- ホーム
- Microsoft
- AZ-500J - Microsoft Azure Security Technologies (AZ-500日本語版)
- Microsoft.AZ-500J.v2024-04-10.q174
- 質問15
有効的なAZ-500J問題集はJPNTest.com提供され、AZ-500J試験に合格することに役に立ちます!JPNTest.comは今最新AZ-500J試験問題集を提供します。JPNTest.com AZ-500J試験問題集はもう更新されました。ここでAZ-500J問題集のテストエンジンを手に入れます。
AZ-500J問題集最新版のアクセス
「497問、30% ディスカウント、特別な割引コード:JPNshiken」
次の表に示すユーザーを含むcontoso.comという名前のAzure Active Directory(Azure AD)テナントがあります。

次の設定を持つAzure AD Identity Protectionユーザーリスクポリシーを作成して適用します。
*割り当て:グループ1を含め、グループ2を除外します
*条件:中以上のサインインリスク
*アクセス:アクセスを許可し、パスワードの変更が必要
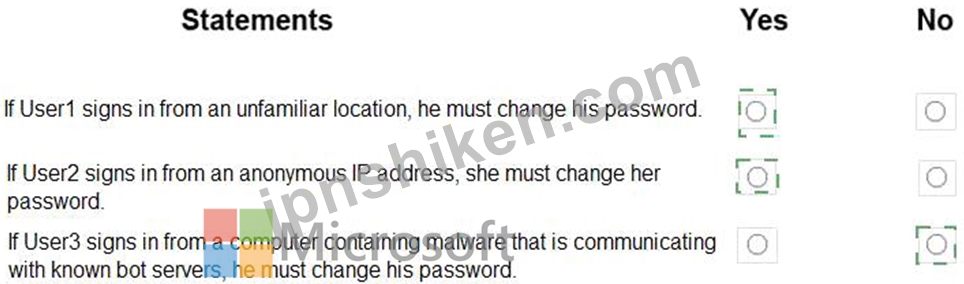
以下の各ステートメントについて、ステートメントが真である場合は「はい」を選択します。それ以外の場合は、「いいえ」を選択します。
注:それぞれの正しい選択には1ポイントの価値があります。


次の設定を持つAzure AD Identity Protectionユーザーリスクポリシーを作成して適用します。
*割り当て:グループ1を含め、グループ2を除外します
*条件:中以上のサインインリスク
*アクセス:アクセスを許可し、パスワードの変更が必要
以下の各ステートメントについて、ステートメントが真である場合は「はい」を選択します。それ以外の場合は、「いいえ」を選択します。
注:それぞれの正しい選択には1ポイントの価値があります。

正解:
Explanation:
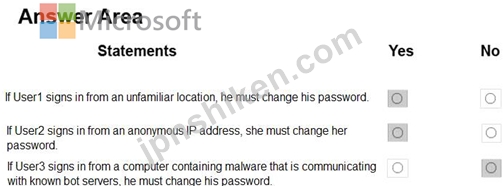
Box 1: Yes
User1 is member of Group1. Sign in from unfamiliar location is risk level Medium.
Box 2: Yes
User2 is member of Group1. Sign in from anonymous IP address is risk level Medium.
Box 3: No
Sign-ins from IP addresses with suspicious activity is low.
Note:
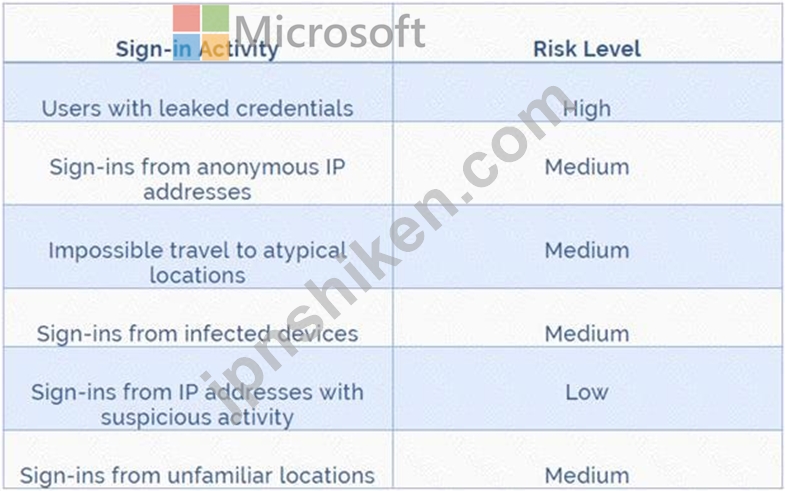
Azure AD Identity protection can detect six types of suspicious sign-in activities:
Users with leaked credentials
Sign-ins from anonymous IP addresses
Impossible travel to atypical locations
Sign-ins from infected devices
Sign-ins from IP addresses with suspicious activity
Sign-ins from unfamiliar locations
These six types of events are categorized in to 3 levels of risks - High, Medium & Low:
References:
http://www.rebeladmin.com/2018/09/step-step-guide-configure-risk-based-azure-conditional-access-policies/
- 質問一覧「174問」
- 質問1 Azure Container Registryに接続するAzure Kubernetes Service(...
- 質問2 ネットワークには、Azure Active Directory(Azure AD)と同期す...
- 質問3 RG1という名前のリソースグループとUser1という名前のユーザーを...
- 質問4 Azure Sentinelをオンボードします。 Azure SentinelをAzure Sec...
- 質問5 Azure Container Registryに接続するAzure Kubernetes Service(...
- 質問6 コンテナー化されたアプリケーションインスタンスの新しいストレ
- 質問7 RG2の作成とRG1の権限の管理を委任する必要があります。どのユー...
- 質問8 AzureSQLデータベースを使用するアプリがあります。 データベー...
- 質問9 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問10 User1という名前のユーザーとConReg1という名前のAzure Containe...
- 質問11 Azure ADアプリケーションの登録と同意の構成がIDとアクセスの要...
- 質問12 Azure キー コンテナーを含む Azure サブスクリプションがありま...
- 質問13 Azure Security Centerから、Registry1のイメージのAzure Contai...
- 質問14 Azureサブネットにバインドされたネットワークセキュリティグル...
- 質問15 次の表に示すユーザーを含むcontoso.comという名前のAzure Activ...
- 質問16 技術的な要件を満たすには、AzureSentinelノートブックのサポー...
- 質問17 Azure AD テナントがあります。 次の要件を満たす認証ソリューシ...
- 質問18 ラボのタスク 必要に応じて、次のログイン資格情報を使用します
- 質問19 プラットフォーム保護要件を満たすために、Role1を作成する必要...
- 質問20 次の表に示す Azure Key Vault を含む Sub1 という名前の Azure ...
- 質問21 VNetwork1の技術要件を満たす必要があります。 最初に何をすべき...
- 質問22 オンプレミス ネットワークには、VM1 という名前の Hyper-V 仮想...
- 質問23 次の表に示すリソースを格納する Vault1 という名前の Azure キ...
- 質問24 3つのAzureサブスクリプションとUser1という名前のユーザーがあ...
- 質問25 Azure仮想マシンの展開に使用するAzure Resource Managerテンプ...
- 質問26 Azure サブスクリプション内のリソースへのアクセスを保護してい...
- 質問27 4つのAzureSQLマネージドインスタンスを含むAzureサブスクリプシ...
- 質問28 次の表に示すリソース グループを含む Sub1 という名前の Azure ...
- 質問29 Contoso.com という名前の Azure Active Directory (Azure AD) ...
- 質問30 storage1 という名前の Azure Data Lake Storage Gen2 アカウン...
- 質問31 オンプレミス ネットワークには、次の表に示すサーバーが含まれ
- 質問32 Azure Sentinelを使用して、疑わしい脅威を検出し、応答を自動化...
- 質問33 SQL1という名前のAzureSQLデータベースとKeyVault1という名前のA...
- 質問34 次の表に示すアイテムを含むKeyVault1という名前のAzureキーボー...
- 質問35 Azure サブスクリプションをお持ちです。 次の要件を満たすには...
- 質問36 次の表に示す仮想マシンを含む Azure サブスクリプションがあり...
- 質問37 Azureサブスクリプションがあります。 S1 Appサービスプランを使...
- 質問38 ネットワークには、contoso.comという名前のActive Directoryフ...
- 質問39 webapp1という名前のAzure Webアプリがあります。 Azure Repoを...
- 質問40 ラボのタスク 必要に応じて、次のログイン資格情報を使用します
- 質問41 次の表に示すユーザーを含む Azure AD テナントがあります。 (Ex...
- 質問42 次の表に示す仮想マシンを含むAzureサブスクリプションがありま...
- 質問43 次の表に示すリソースを含むAzureサブスクリプションがあります...
- 質問44 オンプレミスサーバーでホストされているWebアプリがあり、次のU...
- 質問45 注:質問は、同じ設定を表すいくつかの質問に含まれています。た
- 質問46 次の表に示すAzure仮想マシンがあります。 (Exhibit) 米国東部リ...
- 質問47 Azure Active Directory(Azure AD)テナントにリンクされている...
- 質問48 sub1という名前のAzureサブスクリプションを含むGroup1という名...
- 質問49 Contosostorage1という名前のAzureストレージアカウントとContos...
- 質問50 Sub1 と Sub2 という名前の 2 つの Azure サブスクリプションが...
- 質問51 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問52 次の表に示すストレージアカウントを含むAzureサブスクリプショ...
- 質問53 Windows Server2019を実行するVM1およびVM2という名前の2つの仮...
- 質問54 Azure Active Directory(Azure AD)のハイブリッド構成がありま...
- 質問55 App1をホストするために使用する仮想マシンを推奨する必要があり...
- 質問56 次の表に示すリソースを格納する Vault1 という名前の Azure キ...
- 質問57 App1 という名前の Web アプリを含む Azure サブスクリプション...
- 質問58 3つのストレージアカウント、SQLという名前のAzure SQLマネージ...
- 質問59 RG1という名前のリソースグループを含むAzureサブスクリプション...
- 質問60 Sub1という名前のAzureサブスクリプションがあります。 Sub1には...
- 質問61 OU2とUser1に対して計画された変更を実行する必要があります。 ...
- 質問62 Azure サブスクリプションを作成します。 Azure Active Director...
- 質問63 仮想ネットワークを含むAzureサブスクリプションがあります。仮...
- 質問64 Microsoft Defender for Cloud を使用する Sub1 という名前の Az...
- 質問65 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問66 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問67 Sub2の仮想マシン間のネットワーク通信のセキュリティを評価して...
- 質問68 Appl という名前の Web アプリを含む Azure サブスクリプション...
- 質問69 EASM1 という名前の Microsoft Defender 外部攻撃対象領域管理 (...
- 質問70 ラボのタスク 必要に応じて、次のログイン資格情報を使用します
- 質問71 次の表に示すように、米国東部2リージョンに2つのAzure仮想マシ...
- 質問72 share1 という名前の Azure Files 共有と User1 という名前のユ...
- 質問73 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問74 Azureサブスクリプションがあります。 Azure Storageアカウント...
- 質問75 次の資料に示す役割の割り当てがあります。 (Exhibit) ドロップ...
- 質問76 MicrosoftSentinelを展開しています。 サードパーティのセキュリ...
- 質問77 DB1 という名前の Azure SQL データベースがあり、Table という...
- 質問78 新しいAzureサブスクリプションを作成します。 Azure Security C...
- 質問79 次の表に示すカスタムロールを含むAzureサブスクリプションがあ...
- 質問80 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問81 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問82 次の表に示す仮想マシンを含む Azure サブスクリプションがあり...
- 質問83 Azure AD テナントにリンクされ、次の表に示す仮想マシンを含む ...
- 質問84 Azure環境があります。 ISO27001標準に準拠していないAzure構成...
- 質問85 Microsoft Defender for Cloud を使用する Azure サブスクリプシ...
- 質問86 User1 という名前のユーザーと storage1 という名前のストレージ...
- 質問87 あなたの会社には、シアトルとニューヨークに2つのオフィスがあ
- 質問88 sql1という名前のAzureSQLデータベースを含むAzureサブスクリプ...
- 質問89 MicrosoftSentinelを使用するAzureサブスクリプションがあります...
- 質問90 Azure Blob ストレージ アカウント bolb1 を含む Azure サブスク...
- 質問91 会社には、次の表に示すユーザーを含むSubscription1という名前...
- 質問92 次の表に示すように、RG1という名前のリソースグループとユーザ...
- 質問93 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問94 月曜日に、Microsoft Defender for Cloud で電子メール通知を構...
- 質問95 AzureStorageアカウントのセキュリティ問題のトラブルシューティ...
- 質問96 次の表に示すAzureリソースがあります。 (Exhibit) 次の要件を満...
- 質問97 次の表に示すリソースを含むSubscription1という名前のAzureサブ...
- 質問98 container1という名前のコンテナーを持つstorage1という名前のAz...
- 質問99 次の表に示すように、Azureサブスクリプションでリソースを作成...
- 質問100 Azure仮想マシンの展開に使用するAzure Resource Managerテンプ...
- 質問101 財務部門のユーザーの技術要件を満たす必要があります。 どのCAP...
- 質問102 ラボのタスク 必要に応じて、次のログイン資格情報を使用します
- 質問103 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問104 User1という名前のユーザーを含むAzureActiveDirectory(Azure A...
- 質問105 Identityという名前の管理されたIDを持ち、Azure Active Directo...
- 質問106 Azure Active Directory(Azure AD)コネクタ、Query1という名前...
- 質問107 次の表に示す仮想マシンを含むAzureサブスクリプションがありま...
- 質問108 Vault1という名前のAzure Key Vaultを含むAzureサブスクリプショ...
- 質問109 User1 という名前のユーザーと storage 1 という名前のストレー...
- 質問110 次の表に示す仮想マシンを含むAzureサブスクリプションがありま...
- 質問111 Azure ActiveDirectoryプレミアムプラン1テナントにリンクされた...
- 質問112 SQL1 という名前の Azure SQL サーバーを含む Azure サブスクリ...
- 質問113 Azureポータルから、Azureポリシーを構成しています。 DeployIfN...
- 質問114 Sub1という名前のAzureサブスクリプションがあります。 1つのサ...
- 質問115 Azure Active Directory(Azure AD)特権ID管理(PIM)を使用す...
- 質問116 Azure SQL データベースがあります。 Always Encrypted を実装し...
- 質問117 You have an Azure Active Directory (Azure AD) tenant that co...
- 質問118 JITVMアクセスを実装することを計画しています。どの仮想マシン...
- 質問119 会社には、contoso.comという名前のAzure Active Directory(Azu...
- 質問120 次の表に示すグループを含む Azure AD テナントがあります。 (Ex...
- 質問121 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問122 セキュリティ運用要件を満たしていることを確認する必要がありま
- 質問123 次の表に示すオフィスを持つContoso、Ltd.という会社で働いてい...
- 質問124 LAW1という名前のAzure Log Analyticsワークスペースを含むSub1...
- 質問125 UserR1 という名前のユーザーを含む Azure サブスクリプションが...
- 質問126 VNET1およびVNET2という2つのAzure仮想ネットワークのネットワー...
- 質問127 SQLDB1という名前のAzureSQLデータベースを含むAzureサブスクリ...
- 質問128 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問129 KeyVault1という名前のAzureキーコンテナーと、次の表に示す仮想...
- 質問130 SQLという名前のAzureSQLデータベースロジックサーバーを含むAzu...
- 質問131 Adminl1という名前のユーザーとVM1という名前の仮想マシンを含む...
- 質問132 Azureストレージアカウントのセキュリティ問題をトラブルシュー...
- 質問133 あなたは、新しいレビューのコレクションに割り当てることを計画
- 質問134 次の表に示す仮想マシンを含むAzureサブスクリプションがありま...
- 質問135 次の Azure ファイアウォールを含む Azure サブスクリプションが...
- 質問136 Subscription1という名前のAzureサブスクリプションがあります。...
- 質問137 User1 と User2 という名前の 2 人のユーザーと、App1 という名...
- 質問138 webapp1という名前のAzure Webアプリがあります。 Azure Repoを...
- 質問139 AzFWL という名前の Azure Firewall Standard のインスタンスを...
- 質問140 次の表に示すリソースを含むAzureサブスクリプションがあります...
- 質問141 Windows Server2019を実行するオンプレミスサーバーが10台ありま...
- 質問142 Azure AD テナントと App1 という名前のアプリケーションがあり...
- 質問143 Azure サブスクリプションをお持ちです。これには、次の表に示す...
- 質問144 sa1 という名前の Azure Data Lake Storage アカウントを含む Az...
- 質問145 アクセスレビューを設定する必要があります。レビューは新しいレ
- 質問146 ラボのタスク 必要に応じて、次のログイン資格情報を使用します
- 質問147 Azure Active Directory(Azure AD)にリンクされているAzureサ...
- 質問148 注:この質問は、同じシナリオを提示する一連の質問の一部です。
- 質問149 ユーザーがVM0にアクセスできることを確認する必要があります。...
- 質問150 Sub1という名前のAzureサブスクリプションがあります。 Sub1には...
- 質問151 次の表に示すユーザーを含むAzure Active Directory(Azure AD)...
- 質問152 You have an Azure subscription that contains an Azure SQL da...
- 質問153 次の展示に示すAzureリソースの階層があります。 (Exhibit) 次の...
- 質問154 あなたの会社は、部門ごとに個別のサブスクリプションを作成する
- 質問155 次の表に示すAzureActive Directory(Azure AD)リソースを含むA...
- 質問156 contosos.comという名前のAzure Active Directory(Azure AD)テ...
- 質問157 AzureサブスクリプションマットにRG1という名前のリソースグルー...
- 質問158 次の表に示すリソースを含む Azure サブスクリプションがありま...
- 質問159 Azureコンテナーインスタンスを展開する予定です。 クレジットカ...
- 質問160 Azure サブスクリプションがあり、次の表に示すコンピューターが...
- 質問161 Azure Log Analyticsを使用して、Windows Server 2016を実行する...
- 質問162 Azure AD Premium P1 ライセンスを持つ contoso.com という名前...
- 質問163 KeyVault1 という名前の Azure Key Vault があり、次の表に示す...
- 質問164 単一のネットワークセキュリティグループ(NSG)を持つ単一のサ...
- 質問165 Azureサブスクリプションがあります。 別のAzure Active Directo...
- 質問166 VNet1 という名前の仮想ネットワークを含む Azure サブスクリプ...
- 質問167 WebApp1という名前のAzure Webアプリがあります。 証明書をWebAp...
- 質問168 Azure サブスクリプションをお持ちです。 次の表に示すルールを...
- 質問169 次の表に示すユーザーを含むAzureサブスクリプションがあります...
- 質問170 次の表に示すリソースを含むAzureActive Directory(Azure AD)...
- 質問171 あなたの会社には、weylandindustries.com という名前の単一ドメ...
- 質問172 Azure Key Vaultがあります。 次の要件を満たすために、Key Vaul...
- 質問173 次の表に示すリソースを含むAzureサブスクリプションがあります...
- 質問174 ラボのタスク 必要に応じて、次のログイン資格情報を使用します

