- ホーム
- Microsoft
- MD-102-JPN - Endpoint Administrator (MD-102日本語版)
- Microsoft.MD-102-JPN.v2024-09-04.q124
- 質問72
有効的なMD-102-JPN問題集はJPNTest.com提供され、MD-102-JPN試験に合格することに役に立ちます!JPNTest.comは今最新MD-102-JPN試験問題集を提供します。JPNTest.com MD-102-JPN試験問題集はもう更新されました。ここでMD-102-JPN問題集のテストエンジンを手に入れます。
MD-102-JPN問題集最新版のアクセス
「330問、30% ディスカウント、特別な割引コード:JPNshiken」
次の表に示すデバイスを含む Microsoft 365 サブスクリプションをお持ちです。

信頼できるファームウェアまたはオペレーティング システム ビルドを実行しているデバイスのみがネットワーク リソースにアクセスできるようにする必要があります。
各デバイスにどのコンプライアンス ポリシー設定を構成する必要がありますか? 答えるには、適切な設定を正しいデバイスにドラッグします。各設定は、1 回、複数回、またはまったく使用されない場合があります。コンテンツを表示するには、ペイン間の分割バーをドラッグするか、スクロールする必要がある場合があります。
注意: 正しい選択ごとに 1 ポイントが付与されます。


信頼できるファームウェアまたはオペレーティング システム ビルドを実行しているデバイスのみがネットワーク リソースにアクセスできるようにする必要があります。
各デバイスにどのコンプライアンス ポリシー設定を構成する必要がありますか? 答えるには、適切な設定を正しいデバイスにドラッグします。各設定は、1 回、複数回、またはまったく使用されない場合があります。コンテンツを表示するには、ペイン間の分割バーをドラッグするか、スクロールする必要がある場合があります。
注意: 正しい選択ごとに 1 ポイントが付与されます。

正解:
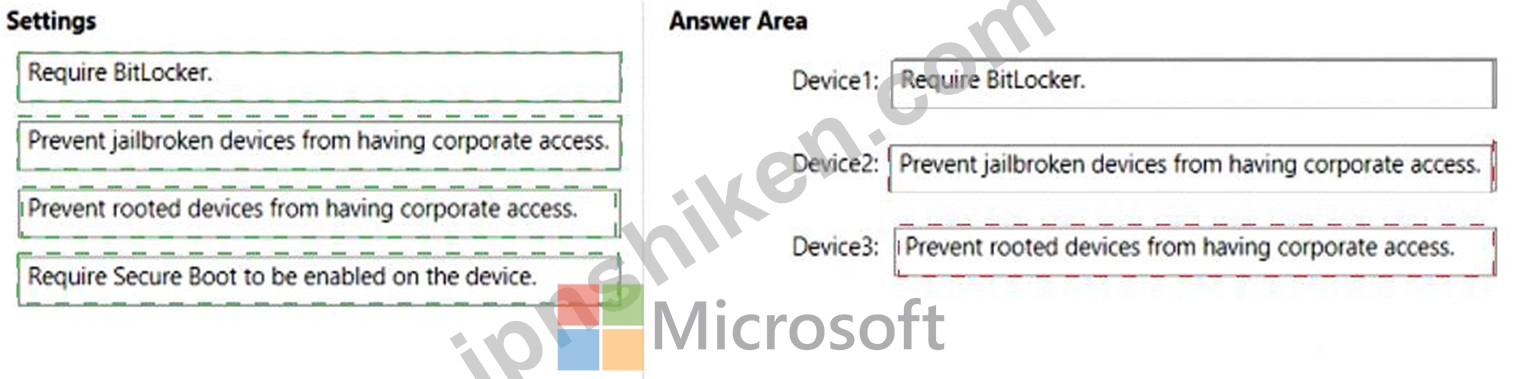
Explanation:
Box 1:
Device Compliance settings for Windows 10/11 in Intune
There are the different compliance settings you can configure on Windows devices in Intune. As part of your mobile device management (MDM) solution, use these settings to require BitLocker, set a minimum and maximum operating system, set a risk level using Microsoft Defender for Endpoint, and more.
Note: Windows Health Attestation Service evaluation rules
Require BitLocker:
Windows BitLocker Drive Encryption encrypts all data stored on the Windows operating system volume.
BitLocker uses the Trusted Platform Module (TPM) to help protect the Windows operating system and user data. It also helps confirm that a computer isn't tampered with, even if its left unattended, lost, or stolen. If the computer is equipped with a compatible TPM, BitLocker uses the TPM to lock the encryption keys that protect the data. As a result, the keys can't be accessed until the TPM verifies the state of the computer.
Not configured (default) - This setting isn't evaluated for compliance or non-compliance.
Require - The device can protect data that's stored on the drive from unauthorized access when the system is off, or hibernates.
Box 2: Prevent jailbroken devices from having corporate access
Device Compliance settings for iOS/iPadOS in Intune
There are different compliance settings you can configure on iOS/iPadOS devices in Intune. As part of your mobile device management (MDM) solution, use these settings to require an email, mark rooted (jailbroken) devices as not compliant, set an allowed threat level, set passwords to expire, and more.
Device Health
Jailbroken devices
Supported for iOS 8.0 and later
Not configured (default) - This setting isn't evaluated for compliance or non-compliance.
Block - Mark rooted (jailbroken) devices as not compliant.
Box 3: Prevent rooted devices from having corporate access.
Device compliance settings for Android Enterprise in Intune
There are different compliance settings you can configure on Android Enterprise devices in Intune. As part of your mobile device management (MDM) solution, use these settings to mark rooted devices as not compliant, set an allowed threat level, enable Google Play Protect, and more.
Device Health - for Personally-Owned Work Profile
Rooted devices
Not configured (default) - This setting isn't evaluated for compliance or non-compliance.
Block - Mark rooted devices as not compliant.
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-create-windows
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-create-android-for-work
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-create-ios
- 質問一覧「124問」
- 質問1 Microsoft Intune を含む Microsoft 365 サブスクリプションをお...
- 質問2 次の表に示すデバイスを含む Microsoft Entra テナントがありま...
- 質問3 Windows AutoPilot の技術要件を満たす必要があります。 Azure A...
- 質問4 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問5 会社には、複数の Windows 10 デバイスを含む contoso.com とい...
- 質問6 ハイブリッド Azure AD テナントがあります。 次の図に示すよう...
- 質問7 あなたの会社では Microsoft Intune を使用しています。 500 台...
- 質問8 Windows Admin Center を使用して、Windows 10 を実行するコンピ...
- 質問9 Microsoft Intune に登録されている 100 台の Windows 10 デバイ...
- 質問10 ネットワークには Active Directory ドメインが含まれています。...
- 質問11 次の表に示すオブジェクトを含む Microsoft 365 テナントがあり...
- 質問12 新しい人事部門のコンピューターの技術要件を満たす必要がありま
- 質問13 会社には、Windows 10 を実行し、Microsoft Azure Active Direct...
- 質問14 Microsoft Intune を含む Microsoft 365 サブスクリプションがあ...
- 質問15 Microsoft Intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問16 Microsoft Intune を使用する Microsoft 365 テナントがあります...
- 質問17 MDM 展示に表示されている MDM セキュリティ ベースライン プロ...
- 質問18 Microsoft Intune に登録されている 500 台の macOS デバイスを...
- 質問19 会社には、複数の Windows 10 デバイスを含む contoso.com とい...
- 質問20 1,000 台の iOS デバイスと Microsoft Intune を含む Microsoft ...
- 質問21 次の表に示すユーザーを含む Azure Active Directory Premium プ...
- 質問22 Microsoft 365 サブスクリプションをお持ちです。 Windows 10 を...
- 質問23 Phoenix オフィス コンピューターの展開を準備する必要がありま...
- 質問24 次の表に示すように、3 つのサイトに Microsoft Deployment Tool...
- 質問25 Windows 10 を実行し、Azure Log Analytics ワークスペースに接...
- 質問26 次の表に示すデバイスを含む Microsoft 365 サブスクリプション...
- 質問27 Windows Autopilot 展開プロファイルを作成します。 次の要件を...
- 質問28 contoso.com という名前の Azure AD テナントがあります。 Windo...
- 質問29 User1 という名前のユーザーを含む Microsoft 365 サブスクリプ...
- 質問30 contoso.com という名前の Azure AD テナントがあります。 ユー...
- 質問31 Microsoft 365 テナントと内部証明機関 (CA) があります。 管理...
- 質問32 開発者向けのデバイス管理要件を満たす必要があります。 何を実
- 質問33 次の表に示すオブジェクトを含む Microsoft 365 テナントがあり...
- 質問34 Active Directory に参加し、Microsoft Intune に登録されている...
- 質問35 次の表に示すデバイスを含む contoso.com という名前の Azure AD...
- 質問36 Microsoft Intune に登録されている Computer1 という名前の Win...
- 質問37 ネットワークには、オンプレミスの Active Directory ドメインと...
- 質問38 Microsoft 365 サブスクリプションをお持ちです。 セキュリティ...
- 質問39 計画された変更に基づいて Boundary1 を実装します。 192.168.1....
- 質問40 Windows 10 を実行するコンピューターが 100 台あります。サーバ...
- 質問41 Microsoft 365 サブスクリプションがあります。サブスクリプショ...
- 質問42 次の表に示すように、動的デバイス メンバーシップ タイプを使用...
- 質問43 Microsoft Intune を含む Microsoft 365 サブスクリプションをお...
- 質問44 次の表に示すように、Microsoft Intune に登録されているデバイ...
- 質問45 Microsoft Intune を使用し、次の表に示すデバイスを含む Micros...
- 質問46 Microsoft 365 サブスクリプションをお持ちです。 すべてのコン...
- 質問47 Microsoft 365 サブスクリプションをお持ちです。 ユーザーは、M...
- 質問48 ネットワークには、contoso.com という名前の Active Directory ...
- 質問49 Windows Autopilot 展開の一部としてコンピューター オブジェク...
- 質問50 Microsoft Deployment Toolkit (MDT) がインストールされていま...
- 質問51 Microsoft Intune を使用する Microsoft 365 ES サブスクリプシ...
- 質問52 User1 という名前のユーザーを含む Microsoft 365 E5 サブスクリ...
- 質問53 Windows 11 を展開するには、Microsoft Deployment Toolkit (MDT...
- 質問54 ネットワークには Active Directory ドメイン サービス (AD DS) ...
- 質問55 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問56 会社には Windows 10 を実行するコンピューターが 200 台ありま...
- 質問57 Windows 11 を実行する 500 台のコンピューターを含む Microsoft...
- 質問58 ネットワークには Active Directory ドメインが含まれています。...
- 質問59 Microsoft Intune に登録されている Windows 10 デバイスが 100 ...
- 質問60 Microsoft Intune が含まれる Microsoft 365 ES サブスクリプシ...
- 質問61 Windows 10 がインストールされている Computed という名前のコ...
- 質問62 Microsoft 365 テナントがあります。 Microsoft Intune に登録さ...
- 質問63 会社所有の Windows デバイス 100 台を交換します。 デバイスを...
- 質問64 Windows 10 を実行する Computer1 と Computed という 2 台のコ...
- 質問65 Microsoft Intune には、次の表に示すデバイス コンプライアンス...
- 質問66 次の表に示すように、会社には Microsoft Intune に登録されたデ...
- 質問67 次のデバイス コンプライアンス ポリシー設定を持つ Microsoft I...
- 質問68 Microsoft Intune に登録されている 1,000 台の Windows 11 デバ...
- 質問69 Microsoft 365 E5 サブスクリプションをお持ちです。 次の図に示...
- 質問70 User1 と User2 が Intune に登録できるデバイスの最大数はいく...
- 質問71 会社では Microsoft Intune を使用してデバイスを管理しています...
- 質問72 次の表に示すデバイスを含む Microsoft 365 サブスクリプション...
- 質問73 Microsoft Intune と Intune データ ウェアハウスを使用します。...
- 質問74 Microsoft Intune と Intune データ ウェアハウスを使用します。...
- 質問75 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問76 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問77 次の表に示すデバイスを含む Microsoft 365 テナントがあります...
- 質問78 DS1 という名前の Microsoft Deployment Toolkit (MDT) 展開共有...
- 質問79 - Microsoft Intune に登録されているデバイスを含む Microsoft ...
- 質問80 Microsoft 365 サブスクリプションをお持ちです。 次の表に示す...
- 質問81 次の表に示すように、Microsoft Intune に登録されているデバイ...
- 質問82 Microsoft 365 サブスクリプションをお持ちです。 次の表に示す...
- 質問83 Microsoft 365 サブスクリプションをお持ちです。 次の種類のデ...
- 質問84 Windows 10 を実行し、Active Directory ドメインのメンバーであ...
- 質問85 Microsoft 365 サブスクリプションをお持ちです。 アプリ保護ポ...
- 質問86 IT 部門の技術要件を満たす必要があります。 まず何をすべきでし...
- 質問87 Microsoft 365 サブスクリプションをお持ちです。 次の図に示す...
- 質問88 Microsoft Intune を使用し、次の表に示すユーザーを含む Micros...
- 質問89 - DS1 という名前の Microsoft Deployment Toolkit (MDT) 展開共...
- 質問90 ネットワークには Active Directory ドメインが含まれています。...
- 質問91 次の各文について、正しい場合は「はい」を選択してください。そ
- 質問92 Microsoft Intune を使用する Microsoft 365 サブスクリプション...
- 質問93 Microsoft 365 ES サブスクリプションをお持ちです。 Microsoft ...
- 質問94 次の表に示すデバイスを含む contoso.com という名前の Azure Ac...
- 質問95 Microsoft Intune を使用する Microsoft 365 サブスクリプション...
- 質問96 150 台のハイブリッド Azure AD 参加済み Windows デバイスを含...
- 質問97 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問98 会社には、Windows 10 を実行する Computer1 という名前のコンピ...
- 質問99 Microsoft 365 サブスクリプションをお持ちです。 Microsoft Int...
- 質問100 次の表に示すユーザーを含む Azure Active Directory Premium プ...
- 質問101 Microsoft 365 E5 サブスクリプションがあります。サブスクリプ...
- 質問102 次の表に示すグループを含む Microsoft 365 E5 サブスクリプショ...
- 質問103 Microsoft 365 Business Standard サブスクリプションと 100 台...
- 質問104 Microsoft Intune を使用し、100 台の Windows 10 デバイスを含...
- 質問105 Windows 11 Pro を実行するコンピューターがあります。コンピュ...
- 質問106 次の表に示すデバイスを含む contoso.com という名前の Azure AD...
- 質問107 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問108 次の図に示すデバイス構成プロファイルがあります。 (Exhibit) ...
- 質問109 Microsoft Intune を使用する Microsoft 365 E5 サブスクリプシ...
- 質問110 DS1 という名前の Microsoft Deployment Toolkit (MDT) 展開共有...
- 質問111 Microsoft 365 サブスクリプションをお持ちです。 すべてのユー...
- 質問112 Windows 10 を実行するコンピューターが 200 台あります。コンピ...
- 質問113 Microsoft 365 E5 サブスクリプションをお持ちです。 Microsoft ...
- 質問114 Microsoft 365 E5 サブスクリプションをお持ちです。 次の図に示...
- 質問115 - 次の表に示すデバイスを含む Microsoft 365 サブスクリプショ...
- 質問116 iOS デバイスを管理するには、Microsoft Intune サブスクリプシ...
- 質問117 次の表に示すリソースを含む Microsoft Intune 展開があります。...
- 質問118 次の表に示すオンプレミス サーバーがあります。 (Exhibit) Andr...
- 質問119 - 次の表に示すデバイスを含む Microsoft 365 サブスクリプショ...
- 質問120 Microsoft Intune に登録されている 100 台の iOS デバイスを含...
- 質問121 Microsoft 365 E5 サブスクリプションと 25 台の Apple iPad を...
- 質問122 Microsoft Intune Suite を使用する Microsoft 365 サブスクリプ...
- 質問123 Hyper-V ホストがあります。ホストには、次の表に示すように、Wi...
- 質問124 Microsoft Intune を使用し、次の表に示すユーザーを含む Micros...

[×]
Download PDF File
Enter your email address to download Microsoft.MD-102-JPN.v2024-09-04.q124.pdf
