- ホーム
- CyberArk
- PAM-DEF-JPN - CyberArk Defender - PAM (PAM-DEF日本語版)
- CyberArk.PAM-DEF-JPN.v2024-04-23.q119
- 質問34
有効的なPAM-DEF-JPN問題集はJPNTest.com提供され、PAM-DEF-JPN試験に合格することに役に立ちます!JPNTest.comは今最新PAM-DEF-JPN試験問題集を提供します。JPNTest.com PAM-DEF-JPN試験問題集はもう更新されました。ここでPAM-DEF-JPN問題集のテストエンジンを手に入れます。
PAM-DEF-JPN問題集最新版のアクセス
「240問、30% ディスカウント、特別な割引コード:JPNshiken」
各キーを推奨される保管場所と一致させます。


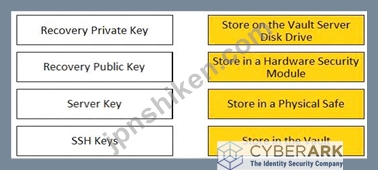
正解:
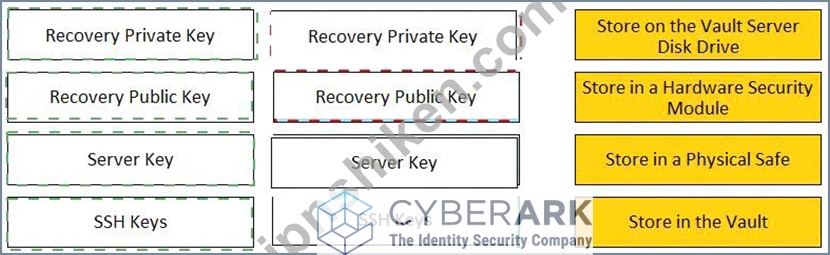
Explanation
* The recommended storage locations for each key are as follows:
* Recovery Private Key: It is recommended to store the Recovery Private Key on the Vault Server Disk Drive. This is because the Recovery Private Key is used to decrypt the data stored in the Vault.
* Recovery Public Key: It is recommended to store the Recovery Public Key in a Hardware Security Module. This is because the Recovery Public Key is used to encrypt the data stored in the Vault.
* Server Key: It is recommended to store the Server Key in a Physical Safe. This is because the Server Key is used to open the Vault, much like the key of a physical Vault. The key is required to start the Vault, after which the Server Key can be removed until the Server is restarted. When the Vault is stopped, the information stored in the Vault is completely inaccessible without that key.
* SSH Keys: It is recommended to store the SSH Keys in the Vault. This is because the SSH Keys are used to connect to remote machines using the SSH protocol. The Vault can manage the passwords and sessions for the SSH Keys and provide secure access to the target systems.
References: Server keys - CyberArk, Cyberark Key Storage Plugin (Enterprise) - Rundeck
- 質問一覧「119問」
- 質問1 オンボーディング ルールを作成すると、 で実行されます。
- 質問2 アカウント フィードを使用してアカウントをオンボーディングす
- 質問3 新しい金庫を作成したので、ユーザー グループがパスワードを参
- 質問4 ユーザーのロックを解除する権利を Tier 1 サポートに委任するよ...
- 質問5 特定のプラットフォームの録画が保存される金庫を変更するには、
- 質問6 CyberArk 認証を利用する新しい Rest API ユーザーを作成し...
- 質問7 金庫が 1 日の特定の時間帯にアクセスできるように構成されてい...
- 質問8 PSM は、Unix で実行された各コマンドの記録をキャプチャします...
- 質問9 DR Vault の Status of Service を、レプリケーション モードで...
- 質問10 DNA を活用して、自動検出では利用できない検出機能を提供するこ...
- 質問11 展示を参照してください。 (Exhibit) ユーザー「EMEALevel2Suppo...
- 質問12 次のエラーが表示されます。 どの根本原因を調査する必要があり
- 質問13 Vault Admins グループのメンバーである限り、アクセスできるす...
- 質問14 ネットワーク アクティビティが原因で、ACME Corp の PrivateArk...
- 質問15 アカウント グループを作成し、クラスターに属する 3 つのアカウ...
- 質問16 CyberArk は、ボールトにプロビジョニングできるユーザーの...
- 質問17 PSM を介してターゲット デバイスに接続するには、接続に使用さ...
- 質問18 新しい HTML5 ゲートウェイが組織に導入されました。 PVWA から...
- 質問19 Ad-Hoc Access (以前の Secure Connect) は、次の機能を提供しま...
- 質問20 Vault HA クラスターを構成しています。 Quorum および Safes デ...
- 質問21 ユーザーが Vault にログインできる時間帯を制御することができ...
- 質問22 ユーザーを Vault 管理者グループに直接追加するにはどの方法を...
- 質問23 パスワードコンプライアンス監査により次のことが判明しました。
- 質問24 これらのアカウントのオンボーディング方法のうち、プロアクティ
- 質問25 Vault 管理者は、新しいライセンスをシステム Safe にアップロー...
- 質問26 資格情報の盗難の疑いを検出するには、どの PTA センサーが必要...
- 質問27 否認防止を保証するマスター ポリシー設定はどれですか?
- 質問28 次のオプションのうち、マスター ポリシーで設定されていないも
- 質問29 エンド ユーザーがリモート マシンに透過的にログインできるが、...
- 質問30 サービス アカウント プラットフォームとして追加できる用途はど...
- 質問31 CyberArk マーケットプレイスからカスタム プラットフォーム...
- 質問32 インストール後に設定を変更する必要がある場合に、PTA 内で電子...
- 質問33 新しい HTML5 ゲートウェイが組織に導入されました。 HTML5 ゲー...
- 質問34 各キーを推奨される保管場所と一致させます。 (Exhibit)...
- 質問35 ユーザーは、PVWA を通じて記録されたセッションを表示する必要...
- 質問36 新しい同僚が、Active Directory グループと Vault の間のディレ...
- 質問37 マスター CD を保存するためのベスト プラクティスを選択します...
- 質問38 PTA がサポートされている SIEM ソリューションと統合されている...
- 質問39 各ユーザーがアクセスできるアカウントを示すレポートはどれです
- 質問40 最近完了したデュアル コントロール リクエストから変更する必要...
- 質問41 Vault 管理者チーム メンバーは CyberArk にログインできま...
- 質問42 CPM ポリシーの間隔設定の目的は何ですか?
- 質問43 PSM フレームワークの Web アプリケーションを介して Web サイト...
- 質問44 CPM が、変更が必要なまもなく期限切れになるパスワードを探す頻...
- 質問45 PVWA のレポート ページから「資格レポート」を生成するには、ユ...
- 質問46 ______で構成されたパスワード検証を実行できる時間帯または曜日...
- 質問47 コンテナーは、サブネット ベースのアクセス制御をサポートして
- 質問48 ユーザーが短い PSM セッションを正常に実行し、ログオフしまし...
- 質問49 ターゲット アカウント プラットフォームは、Allowed Safes プロ...
- 質問50 CyberArk によると、インストールされているコンポーネント...
- 質問51 ____________________に基づいてマスター ポリシーの例外を作成...
- 質問52 あなたが Vault Admins グループのメンバーである限り、あらゆる...
- 質問53 PSM レコーディングのカスタマイズのオプションはどれですか?...
- 質問54 PVWA の応答が遅い場合のトラブルシューティングを行っています...
- 質問55 ITALog に DR ユーザーの認証失敗エントリがあることに気付きま...
- 質問56 Vault 管理者は、Vault 内の Unix ルート アカウントの 1 つにロ...
- 質問57 組み込みの Vault ユーザーを正しい定義と一致させます。 (Exhib...
- 質問58 CPM がデータベースに接続するとき、どのインターフェイスが最も...
- 質問59 Simple Mail Transfer Protocol (SMTP) の統合は、Vault のアク...
- 質問60 PAReplicate 用にサーバーに必要なディスク容量はどれくらいです...
- 質問61 CPM によるローテーションのために、5,000 の UNIX ルート アカ...
- 質問62 ボールトを再起動せずにボールトのデバッグ レベルを変更するた
- 質問63 アカウントの住所フィールドで使用できる値はどれですか?
- 質問64 プライマリ ボールトの障害により、ADR ボールトがアクティブに...
- 質問65 DR 実行後に実稼働インフラストラクチャにフェールバックする前...
- 質問66 Vault 内では、各パスワードは次の方法で暗号化されます。
- 質問67 すべてのセッションが確実に記録されるように、CyberArk 管...
- 質問68 特定の金庫の PVWA の [レポート] ページから「特権アカウント ...
- 質問69 CyberArk は、すべての Safe にオブジェクト レベルのアクセ...
- 質問70 root の SSH アクセスが拒否された場合、[接続] ボタンを使用し...
- 質問71 PTA はどこでアラートを送信するように設定できますか? (2つお選...
- 質問72 次の Privileged Session Management ソリューションのうち、セ...
- 質問73 プライマリ本番ボールトが稼働しているときに、DR ボールトで実...
- 質問74 ファイルからアカウントを追加するときに必須のプロパティは次の
- 質問75 Export Vault Data (EVD) ユーティリティは何をしますか?...
- 質問76 PrivateArk サーバー サービスの目的は何ですか?
- 質問77 Windows 検出プロセスで使用するためにどのアカウントを選択でき...
- 質問78 PAReplicate で完全なレプリケーションを実行するには、サーバー...
- 質問79 特権セッションで疑わしいアクティビティが検出された場合、PTA ...
- 質問80 特権アカウントを使用する Windows サービスまたはスケジュール...
- 質問81 マスター ユーザーとして CyberArk にログインして、孤立し...
- 質問82 SSH キーを管理するとき、CPM は秘密キーを保存しました
- 質問83 ドメインに新しいドメイン コントローラが追加されました。Cyber...
- 質問84 Vault の完全バックアップを生成するコマンドはどれですか?...
- 質問85 次のコンポーネントのうち、ボールトのテープ バックアップを作
- 質問86 リンクされたアカウントの目的は何ですか?
- 質問87 プラットフォーム レベルでの調整アカウントの設定について正し
- 質問88 プラットフォームの設定は __________ に適用されます。...
- 質問89 次のレポートのうち、PVWA を使用して生成されていないものはど...
- 質問90 UNIX の検出スキャンを設定する場合、何を指定する必要がありま...
- 質問91 あなたの組織では、デフォルトで「クリックして接続」ボタンがア
- 質問92 テキスト ファイルまたは MSSQL データベースに出力するマスター...
- 質問93 デュアル コントロールが有効になっている場合、ユーザーは PSM ...
- 質問94 顧客である ACME Corp は、Safes データをドライブ C ではなくド...
- 質問95 PSM の主な利点は何ですか?
- 質問96 Private Ark クライアントで LDAP グループを CyberArk グル...
- 質問97 自動化されたオンボーディング ルールを管理するには、Cyber...
- 質問98 Vault サービスの稼働状況または停止状況を特定するよう求められ...
- 質問99 DR Vault サーバーがアクティブな格納域になると、プライマリ Va...
- 質問100 プラットフォーム ポリシーの minvalidity パラメーターは何を決...
- 質問101 各ユーザーがアクセスできるアカウントを示すレポートはどれです
- 質問102 パスワード アップロード ユーティリティを実行するために作成ま...
- 質問103 既存のプラットフォームを複製する最も簡単な方法は何ですか?
- 質問104 PSM と PSMP の両方を介して SSH 経由で Unix アカウントにアク...
- 質問105 各権限を見つけられる場所に一致させます。 (Exhibit)
- 質問106 次のログのうち、PTA に関連するエラーに関する情報が含まれてい...
- 質問107 すべての Unix ルート パスワードは、安全な UnixRoot に保存さ...
- 質問108 コンテナーは、役割ベースのアクセス制御をサポートしています。
- 質問109 ユーザーは特定の CyberArk インターフェイス (PVWA や PACL...
- 質問110 dbparm.ini は、Vault のメイン構成ファイルです。...
- 質問111 CyberArk Event Notification Engine サービスの目的は何で...
- 質問112 ボールトに対する管理者権限を持つユーザーは、自分が持っている
- 質問113 ターゲット Windows サーバーの PSM 記録を有効にする場合、次の...
- 質問114 各コンポーネントをそれぞれのログ ファイルの場所に一致させま
- 質問115 新しく作成されたプラットフォームにより、ユーザーは Linux エ...
- 質問116 新しいオンボーディング ルールを作成したいと考えています。 ど...
- 質問117 アカウントの検出により、ドメイン コントローラーへの安全な接
- 質問118 セキュア コネクトは次の機能を提供します。あてはまるものをす
- 質問119 どのプロセスが資格情報の盗難のリスクを軽減しますか? (2つお選...

[×]
Download PDF File
Enter your email address to download CyberArk.PAM-DEF-JPN.v2024-04-23.q119.pdf
