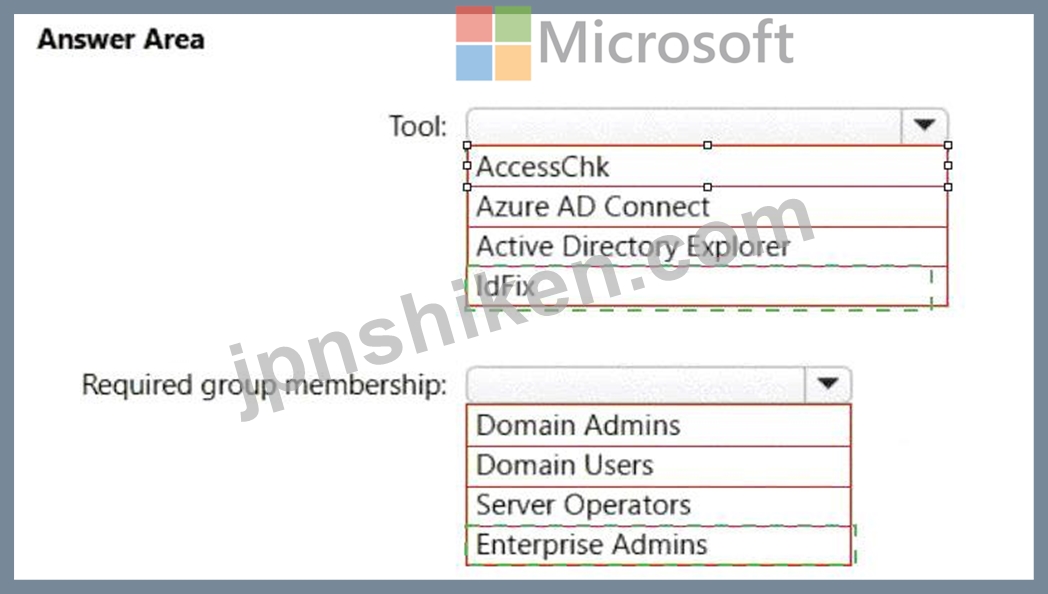
Explanation:

Box 1: IdFix
Query and fix invalid object attributes with the IdFix tool
Microsoft is working to reduce the time required to remediate identity issues when onboarding to Microsoft
365. A portion of this effort is intended to address the time involved in remediating the Windows Server Active Directory (Windows Server AD) errors reported by the directory synchronization tools such as Azure AD Connect and Azure AD Connect cloud sync. The focus of IdFix is to enable you to accomplish this task in a simple, expedient fashion.
The IdFix tool provides you the ability to query, identify, and remediate the majority of object synchronization errors in your Window's Server AD forests in preparation for deployment to Microsoft 365.
The utility does not fix all errors, but it does find and fix the majority. This remediation will then allow you to successfully synchronize users, contacts, and groups from on-premises Active Directory into Microsoft 365.
Note: IdFix might identify errors beyond those that emerge during synchronization. The most common example is compliance with rfc 2822 for smtp addresses. Although invalid attribute values can be synchronized to the cloud, the product group recommends that these errors be corrected.
Incorrect:
* AccessChk
Box 2: Enterprise Admins
IdFix permissions requirements
The user account that you use to run IdFix must have read and write access to the AD DS domain.
If you aren't sure if your user account meets these requirements, and you're not sure how to check, you can still download and run IdFix. If your user account doesn't have the right permissions, IdFix will simply display an error when you try to run it.
* Enterprise Admins
The Enterprise Admins group exists only in the root domain of an Active Directory forest of domains. The group is a Universal group if the domain is in native mode. The group is a Global group if the domain is in mixed mode. Members of this group are authorized to make forest-wide changes in Active Directory, like adding child domains.
Incorrect:
* Domain Admins
Members of the Domain Admins security group are authorized to administer the domain. By default, the Domain Admins group is a member of the Administrators group on all computers that have joined a domain, including the domain controllers. The Domain Admins group is the default owner of any object that's created in Active Directory for the domain by any member of the group. If members of the group create other objects, such as files, the default owner is the Administrators group.
* Server Operator
Server Operators can log on to a server interactively; create and delete network shares; start and stop services; back up and restore files; format the hard disk of the computer; and shut down the computer. Any service that accesses the system has the Service identity.
* Domain Users - too few permissions
The Domain Users group includes all user accounts in a domain. When you create a user account in a domain, it's automatically added to this group.
Reference:
https://microsoft.github.io/idfix/
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups
- 質問一覧「223問」
- 質問1 Microsoft 365 サブスクリプションをお持ちです。 サービス デス...
- 質問2 Microsoft 365 サブスクリプションをお持ちです。 Microsoft 365...
- 質問3 デバイス管理に Microsoft Endpoint Manager を使用する Microso...
- 質問4 3 月の時点で、各オフィスのコンピューターはいつまで Microsoft...
- 質問5 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問6 Microsoft 365 サブスクリプションをお持ちです。 次の図に示す...
- 質問7 あなたの会社は Microsoft 365 E5 サブスクリプションを持ってい...
- 質問8 Microsoft 365 サブスクリプションをお持ちです。 App1 と App2 ...
- 質問9 ホットスポット ネットワークにはオンプレミスの Active Directo...
- 質問10 100 台の Windows 10 デバイスを含む Microsoft 365 E5 テナント...
- 質問11 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問12 Microsoft Defender for Endpoint を使用する Microsoft 365 E5 ...
- 質問13 次の表に示すユーザーを含む Azure AD のハイブリッド デプロイ...
- 質問14 Microsoft 365 E5 サブスクリプションをお持ちです。 アプリケー...
- 質問15 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問16 あなたの会社には複数のオフィスがあります。 デバイス管理に Mi...
- 質問17 Microsoft 365 テナントがあります。 会社のポリシーでは、すべ...
- 質問18 Microsoft 365 E5 サブスクリプションをお持ちです。 あなたは、...
- 質問19 User1 という名前のユーザーを含む Microsoft 365 E5 テナントが...
- 質問20 ホットスポット 次の表に示すユーザーを含む Microsoft 365 E5 ...
- 質問21 会社には、contoso.com という名前の Microsoft Entra テナント...
- 質問22 Admin1 と Admin2 という名前の 2 人のユーザーを含む Microsoft...
- 質問23 Microsoft 365 E5 テナントがあります。 業界規制により、テナン...
- 質問24 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問25 次の表に示すデバイスを含む Microsoft 365 E5 サブスクリプショ...
- 質問26 ネットワークには 3 つの Active Directory フォレストが含まれ...
- 質問27 ホットスポット Microsoft 365 サブスクリプションをお持ちです...
- 質問28 ホットスポット 次の表に示すユーザーを含む Microsoft 365 E5 ...
- 質問29 ネットワークには 3 つの Active Directory フォレストが含まれ...
- 質問30 Microsoft Azure Advanced Threat Protection (Azure ATP) を実...
- 質問31 次の表に示すデバイスを含む Microsoft 365 E5 サブスクリプショ...
- 質問32 サポート技術者がモントリオール オフィスのモバイル デバイスの...
- 質問33 Microsoft 365 E5 テナントがあります。 次の要件を満たす監視ソ...
- 質問34 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問35 User1 と User2 という名前の 2 人のユーザーと、次の表に示すグ...
- 質問36 Microsoft Defender for Office 365 を使用する Microsoft 365 ...
- 質問37 ネットワークには、contoso.com という名前のオンプレミスの Act...
- 質問38 Microsoft 365 E5 サブスクリプションをお持ちです。 次の図に示...
- 質問39 Microsoft 365 E5 サブスクリプションがあります。DLP1 という名...
- 質問40 ホットスポット Microsoft 365 サブスクリプションをお持ちです...
- 質問41 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーが...
- 質問42 ホットスポット User1 という名前のユーザーを含む Microsoft 36...
- 質問43 Microsoft 365 E5 サブスクリプションをお持ちです。 月曜日に、...
- 質問44 User1 という名前のユーザーを含む Microsoft 365 E5 サブスクリ...
- 質問45 Microsoft 365 E5 サブスクリプションをお持ちです。サブスクリ...
- 質問46 Microsoft Intune に登録されたデバイスを含む Microsoft 365 テ...
- 質問47 Microsoft 365 サブスクリプションがあり、Microsoft Defender f...
- 質問48 Microsoft 365 E5 テナントがあります。 機密ラベルは、機密ラベ...
- 質問49 Microsoft 365 サブスクリプションをお持ちです。 Microsoft Pur...
- 質問50 部門内のユーザーが部門の Microsoft SharePoint Online サイト...
- 質問51 オンプレミス ネットワークには、Contoso.com という名前の Acti...
- 質問52 ネットワークには Active Directory フォレストが含まれています...
- 質問53 ネットワークには、Azure AD と同期されている adatum.com とい...
- 質問54 Microsoft 365 サブスクリプションをお持ちです。 onmicrosoft.c...
- 質問55 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問56 あなたの会社は、App1 という名前のクラウド アプリを購入します...
- 質問57 Microsoft 365 E5 サブスクリプションをお持ちです。 次の要件を...
- 質問58 Microsoft 365 E5 サブスクリプションがあり、Microsoft Defende...
- 質問59 あなたは Contoso, Ltd. という名前の会社で働いています。 Cont...
- 質問60 Microsoft 365 E5 サブスクリプションをお持ちです。 利用可能な...
- 質問61 Microsoft 365 E5 サブスクリプションをお持ちです。 サブスクリ...
- 質問62 ホットスポット 次の表に示すユーザーを含む contoso.com という...
- 質問63 次の表に示すグループを含む Microsoft 365 テナントがあります...
- 質問64 Device1 という名前の Windows 10 デバイスと、次の表に示す Mic...
- 質問65 Microsoft 365 サブスクリプションをお持ちです。 Exchange 管理...
- 質問66 オンプレミス ネットワークには Active Directory ドメインが含...
- 質問67 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問68 User1 にどの役割を割り当てるべきですか? 利用可能な選択肢 (正...
- 質問69 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問70 次の図に示すグループを含む Microsoft Entra テナントがありま...
- 質問71 Microsoft 365 E5 サブスクリプションをお持ちです。 次の図に示...
- 質問72 contoso.com という名前の Azure AD テナントを使用する Microso...
- 質問73 デバイス管理に Microsoft エンドポイント マネージャーを使用す...
- 質問74 Microsoft Intune に登録された 200 台の Android デバイスを含...
- 質問75 Microsoft 365 E5 サブスクリプションをお持ちです。 グループの...
- 質問76 Microsoft 365 Defender ポータルでアラートを確認しています。 ...
- 質問77 Microsoft 365 E5 サブスクリプションがあり、その中に User1 と...
- 質問78 技術要件を満たすには、安全な添付ファイル ポリシーを作成する
- 質問79 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問80 Intune の技術要件と計画された変更を満たす必要があります。 あ...
- 質問81 Microsoft Defender for Cloud Apps を使用する Microsoft 365 E...
- 質問82 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問83 次のユーザーを含む Microsoft 365 E5 サブスクリプションがあり...
- 質問84 次の表に示すコンプライアンス ポリシーを含む Microsoft 365 テ...
- 質問85 User1 という名前のユーザーを含む Microsoft 365 E5 サブスクリ...
- 質問86 100 台の Windows 10 デバイスを含む Microsoft 365 テナントが...
- 質問87 Montreal Users OU と Seattle Users OU の計画された変更をサポ...
- 質問88 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーは...
- 質問89 あなたの会社は 5 つの都市にオフィスを構えています。 会社には...
- 質問90 Microsoft および SharePoint Online に対して秘密度ラベルのサ...
- 質問91 あなたの会社には、オンプレミスのデータセンターからすべてのア
- 質問92 Microsoft 365 E5 テナントがあります。 ユーザーは次の場所にデ...
- 質問93 次の表のユーザーを含む Microsoft 365 サブスクリプションがあ...
- 質問94 Microsoft 365 E5 サブスクリプションをお持ちです。 過去 7 日...
- 質問95 Microsoft Defender XDR が含まれる Microsoft 365 サブスクリプ...
- 質問96 Microsoft 36S E5 サブスクリプションをお持ちです。 次の表に示...
- 質問97 ニューヨーク事務所の監査人はどの報告書を参照すべきでしょうか
- 質問98 ホットスポット あなたの会社では、100 人のユーザーを含む従来...
- 質問99 contoso.com という名前の Azure AD テナントを使用する Microso...
- 質問100 500 台の Windows 10 デバイスを含む Microsoft 365 E5 テナント...
- 質問101 Microsoft Defender for Office 365 を使用する Microsoft 365 ...
- 質問102 Microsoft Defender for Office 365 を使用し、Mailbox1 という...
- 質問103 Microsoft 365 サブスクリプションをお持ちです。 Microsoft Ent...
- 質問104 Microsoft 365 E5 サブスクリプションをお持ちです。メールが有...
- 質問105 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問106 Microsoft 365 サブスクリプションをお持ちです。 次の要件を満...
- 質問107 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問108 Microsoft Defender for Endpoint が Microsoft Endpoint Manage...
- 質問109 次の表に示すデバイスを含む Microsoft 365 E5 サブスクリプショ...
- 質問110 Microsoft エンドポイント マネージャーに複数のデバイスが登録...
- 質問111 Microsoft E5 サブスクリプションをお持ちです。 Microsoft Exch...
- 質問112 ビジネス向け Microsoft ストアを作成する必要があります。どの...
- 質問113 Azure ATP センサーはどのサーバーにインストールする必要があり...
- 質問114 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーが...
- 質問115 ホットスポット ネットワークには、contoso.com という名前のオ...
- 質問116 Microsoft 365 E5 サブスクリプションをお持ちです。 SecAdmin1 ...
- 質問117 Microsoft 365 E5 サブスクリプションをお持ちです。 すべてのユ...
- 質問118 次の図に示すように、3 つの自動保持ポリシーを持つ Microsoft 3...
- 質問119 Microsoft Defender XDR を使用する Microsoft 365 サブスクリプ...
- 質問120 Microsoft 365 E5 サブスクリプションがあり、Microsoft Defende...
- 質問121 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問122 Microsoft 365 サブスクリプションをお持ちです。 次の表に示す...
- 質問123 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問124 ネットワークには、contoso.com という名前のオンプレミスの Act...
- 質問125 Microsoft Intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問126 Microsoft 365 E5 サブスクリプションをお持ちです。 次の表に示...
- 質問127 Microsoft 365 E5 テナントがあります。 クレジット カード番号...
- 質問128 Microsoft 365 IS サブスクリプションがあり、Microsoft Defende...
- 質問129 次の図に示すように、フィッシング対策ポリシーを構成します。 (...
- 質問130 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問131 あなたの会社では Microsoft Defender for Endpoint を使用して...
- 質問132 Microsoft Defender for Office 365 を使用する Microsoft 365 E...
- 質問133 Microsoft intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問134 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問135 Microsoft 365 E5 テナントがあります。 異常な Microsoft Offic...
- 質問136 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問137 ホットスポット ネットワークには、fabrikam.com という名前の A...
- 質問138 ホットスポット 次の表に示すユーザーを含む Microsoft 365 サブ...
- 質問139 Microsoft Defender for Cloud Apps を使用する Microsoft 365 ...
- 質問140 Office 365 サービスのステータス通知を構成し、サービスと機能...
- 質問141 Microsoft 365 テナントがあります。 Microsoft Intune に登録す...
- 質問142 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問143 Microsoft 365 E5 サブスクリプションをお持ちです。 すべてのデ...
- 質問144 技術要件を満たすために DLP ポリシーを作成する必要があります...
- 質問145 Windows 10 バージョン 21H1 がプレインストールされている新し...
- 質問146 ネットワークには、Azure Active Directory (Azure AD) と同期す...
- 質問147 Microsoft 365 E5 テナントがあります。 テナントの Microsoft ...
- 質問148 Microsoft 365 サブスクリプションをお持ちです。 機密データが...
- 質問149 Microsoft 365 E5 サブスクリプションをお持ちです。 条件付きア...
- 質問150 次の図に示すドメインを含む Microsoft 365 サブスクリプション...
- 質問151 Microsoft 365 サブスクリプションをお持ちです。 過去 1 週間に...
- 質問152 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問153 Microsoft Defender for Cloud Apps を使用する Microsoft 365 E...
- 質問154 ネットワークには、contoso.local という名前のオンプレミスの A...
- 質問155 Microsoft 365 E5 テナントがあります。 ISO 27001:2013 テンプ...
- 質問156 Azure サブスクリプションとオンプレミスの Active Directory ド...
- 質問157 ネットワークには Active Directory ドメインと Azure AD テナン...
- 質問158 Microsoft 365 サブスクリプションをお持ちです。 次の図に示す...
- 質問159 次の表に示すように、Microsoft Intune に登録された 4 台のデバ...
- 質問160 次の表に示すデバイスを含む Microsoft 365 E5 テナントがありま...
- 質問161 Microsoft 36S E5 サブスクリプションをお持ちです。 Group1 と...
- 質問162 法務部門の要件を満たす必要があります。 「セキュリティとセキ
- 質問163 ネットワークには Active Directory ドメインが含まれています。...
- 質問164 オンプレミス ネットワークには Active Directory ドメインが含...
- 質問165 Youi ネットワークには Active Directory ドメインが含まれてい...
- 質問166 EU PII データの技術要件を満たす必要があります。 何を作成する...
- 質問167 Intune で自動登録を構成する必要があります。ソリューションは...
- 質問168 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問169 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問170 Azure Active Directory (Azure AD) で [セキュリティの有効化] ...
- 質問171 大量のドキュメントを検索するための技術要件を満たす必要があり
- 質問172 Microsoft 365 サブスクリプションをお持ちです。 ネットワーク...
- 質問173 セキュリティとセキュリティからコンプライアンス管理センターで
- 質問174 ホットスポット Microsoft 365 テナントを作成します。 次の図に...
- 質問175 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問176 Group1 と Group2 という 2 つのセキュリティ グループを含む Mi...
- 質問177 Microsoft 365 E5 サブスクリプションをお持ちです。 Policy1 と...
- 質問178 あなたの会社には Microsoft 365 E5 テナントがあります。 会社...
- 質問179 Microsoft 365 テナントと LinkedIn 会社ページがあります。 Lin...
- 質問180 次の表に示すグループを含む Microsoft 365 E5 サブスクリプショ...
- 質問181 Microsoft 365 サブスクリプションをお持ちです。 App1 という名...
- 質問182 Admin4 が SSPR を使用できることを確認する必要があります。 ど...
- 質問183 Microsoft 365 テナントがあります。 Microsoft Intune にデバイ...
- 質問184 Microsoft 365 E5 テナントがあります。 次の図に示すように、デ...
- 質問185 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問186 Microsoft 365 のインシデントと勧告を毎月確認する必要がありま...
- 質問187 User1 という名前のユーザーと Site1 という名前の Microsoft Sh...
- 質問188 Microsoft 365 E5 サブスクリプションをお持ちです。サブスクリ...
- 質問189 User1 という名前のユーザーと次の表に示す管理者を含む Microso...
- 質問190 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問191 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問192 ホットスポット ネットワークには、オンプレミスの Active Direc...
- 質問193 セキュリティとセキュリティを使用する Microsoft 365 サブスク...
- 質問194 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーの...
- 質問195 1,000 台の Windows 10 デバイスを含む Microsoft 365 テナント...
- 質問196 注: このセクションには、同じシナリオと問題に関する 1 つ以上...
- 質問197 Microsoft 365 サブスクリプションをお持ちです。 Microsoft 365...
- 質問198 ホットスポット ネットワークにはオンプレミスの Active Directo...
- 質問199 ネットワークには Contoso という名前の Active Directory フォ...
- 質問200 次の表に示すラベルを含む Microsoft 365 E5 サブスクリプション...
- 質問201 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問202 Microsoft J65 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問203 あなたの会社には、contoso.onmicrosoft.com という名前の Azure...
- 質問204 次の図に示す公開された機密ラベルを持つ Microsoft 365 E5 サブ...
- 質問205 Microsoft 365 Enterprise E5 サブスクリプションを持っています...
- 質問206 contoso.com という名前の Azure AD テナントを含む Microsoft 3...
- 質問207 あなたの会社には Microsoft 365 テナントがあります Engineerin...
- 質問208 Microsoft 365 E3 サブスクリプションをお持ちです。 すべてのユ...
- 質問209 次の表に示す使用が含まれる Microsoft 365 ES サブスクリプショ...
- 質問210 Microsoft 365 E5 サブスクリプションがあり、Microsoft Defende...
- 質問211 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問212 Microsoft 365 E5 サブスクリプションがあり、Microsoft Defende...
- 質問213 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問214 ネットワークにはオンプレミスの Active Directory ドメインが含...
- 質問215 User1 と User2 という名前の 2 人のユーザーを含む Microsoft 3...
- 質問216 Microsoft 365 E5 テナントがあります。 ユーザーがマルウェアを...
- 質問217 ドラッグドロップ Group1 と Group2 という 2 つのグループを含...
- 質問218 ネットワークには contoso.local という名前の Active Directory...
- 質問219 あなたの会社には 3 つの本社と 1 つの支社があります。支社は研...
- 質問220 Microsoft Defender for Endpoint を使用する Microsoft 365 サ...
- 質問221 あなたの会社では Microsoft Defender for Endpoint を使用して...
- 質問222 Microsoft Defender for Office 365 を使用する Microsoft 365 ...
- 質問223 注: この質問は、同じシナリオを示す一連の質問の一部です。この...

