- ホーム
- CompTIA
- SY0-701-JPN - CompTIA Security+ Certification Exam (SY0-701日本語版)
- CompTIA.SY0-701-JPN.v2024-09-24.q112
- 質問78
有効的なSY0-701-JPN問題集はJPNTest.com提供され、SY0-701-JPN試験に合格することに役に立ちます!JPNTest.comは今最新SY0-701-JPN試験問題集を提供します。JPNTest.com SY0-701-JPN試験問題集はもう更新されました。ここでSY0-701-JPN問題集のテストエンジンを手に入れます。
SY0-701-JPN問題集最新版のアクセス
「645問、30% ディスカウント、特別な割引コード:JPNshiken」
ラボシミュレーション1
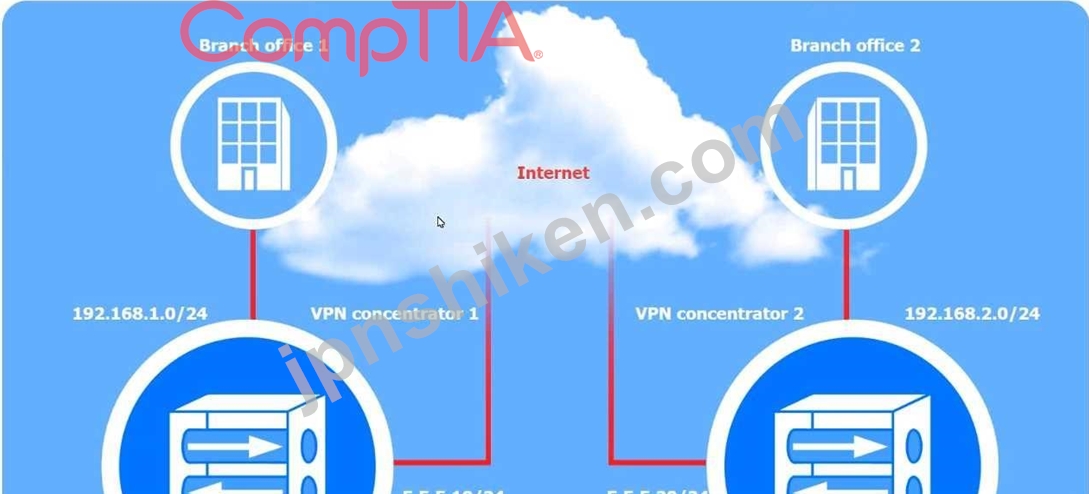
システム管理者は、2 つのブランチ オフィス間のサイト間 VPN を構成しています。一部の設定は既に正しく構成されています。構成を完了するために、システム管理者には次の要件が提供されています。
- 最も安全なアルゴリズムを選択する必要があります
- すべてのトラフィックはVPN経由で暗号化される必要があります
- 2つのVPNを認証するために秘密のパスワードが使用されます
コンセントレータ
システム管理者は、2 つのブランチ オフィス間のサイト間 VPN を構成しています。一部の設定は既に正しく構成されています。構成を完了するために、システム管理者には次の要件が提供されています。
- 最も安全なアルゴリズムを選択する必要があります
- すべてのトラフィックはVPN経由で暗号化される必要があります
- 2つのVPNを認証するために秘密のパスワードが使用されます
コンセントレータ





正解:
To configure the site-to-site VPN between the two branch offices according to the provided requirements, here are the detailed steps and settings that need to be applied to the VPN concentrators:
Requirements:
Most secure algorithms should be selected.
All traffic should be encrypted over the VPN.
A secret password will be used to authenticate the two VPN concentrators.
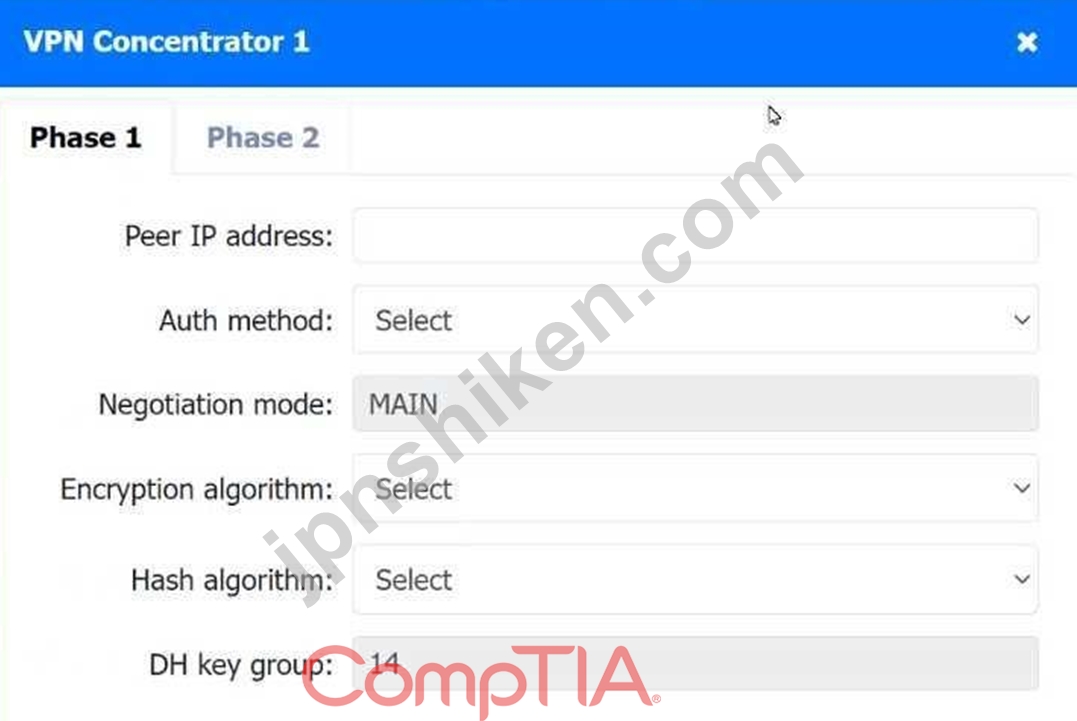
VPN Concentrator 1 Configuration:
Phase 1:
Peer IP address: 5.5.5.10 (The IP address of VPN Concentrator 2)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
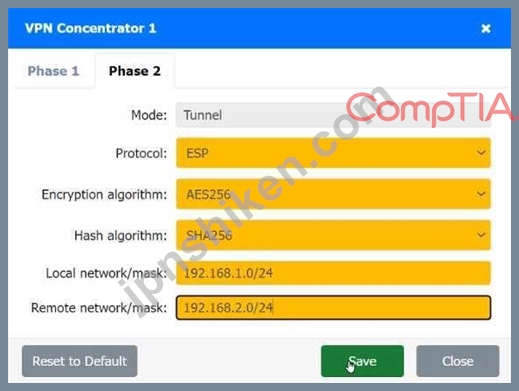
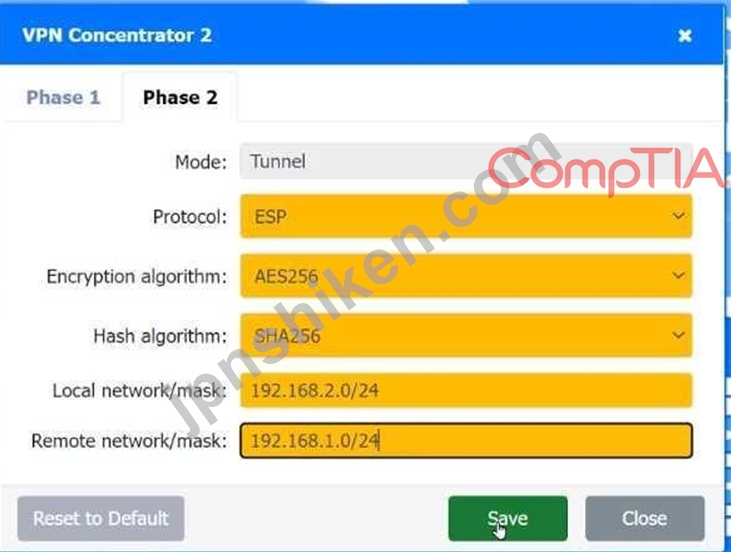
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.1.0/24
Remote network/mask: 192.168.2.0/24
VPN Concentrator 2 Configuration:
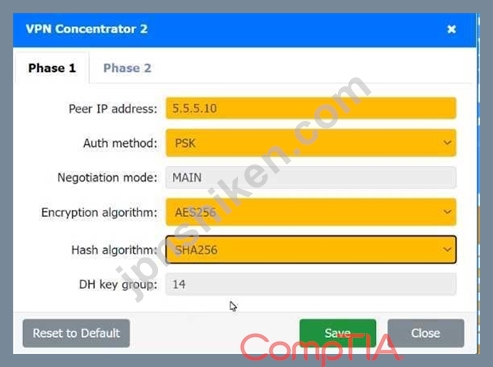
Phase 1:
Peer IP address: 5.5.5.5 (The IP address of VPN Concentrator 1)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.2.0/24
Remote network/mask: 192.168.1.0/24
Summary:
Peer IP Address: Set to the IP address of the remote VPN concentrator.
Auth Method: PSK for using a pre-shared key.
Negotiation Mode: MAIN for the initial setup.
Encryption Algorithm: AES256, which is a strong and secure algorithm.
Hash Algorithm: SHA256, which provides strong hashing.
DH Key Group: 14 for strong Diffie-Hellman key exchange.
Phase 2 Protocol: ESP for encryption and integrity.
Local and Remote Networks: Properly configure the local and remote network addresses to match each branch office subnet.
By configuring these settings on both VPN concentrators, the site-to-site VPN will meet the requirements for strong security algorithms, encryption of all traffic, and authentication using a pre-shared key.
Requirements:
Most secure algorithms should be selected.
All traffic should be encrypted over the VPN.
A secret password will be used to authenticate the two VPN concentrators.
VPN Concentrator 1 Configuration:
Phase 1:
Peer IP address: 5.5.5.10 (The IP address of VPN Concentrator 2)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.1.0/24
Remote network/mask: 192.168.2.0/24
VPN Concentrator 2 Configuration:
Phase 1:
Peer IP address: 5.5.5.5 (The IP address of VPN Concentrator 1)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.2.0/24
Remote network/mask: 192.168.1.0/24
Summary:
Peer IP Address: Set to the IP address of the remote VPN concentrator.
Auth Method: PSK for using a pre-shared key.
Negotiation Mode: MAIN for the initial setup.
Encryption Algorithm: AES256, which is a strong and secure algorithm.
Hash Algorithm: SHA256, which provides strong hashing.
DH Key Group: 14 for strong Diffie-Hellman key exchange.
Phase 2 Protocol: ESP for encryption and integrity.
Local and Remote Networks: Properly configure the local and remote network addresses to match each branch office subnet.
By configuring these settings on both VPN concentrators, the site-to-site VPN will meet the requirements for strong security algorithms, encryption of all traffic, and authentication using a pre-shared key.
- 質問一覧「112問」
- 質問1 ある企業が、社内ネットワークから発信される DNS トラフィック...
- 質問2 セキュリティ管理者は、機密性の高い顧客データの流出を防ぐため
- 質問3 最高情報セキュリティ責任者 (CISO) は、経営陣へのレポートで、...
- 質問4 セキュリティ アナリストは、サーバー上で悪意のある可能性のあ
- 質問5 侵入テスト中に、ベンダーはアクセス バッジを使用して許可され
- 質問6 システム管理者は境界ファイアウォールを設定しましたが、内部エ
- 質問7 技術者が新しいセキュリティ カメラを導入しています。技術者は
- 質問8 管理チームは、手動で設定された新しいアカウントに必ずしも正し
- 質問9 集中システム内の複数のソースからシステム、アプリケーション、
- 質問10 IT マネージャーは、ヘルプ デスク ソフトウェアの管理者コンソ...
- 質問11 次のどれがハードウェア固有の脆弱性ですか?
- 質問12 ホットスポットに関する質問 あなたは、ネットワーク上の潜在的
- 質問13 ある会社のベンダーがアナリストに BIOS アップデートを推奨する...
- 質問14 次のベスト プラクティスのうち、可用性を確保し、ビジネスへの
- 質問15 会社のマーケティング部門は、機密性の高い顧客データを収集、変
- 質問16 クラウド環境で意図しない企業認証情報の漏洩が発生する一般的な
- 質問17 従業員がフィッシング詐欺に引っかかり、攻撃者が会社の PC にア...
- 質問18 セキュリティ アナリストと管理チームは、最近のフィッシング キ...
- 質問19 セキュリティ アナリストが会社のパブリック ネットワークをスキ...
- 質問20 次のセキュリティ概念のうち、RADIUS サーバーのインストールに...
- 質問21 組織は、侵害が発生した場合に、ログイン データベースへの潜在
- 質問22 経理担当者は、新しい口座を使用するようにという不正な指示を受
- 質問23 企業が侵害を受けた後、顧客が訴訟を起こしました。会社の弁護士
- 質問24 次の侵入テスト チームのうち、攻撃者の戦術を使用して組織を侵
- 質問25 ある企業が災害復旧サイトを計画しており、単一の自然災害によっ
- 質問26 セキュリティ アナリストは、ネットワークへのアクセスを強化す
- 質問27 ローカルガイドラインでは、すべての情報システムが準拠するため
- 質問28 セキュリティ意識向上プログラムのコミュニケーション要素として
- 質問29 組織は財務データ記録を 3 年間、顧客データを 5 年間保持する必...
- 質問30 ネットワーク管理者は、会社のクラウド環境にロード バランサー
- 質問31 脆弱性スキャンを実行した後、システム管理者は、特定された脆弱
- 質問32 2 つの同一サイト間でトラフィックを分割してアプリケーションの...
- 質問33 新しい脆弱性が公開されたときに、セキュリティアナリストが組織
- 質問34 ある会社のユーザーから、新しい小売ウェブサイトの URL がギャ...
- 質問35 技術者が、SaaS プロバイダーによって導入およびサポートされて...
- 質問36 セキュリティ管理者がファイル共有を設定しています。管理者はデ
- 質問37 レガシー サーバーで実行されている重要なビジネス アプリケーシ...
- 質問38 ある組織では、常に可用性を必要とする顧客アプリケーションとデ
- 質問39 人事ファイル共有の権限が最小権限の原則に従うべき最も適切な理
- 質問40 部門は、会社のさまざまなサービスやシステムにアクセスする際に
- 質問41 ある企業は、セキュリティ運用を主導するために、社外からセキュ
- 質問42 セキュリティ アナリストがドメイン アクティビティ ログを確認...
- 質問43 ネットワーク管理者は、次の要素を使用する多要素認証を実装して
- 質問44 ある企業が政府向けの重要なシステムを開発しており、プロジェク
- 質問45 セキュリティ保護された施設への訪問者は、写真付き身分証明書で
- 質問46 ある企業が機密ストレージ アレイを廃棄し、廃棄を完了するため
- 質問47 次のどれが、データベースの誤った構成を悪用しようとする試みに
- 質問48 ある企業は、天候によるサーバールームの損傷やダウンタイムを懸
- 質問49 ある組織では、顧客データを、メインの企業ネットワーク上のユー
- 質問50 サーバー上で検出された CVE に対処する管理者の能力に最も影響...
- 質問51 ファイアウォール構成のトラブルシューティング中に、技術者は A...
- 質問52 銀行環境で監査を完了する最も適切な理由はどれですか?
- 質問53 ある組織が、コストと利益を主な要件とし、RTO と RPO の値が約 ...
- 質問54 ある企業では、廃棄したシステムをリサイクルに出す前にハードド
- 質問55 管理者は、組織外にこれらのファイルを電子メールで送信しようと
- 質問56 DDoS 攻撃に対する保護を提供する製品を実装する際に、次のセキ...
- 質問57 クラウド環境で意図しない企業認証情報の漏洩が発生する一般的な
- 質問58 ハッカーは、ユーザーが疑わしいリンクをクリックしたことによる
- 質問59 システム管理者は、クラウドベースの低コストのアプリケーション
- 質問60 ある企業は、自社が導入しているソフトウェアが、そのソフトウェ
- 質問61 ある企業では、データベース管理者のワークステーションからデー
- 質問62 次のシナリオのうち、ビジネス メール詐欺攻撃の可能性を説明し
- 質問63 攻撃者の活動や手法を入手して分析するために導入される可能性が
- 質問64 管理者は、ユーザーが勤務時間外にリモートでログインし、大量の
- 質問65 アナリストは、データ プレーン内でのゼロ トラスト原則の実装を...
- 質問66 管理者が単一サーバーのセキュリティ ログを確認したところ、次
- 質問67 システム障害が発生した場合に組織が復元プロセスを適切に管理す
- 質問68 ハリケーンが発生しやすい地域にある会社が災害復旧計画を策定し
- 質問69 次の脅威アクターのうち、利益を動機とする可能性が高いのはどれ
- 質問70 セキュリティ管理者が新しいファイアウォール ルール セットを設...
- 質問71 許可された担当者だけが安全な施設にアクセスできるようにするに
- 質問72 リスク、責任者、しきい値を文書化するために最もよく使用される
- 質問73 ある企業は第三者と連携しており、安全なファイル移行のために双
- 質問74 従業員が退職したときに権限を迅速に更新することで組織のセキュ
- 質問75 顧客の個人情報を含むファイルを誤って電子メールで送信した従業
- 質問76 ある組織は、サードパーティベンダーに特定のデバイスを対象とし
- 質問77 ある会社が業務をクラウドに移行することを決定しました。この会
- 質問78 ラボシミュレーション1 システム管理者は、2 つのブランチ オフ...
- 質問79 グラフィック画像内にコードやテキストを隠すプロセスを説明して
- 質問80 ある企業が物理サーバーを廃止し、個々のオペレーティング シス
- 質問81 組織がインシデント対応プロセスを改善するために使用すべき演習
- 質問82 次のチームのうち、組織の重要なシステムを保護するために、攻撃
- 質問83 ソフトウェア会社の最終的なソフトウェア リリースに脆弱なコー
- 質問84 ある企業がインフラストラクチャを再設計し、使用中の物理サーバ
- 質問85 攻撃者が悪意のあるアドレスでレジスタを上書きすると、次の脆弱
- 質問86 セキュリティ インシデントが発生した後、システム管理者は会社
- 質問87 企業の公開ウェブサイトhttps://www.organization.comのIPアドレ...
- 質問88 クラウド プロバイダー内でリソースを簡単に展開できるようにす
- 質問89 医療機関は、個人が健康上の緊急事態をデジタルで報告できる Web...
- 質問90 内部者が企業の開発プロセスに悪意のあるコードを持ち込むのを防
- 質問91 一方向データ変換アルゴリズムを使用する前に、複雑さをさらに追
- 質問92 ある組織では、サーバーのハードウェアの問題を解決するために必
- 質問93 運用サーバーに影響を与えずに潜在的な攻撃者の活動を特定するた
- 質問94 マネージャーは、払い戻しを受けるためのリンクが記載されたメー
- 質問95 システム管理者は、外部 Web サーバーが正常に機能していないと...
- 質問96 従業員が侵害された業界ブログにアクセスした後、マルウェアが会
- 質問97 ある企業は、情報がオンライン フォーラムに漏洩するのを防ぐた
- 質問98 次のタスクのうち、BIA プロセスに通常含まれるものはどれですか...
- 質問99 管理者は、複数のユーザーが疑わしい IP アドレスからログインし...
- 質問100 ある企業が、リスク登録簿に記載されている項目に対処するために
- 質問101 従業員は、会社の最高経営責任者を名乗る未知の番号から、ギフト
- 質問102 退職前に顧客リストを個人アカウントに電子メールで送信している
- 質問103 ある組織で、コマンド アンド コントロール サーバーに関連する...
- 質問104 次の脆弱性のうち、製造元が承認したソフトウェア リポジトリの
- 質問105 サーバーのセキュリティ設定が変更されたかどうかを毎日一貫して
- 質問106 許容されるリスクの最大許容度を説明するのは次のどれですか?
- 質問107 セキュリティ エンジニアが組織内のすべてのラップトップに FDE ...
- 質問108 セキュリティ意識向上トレーニング セッションの後、ユーザーが ...
- 質問109 管理者は、展開前にサーバーの強化を実行する必要があります。管
- 質問110 入力フィールドを使用して、データを表示または操作できるコマン
- 質問111 セキュリティ意識向上プログラムのトレーニング カリキュラム プ...
- 質問112 企業は、保存されている機密データが読み取り不可能な状態になっ

