- ホーム
- Microsoft
- MS-102J - Microsoft 365 Administrator (MS-102日本語版)
- Microsoft.MS-102J.v2024-06-08.q198
- 質問105
有効的なMS-102J問題集はJPNTest.com提供され、MS-102J試験に合格することに役に立ちます!JPNTest.comは今最新MS-102J試験問題集を提供します。JPNTest.com MS-102J試験問題集はもう更新されました。ここでMS-102J問題集のテストエンジンを手に入れます。
MS-102J問題集最新版のアクセス
「527問、30% ディスカウント、特別な割引コード:JPNshiken」
ホットスポット
Microsoft 365 E5 サブスクリプションをお持ちです。
会社所有のすべての Windows 11 デバイスは Microsoft Defender for Endpoint にオンボードされています。
次の要件を満たすように Defender for Endpoint を構成する必要があります。
* アプリが更新されるまで、脆弱なアプリをブロックします。
* ファイル ハッシュに基づいてアプリケーションの実行可能ファイルをブロックします。
ソリューションでは、管理労力を最小限に抑える必要があります。
それぞれの要件に対して何を構成する必要がありますか?回答するには、回答領域で適切なオプションを選択してください。
注: 正しく選択するたびに 1 ポイントの価値があります。

Microsoft 365 E5 サブスクリプションをお持ちです。
会社所有のすべての Windows 11 デバイスは Microsoft Defender for Endpoint にオンボードされています。
次の要件を満たすように Defender for Endpoint を構成する必要があります。
* アプリが更新されるまで、脆弱なアプリをブロックします。
* ファイル ハッシュに基づいてアプリケーションの実行可能ファイルをブロックします。
ソリューションでは、管理労力を最小限に抑える必要があります。
それぞれの要件に対して何を構成する必要がありますか?回答するには、回答領域で適切なオプションを選択してください。
注: 正しく選択するたびに 1 ポイントの価値があります。

正解:
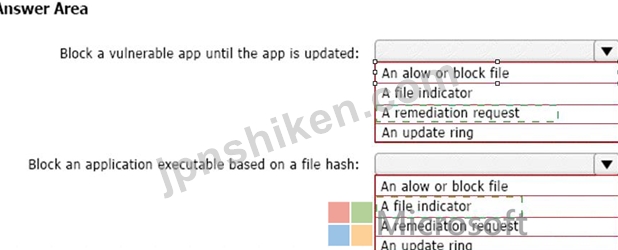
Explanation:
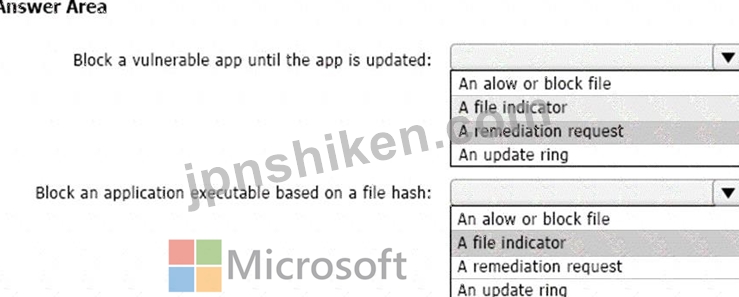
Box 1: A remediation request
Block a vulnerable app until the app is updated.
Block vulnerable applications
How to block vulnerable applications
* Go to Vulnerability management > Recommendations in the Microsoft 365 Defender portal.
* Select a security recommendation to see a flyout with more information.
* Select Request remediation.
* Select whether you want to apply the remediation and mitigation to all device groups or only a few.
* Select the remediation options on the Remediation request page. The remediation options are software update, software uninstall, and attention required.
* Pick a Remediation due date and select Next.
* Under Mitigation action, select Block or Warn. Once you submit a mitigation action, it is immediately applied.
* Review the selections you made and Submit request. On the final page you can choose to go directly to the remediation page to view the progress of remediation activities and see the list of blocked applications.
Box 2: A file indicator
Block an application executable based on a file hash.
While taking the remediation steps suggested by a security recommendation, security admins with the proper permissions can perform a mitigation action and block vulnerable versions of an application. File indicators of compromise (IOC)s are created for each of the executable files that belong to vulnerable versions of that application. Microsoft Defender Antivirus then enforces blocks on the devices that are in the specified scope.
The option to View details of blocked versions in the Indicator page brings you to the Settings > Endpoints > Indicators page where you can view the file hashes and response actions.
Reference:
https://learn.microsoft.com/en-us/microsoft-365/security/defender-vulnerability-management/tvm-block-vuln-ap
- 質問一覧「198問」
- 質問1 オンプレミス ネットワークには Active Directory ドメインが含...
- 質問2 Microsoft エンドポイント マネージャーを使用して管理されてい...
- 質問3 Admin1 と Admin2 という名前の 2 人のユーザーを含む Microsoft...
- 質問4 Intune の技術要件と計画された変更を満たす必要があります。 あ...
- 質問5 Microsoft 365 E5 サブスクリプションをお持ちです。 アプリケー...
- 質問6 次の表に示すグループを含む Microsoft 365 E5 サブスクリプショ...
- 質問7 ホットスポット あなたの会社では、100 人のユーザーを含む従来...
- 質問8 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問9 Microsoft 365 サブスクリプションをお持ちです。 onmicrosoft.c...
- 質問10 Microsoft 365 サブスクリプションをお持ちです。 次の表に示す...
- 質問11 contoso.com という名前の Azure AD テナントを使用する Microso...
- 質問12 Microsoft 365 テナントがあります。 会社のポリシーでは、すべ...
- 質問13 次の表に示すように、Microsoft Intune に登録された 5 台のデバ...
- 質問14 あなたの会社は Microsoft 365 サブスクリプションを持っていま...
- 質問15 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問16 Microsoft 365 E5 サブスクリプションをお持ちです。 次の設定を...
- 質問17 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問18 技術要件を満たすには、米国の PII データを保護する必要があり...
- 質問19 Contoso.com という名前の Microsoft Azure Active Directory (A...
- 質問20 User1 という名前のユーザーを含む Microsoft 365 E5 サブスクリ...
- 質問21 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問22 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問23 ハイブリッド Microsoft Entra テナントにリンクされた Azure サ...
- 質問24 ホットスポット ネットワークには、fabrikam.com という名前の A...
- 質問25 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問26 Microsoft 365 E5 テナントがあります。 次の例に示すように、Re...
- 質問27 ホットスポット Microsoft 365 E5 サブスクリプションをお持ちで...
- 質問28 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問29 Microsoft Defender for Office 365 を使用する Microsoft 365 E...
- 質問30 Microsoft Intune に登録された 1,000 台の iOS デバイスを含む ...
- 質問31 Microsoft E5 サブスクリプションをお持ちです。 Microsoft Exch...
- 質問32 あなたの会社には、User1 という名前のユーザーを含む Microsoft...
- 質問33 Microsoft 365 テナントがあります。 Microsoft Intune に登録す...
- 質問34 技術要件を満たすように情報ガバナンス設定を構成する必要があり
- 質問35 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問36 ハイブリッド Azure Active Directory (Azure AD) テナントと Mi...
- 質問37 Microsoft 365 E5 テナントがあります。 顧客データに関する欧州...
- 質問38 Microsoft Defender for Office 365 を使用する Microsoft 365 ...
- 質問39 Microsoft 365 サブスクリプションをお持ちです。 次の例に示す...
- 質問40 Windows 10 バージョン 21H1 がプレインストールされている新し...
- 質問41 Microsoft 365 E5 テナントがあります。 次の要件を満たすコンプ...
- 質問42 あなたの会社には、contoso.onmicrosoft.com という名前の Azure...
- 質問43 Microsoft 365 E5 テナントがあります。 異常な Microsoft Offic...
- 質問44 Microsoft 365 E5 テナントがあります。 ISO 27001:2013 テンプ...
- 質問45 ホットスポット User1 という名前のユーザーを含む Microsoft 36...
- 質問46 Microsoft intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問47 Microsoft Intune に登録された 500 台の Android デバイスを含...
- 質問48 Microsoft Defender for Office 365 を使用し、User1 という名前...
- 質問49 デバイス管理に Microsoft エンドポイント マネージャーを使用す...
- 質問50 次の表に示すデバイスを含む Microsoft 365 E5 サブスクリプショ...
- 質問51 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問52 あなたの会社は Microsoft 365 サブスクリプションを持っていま...
- 質問53 User1 という名前のユーザーを含む Microsoft 365 サブスクリプ...
- 質問54 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問55 Intune で自動登録を構成する必要があります。ソリューションは...
- 質問56 User1 と User2 という名前の 2 人のユーザーを含む Microsoft 3...
- 質問57 100 台の Windows 10 デバイスを含む Microsoft 365 テナントが...
- 質問58 Microsoft 365 サブスクリプションをお持ちです。 いくつかの Mi...
- 質問59 Microsoft Defender for Cloud Apps を使用する Microsoft 365 ...
- 質問60 Microsoft 365 E5 サブスクリプションをお持ちです。 サブスクリ...
- 質問61 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問62 Microsoft 365 テナントがあります。 Endpoint Protection デバ...
- 質問63 ホットスポット 次の表に示すユーザーを含む Microsoft 365 サブ...
- 質問64 Microsoft Intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問65 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問66 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問67 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問68 ログ分析の技術要件を満たす必要があります。 Microsoft Cloud A...
- 質問69 100 台の Windows 10 デバイスを含む Microsoft 365 E5 テナント...
- 質問70 次の表に示すように、Microsoft エンドポイント マネージャーに ...
- 質問71 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問72 Microsoft 365 E5 サブスクリプションをお持ちです。 SecAdmin1 ...
- 質問73 Project1 に必要なプロセスを評価しています。 プロジェクトのド...
- 質問74 Microsoft 365 テナントがあります。 Azure Active Directory (A...
- 質問75 多要素認証 (MFA) の使用を評価しています。 次の各ステートメン...
- 質問76 Microsoft 365 E5 テナントがあります。 業界規制により、テナン...
- 質問77 あなたの会社にはオンプレミス サーバーと Azure AD テナントが...
- 質問78 Microsoft 365 E5 サブスクリプションをお持ちです。 次の表に示...
- 質問79 Microsoft 365 Defender を使用する Microsoft 365 サブスクリプ...
- 質問80 Microsoft 365 サブスクリプションをお持ちです。 データ損失防...
- 質問81 ホットスポット contoso.com という名前の Azure AD テナントが...
- 質問82 Microsoft 365 サブスクリプションをお持ちです。 次の表に示す...
- 質問83 Microsoft 365 コンプライアンス センターから、Site1 という名...
- 質問84 Microsoft 365 E5 テナントがあります。 次の要件を満たす監視ソ...
- 質問85 Office 365 サービスのステータス通知を構成し、サービスと機能...
- 質問86 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問87 ホットスポット ネットワークにはオンプレミスの Active Directo...
- 質問88 ホットスポット Microsoft 365 テナントがあります。 「保持ラベ...
- 質問89 Microsoft 365 サブスクリプションをお持ちです。 ネットワーク...
- 質問90 Microsoft 365 E5 テナントがあります。 クレジット カード番号...
- 質問91 監査が有効になっている Microsoft 365 E5 サブスクリプションが...
- 質問92 Microsoft 365 サブスクリプションをお持ちです。 Microsoft 365...
- 質問93 次の表に示すアラートを含む Microsoft 365 サブスクリプション...
- 質問94 Microsoft 365 サブスクリプションをお持ちです。 過去 1 週間に...
- 質問95 Azure AD テナントと Microsoft 365 E5 サブスクリプションがあ...
- 質問96 次の表に示すセキュリティ グループを含む Microsoft 365 E5 サ...
- 質問97 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーは...
- 質問98 1,000 台の Windows 10 デバイスを含む Microsoft 365 テナント...
- 質問99 次の表に示すコンプライアンス ポリシーを含む Microsoft 365 テ...
- 質問100 ホットスポット Microsoft 365 サブスクリプションをお持ちです...
- 質問101 Microsoft 365 E5 サブスクリプションをお持ちです。 メールが有...
- 質問102 Microsoft 365 テナントがあります。 Microsoft 365 セキュリテ...
- 質問103 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問104 Microsoft 365 サブスクリプションをお持ちです。 次の図に示す...
- 質問105 ホットスポット Microsoft 365 E5 サブスクリプションをお持ちで...
- 質問106 Windows 10 デバイスを含む Microsoft 365 テナントがあります。...
- 質問107 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーが...
- 質問108 ビジネス向け Microsoft ストアを作成する必要があります。どの...
- 質問109 あなたの会社には Microsoft E5 テナントがあります。 企業は IS...
- 質問110 ホットスポット 次の表に示すユーザーを含む Microsoft 365 E5 ...
- 質問111 Microsoft 365 E5 サブスクリプションをお持ちです。 月曜日に、...
- 質問112 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問113 あなたの会社には 3 つの本社と 1 つの支店があります。支店は研...
- 質問114 Microsoft 365 E5 サブスクリプションをお持ちです。 ユーザーは...
- 質問115 Microsoft 365 ES テナントがあります。 次の図に示すアラートが...
- 質問116 技術要件を満たすように Office on the Web を構成する必要があ...
- 質問117 次の表に示すデバイスを含む Microsoft 365 E5 テナントがありま...
- 質問118 ネットワークには、contoso.com という名前のオンプレミスの Act...
- 質問119 Admin4 が SSPR を使用できることを確認する必要があります。 ど...
- 質問120 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問121 Microsoft Purview コンプライアンス ポータルから、Policy 1 と...
- 質問122 ホットスポット 次の表に示す管理単位を含む Azure AD テナント...
- 質問123 ホットスポット ネットワークには、オンプレミスの Active Direc...
- 質問124 あなたは Contoso, Ltd. という名前の会社で働いています。 Cont...
- 質問125 新しい Microsoft 365 E5 テナントがあります。 Microsoft Excha...
- 質問126 次の表に示すグループを含む Microsoft 365 テナントがあります...
- 質問127 Microsoft 365 E5 サブスクリプションをお持ちです。 すべてのユ...
- 質問128 次の表に示すユーザーを含む Microsoft 365 サブスクリプション...
- 質問129 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問130 Microsoft 365 E5 サブスクリプションをお持ちです。 利用可能な...
- 質問131 Microsoft 365 サブスクリプションをお持ちです。 Exchange 管理...
- 質問132 Microsoft Defender for Endpoint を使用する Microsoft 365 E5 ...
- 質問133 Windows 10 デバイスのコンプライアンス要件を満たす必要があり...
- 質問134 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問135 Microsoft 365 サブスクリプションをお持ちです。 App1 という名...
- 質問136 contoso.com という名前の Azure AD テナントを含む Microsoft 3...
- 質問137 Microsoft 365 サブスクリプションをお持ちです。 [ヘッダーの設...
- 質問138 あなたの会社では Microsoft Defender for Endpoint を使用して...
- 質問139 Microsoft 365 E5 サブスクリプションをお持ちです。 あなたは、...
- 質問140 Montreal Users OU と Seattle Users OU の計画された変更をサポ...
- 質問141 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問142 計画された DLP ポリシーを作成します。 技術要件を満たすように...
- 質問143 ホットスポット あなたの会社では Microsoft Defender for Endpo...
- 質問144 ネットワークには、Azure AD Connect Express 設定を使用して Az...
- 質問145 どのサーバーで Defender for ID センサーを使用する必要があり...
- 質問146 Microsoft 365 サブスクリプションをお持ちです。 App1 と App2 ...
- 質問147 ホットスポット 次の表に示すユーザーを含む Microsoft 365 E5 ...
- 質問148 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問149 あなたの会社には Microsoft 365 E5 テナントがあります。 会社...
- 質問150 Microsoft 365 E5 テナントがあります。 機密ラベルを構成します...
- 質問151 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問152 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問153 Microsoft 365 Defender ポータルでアラートを確認しています。 ...
- 質問154 Microsoft 365 サブスクリプションをお持ちです。 次の要件を満...
- 質問155 Microsoft Intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問156 Microsoft 365 E5 テナントがある データ投げ捨て防止 (DLP) ポ...
- 質問157 オンプレミス ネットワークには、Active Directory ドメインと M...
- 質問158 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問159 Microsoft 365 サブスクリプションをお持ちです。 レポートを確...
- 質問160 次の表に示すデバイスを含む Microsoft 365 E5 テナントがありま...
- 質問161 User1 という名前のユーザーを含む Microsoft 365 E5 テナントが...
- 質問162 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問163 ネットワークには、contoso.com という名前のオンプレミスの Act...
- 質問164 ネットワークには、contoso.local という名前のオンプレミスの A...
- 質問165 あなたの会社には、オンプレミスのデータセンターからすべてのア
- 質問166 Microsoft 365 E5 テナントがあります。 ユーザーがマルウェアを...
- 質問167 Site1 という名前の Microsoft SharePoint Online サイトを含む ...
- 質問168 Microsoft 365 E5 サブスクリプションをお持ちです。 すべてのユ...
- 質問169 Device1 という名前の Windows 10 デバイスと、次の表に示す Mic...
- 質問170 次の表に示すラベルを含む Microsoft 365 E5 サブスクリプション...
- 質問171 User1 という名前のユーザーを含む Azure Active Directory (Azu...
- 質問172 ネットワークには Contoso という名前の Active Directory フォ...
- 質問173 Microsoft 365 テナントがあります。 Endpoint Protection デバ...
- 質問174 営業部門のすべてのユーザーが Project1 と Project2 中に正常に...
- 質問175 Microsoft 365 E5 テナントがあります。 機密情報の種類を含む電...
- 質問176 注: この質問は、同じシナリオを示す一連の質問の一部です。この...
- 質問177 Microsoft Azure Advanced Threat Protection (Azure ATP) を実...
- 質問178 Microsoft Intune を使用する Microsoft 365 E5 テナントがあり...
- 質問179 Microsoft Defender for Endpoint が Microsoft Endpoint Manage...
- 質問180 Device1 という名前の Windows 10 デバイスと、次の表に示す Mic...
- 質問181 次の表に示すグループを含む Microsoft 365 E5 サブスクリプショ...
- 質問182 Azure サブスクリプションとオンプレミスの Active Directory ド...
- 質問183 Sitel という名前の Microsoft SharePoint サイトを含む Microso...
- 質問184 次の表に示すデバイスを含む Microsoft 365 E5 テナントがありま...
- 質問185 Microsoft Defender for Office 365 を使用する Microsoft 365 ...
- 質問186 ホットスポット Microsoft 365 テナントを作成します。 次の図に...
- 質問187 Microsoft 365 サブスクリプションをお持ちです。 一部の外部ユ...
- 質問188 ホットスポット ネットワークにはオンプレミスの Active Directo...
- 質問189 ネットワークには Active Directory ドメインと Azure AD テナン...
- 質問190 Microsoft 365 E5 テナントがあります。 機密ラベルの説明に示さ...
- 質問191 次の表に示すユーザーを含む Microsoft 365 E5 テナントがありま...
- 質問192 Microsoft 365 サブスクリプションをお持ちです。 導入スコアを...
- 質問193 User1 と User2 という名前の 2 人のユーザーと、次の表に示すグ...
- 質問194 ホットスポット Site1 という名前の Microsoft SharePoint サイ...
- 質問195 (Exhibit) SP800 評価には、次の表に示す改善アクションがありま...
- 質問196 Group1 と Group2 という名前の 2 つのグループを含む Microsoft...
- 質問197 次の表に示すユーザーを含む Microsoft 365 E5 サブスクリプショ...
- 質問198 あなたの会社には、contoso.com という名前の Azure AD テナント...

