- ホーム
- CompTIA
- PT0-002J - CompTIA PenTest+ Certification (PT0-002日本語版)
- CompTIA.PT0-002J.v2023-11-21.q141
- 質問98
有効的なPT0-002J問題集はJPNTest.com提供され、PT0-002J試験に合格することに役に立ちます!JPNTest.comは今最新PT0-002J試験問題集を提供します。JPNTest.com PT0-002J試験問題集はもう更新されました。ここでPT0-002J問題集のテストエンジンを手に入れます。
PT0-002J問題集最新版のアクセス
「460問、30% ディスカウント、特別な割引コード:JPNshiken」
侵入テスト担当者が侵入テストを実施していて、クライアントが所有する Web サーバーの脆弱性を発見しました。この脆弱性を悪用すると、テスターはリバース シェルを開くことができます。権限昇格のためにサーバーを列挙すると、テスターは次のことを発見します。
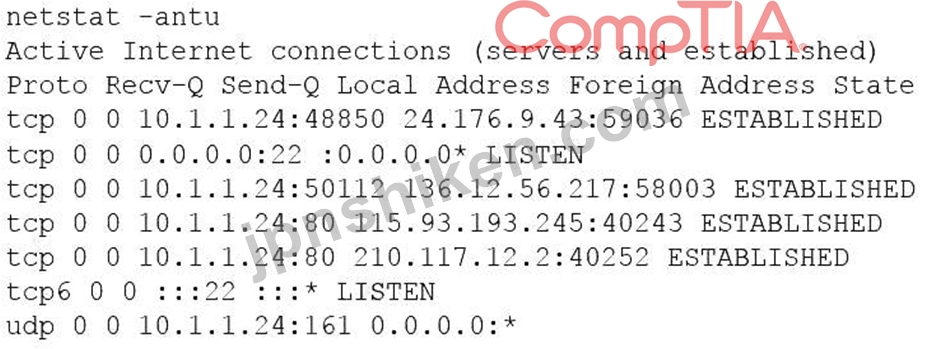
ペネトレーションテスターが次に行うべきことは次のうちどれですか?

ペネトレーションテスターが次に行うべきことは次のうちどれですか?
正解:C
Explanation
The image shows the output of the netstat -antu command, which displays active internet connections for the TCP and UDP protocols. The output shows that there are four established TCP connections and two listening UDP connections on the host. The established TCP connections have high numbered ports as their local addresses, such as 49152, 49153, 49154, and 49155. These ports are in the range of ephemeral ports, which are dynamically assigned by the operating system for temporary use by applications or processes. The foreign addresses of these connections are also high numbered ports, such as 4433, 4434, 4435, and 4436. These ports are not well-known or registered ports for any common service or protocol. The combination of high numbered ports for both local and foreign addresses suggests that these connections are suspicious and may indicate a backdoor or a covert channel on the host. Therefore, the penetration tester should investigate these connections next to determine their nature and purpose. The other options are not appropriate actions for the penetration tester at this stage.
The image shows the output of the netstat -antu command, which displays active internet connections for the TCP and UDP protocols. The output shows that there are four established TCP connections and two listening UDP connections on the host. The established TCP connections have high numbered ports as their local addresses, such as 49152, 49153, 49154, and 49155. These ports are in the range of ephemeral ports, which are dynamically assigned by the operating system for temporary use by applications or processes. The foreign addresses of these connections are also high numbered ports, such as 4433, 4434, 4435, and 4436. These ports are not well-known or registered ports for any common service or protocol. The combination of high numbered ports for both local and foreign addresses suggests that these connections are suspicious and may indicate a backdoor or a covert channel on the host. Therefore, the penetration tester should investigate these connections next to determine their nature and purpose. The other options are not appropriate actions for the penetration tester at this stage.
- 質問一覧「141問」
- 質問1 侵入テスターは、電子メールの添付ファイルを使用してデータの流
- 質問2 侵入テスターがサーバーに対してスキャンを実行し、次の出力を取
- 質問3 エクスプロイトの開発者は、サーバーが侵害されるまで、非常に多
- 質問4 侵入テスターは、SSHD が実行されている Linux サーバーで実行す...
- 質問5 エンゲージメントを行っているペネトレーション テスターは、特
- 質問6 次のうち、OWASP トップ 10 を最もよく表しているのはどれですか...
- 質問7 侵入テスターは、Linux ベースのファイル サーバーへのルート ア...
- 質問8 赤いチームは、エンゲージメント中にクライアントの内部ネットワ
- 質問9 侵入テスターは、特定のドメインの Web 上で入手可能なドキュメ...
- 質問10 侵入テスターが、保護されていない内部ソース コード リポジトリ...
- 質問11 次のコードがあるとします。 (Exhibit) 次のデータ構造のうち、...
- 質問12 侵入テスト中に、認証要件のない Web コンポーネントが見つかり...
- 質問13 IoT デバイスが受動的偵察をサポートするためにベンダーやその他...
- 質問14 評価のスコーピング段階で、クライアントは、脆弱性をできるだけ
- 質問15 評価中に、ペネトレーション テスターは、以前の侵害を示す可能
- 質問16 ペネトレーションテスターは最終報告書に次のコメントを書いた:
- 質問17 非特権アカウントで Linux システムにアクセスした後、ペネトレ...
- 質問18 あるソフトウェア会社は、会社のソフトウェア開発プラクティスの
- 質問19 侵入テスターは、dirb ユーティリティを使用して Web サーバーを...
- 質問20 ペネトレーション テスターは、クライアントの金融システムにア
- 質問21 侵入テスト担当者は、次の侵入テストのために次のフィッシング
- 質問22 文字列値を別の文字列に追加すると、次のように呼び出されます。
- 質問23 コンサルタントは、リモート ホストで開いているすべてのポート
- 質問24 侵入テスターは、システムで次のコマンドを実行します。 検索 / ...
- 質問25 顧客は、侵入テストの範囲に、アクティビティは通常の営業時間中
- 質問26 侵入テスターは、クライアントのシステムの評価中にいくつかの重
- 質問27 セキュリティ会社は、侵入テストの結果についてクライアントと話
- 質問28 侵入テスターは、Nmap スキャンから次の結果を受け取ります。 (E...
- 質問29 セキュリティ評価を行っているペネトレーション テスターは、重
- 質問30 ペネトレーション テスターは、Windows ホストへのシェル アクセ...
- 質問31 侵入テスターは、サーバーから MD5 ハッシュを収集し、レインボ...
- 質問32 物理的な侵入テスターは、疑わしい行動をしたり、警備員に気付か
- 質問33 侵入テスターは最近、企業環境内のコア ネットワーク デバイスの...
- 質問34 侵入テスターは、MITRE ATT&CK フレームワークを企業の主任...
- 質問35 ある会社は、侵入テスト用に次のネットワーク スコープを提供し
- 質問36 Nmap ネットワーク スキャンにより、サービスが特定された 5 つ...
- 質問37 ペネトレーション テスターが検出スキャンを実行した結果、次の
- 質問38 侵入テストを実行しているテスターは、リモート攻撃に対して重大
- 質問39 侵入テスターはクライアントのオフィスにあるラップトップでシェ
- 質問40 エンゲージメント中に、侵入テスターがファイル内に次の文字列の
- 質問41 次の状況のうち、以前のセキュリティ評価の再検証を正当化する可
- 質問42 ある企業が侵入テスターを雇って、従業員に対してソーシャル エ
- 質問43 侵入テスターは、Web アプリケーションのコマンド インジェクシ...
- 質問44 日常業務の中断を最小限に抑える必要がある企業には、企業の Web...
- 質問45 ペネトレーション テスターは、192.168.1.0/24 範囲内の一連のタ...
- 質問46 ペネトレーション テスターは、新しいクライアントと共にスコー
- 質問47 ユーザー資格情報は、評価中にデータベースから取得され、レイン
- 質問48 ペネトレーション テスターは、侵害された Web サーバーから Jav...
- 質問49 次のうち、攻撃者が使用する一般的な戦術と手法のマトリックスと
- 質問50 侵入テストのスキャン段階の実行中に、侵入テスターは次のコマン
- 質問51 Web アプリケーションのテスト中に、侵入テスターは https://com...
- 質問52 侵入テスト中にセキュリティ アラームがトリガーされると、企業
- 質問53 偵察段階で、侵入テスターは次の出力を取得します。 192.168.1.2...
- 質問54 次のうち、アプリケーション コードでサードパーティのオープン
- 質問55 侵入テスターは、Windows サーバーで次のコマンドを実行しました...
- 質問56 最悪の条件下でテストするには、次の OSSTM テスト方法論のうち...
- 質問57 ペネトレーション テスターはパス上の攻撃位置を確立し、ターゲ
- 質問58 侵入テスターは、評価の対象となった 16 ビットのネットワーク ...
- 質問59 ペネトレーション テスターは、内部の Web サーバーに対してブル...
- 質問60 侵入テスターは、検出されることなく偵察を実行したいと考えてい
- 質問61 侵入テスターは、クライアントとサーバー間の NTLM チャレンジ/...
- 質問62 ion tester は、ターゲット企業からより多くの人々に実行可能フ...
- 質問63 侵入テストの取り組みを計画するときは、テストの実行に最適な時
- 質問64 侵入テスターは、評価対象の会社によって作成されたさまざまなソ
- 質問65 侵入テスターが Web サイトをクロールし、Web サイトのパスワー...
- 質問66 侵入テストを実施するために、セキュリティ エンジニアは IT ヘ...
- 質問67 許可されていない開示を防止するための侵入テスターとクライアン
- 質問68 アプリケーション開発者のチームを対象読者として作成された静的
- 質問69 メール サービス会社は、侵入テスターを雇って、SMTP サーバー上...
- 質問70 侵入テスト担当者が侵入テストを実施していたところ、ネットワー
- 質問71 システムに侵入した後、ペネトレーションテスターは、次にどのよ
- 質問72 クラウド環境で侵入テストを行う際、侵入テスト担当者が最初に考
- 質問73 次の PowerShell スニペットは、攻撃者のマシンのログから抽出さ...
- 質問74 ペネトレーション テスターは、dig からの comptia.org の次の D...
- 質問75 PCI DSS では、侵入テスト プロセスの一環として、次のうちどれ...
- 質問76 クライアントは、セキュリティ評価会社に、そのホット サイトに
- 質問77 侵入テスターは、範囲内にある企業の Web アプリケーション内の...
- 質問78 ソフトウェア会社のネットワーク上のすべてのサーバーの認証スキ
- 質問79 評価中、ペネトレーション テスターは LFI の脆弱性を悪用し、We...
- 質問80 インターネットに直接接続されている IoT デバイスに関連する最...
- 質問81 セキュリティ アナリストは、BLE スマート デバイスに対してオン...
- 質問82 新しいクライアントは、クライアントの新しいサービスに対するさ
- 質問83 忘れられる権利を実装することでユーザーのプライバシーに重点を
- 質問84 侵入テスターはマシンで unshadow コマンドを実行します。次のツ...
- 質問85 会社のセキュリティ慣行の物理的評価を行っているペネトレーショ
- 質問86 ある民間調査会社は、攻撃者がモバイル デバイスにアクセスして
- 質問87 侵入テスト中、テスト担当者は、Bluetooth フレームをブロードキ...
- 質問88 侵入テスターはターゲットに対して Nmap スキャンを実行し、次の...
- 質問89 ペネトレーション テスターは、脆弱性を探すために石油リグ ネッ...
- 質問90 内部侵入テスト中、攻撃マシンはターゲット ホストと同じ LAN セ...
- 質問91 次の概念のうち、侵入テスト中に実行される特定の一連の手順とア
- 質問92 侵入テスターは、内部ネットワークの一部へのアクセスを取得し、
- 質問93 変数 val を 1 増やす Python の次の式はどれですか (2 つ選択し...
- 質問94 侵入テスターは、Web サイトで発見された検索フォームで入力の検...
- 質問95 ペネトレーションテスターが、ある場所でテストを行う際に考慮す
- 質問96 評価者は、できるだけ静かに Nmap スキャンを実行したいと考えて...
- 質問97 次の文書のうち、侵入テスターの特定の活動、成果物、およびスケ
- 質問98 侵入テスト担当者が侵入テストを実施していて、クライアントが所
- 質問99 ネットワーク スイッチの Nmap スキャンでは、次のことが明らか...
- 質問100 侵入テスターは、保護されていないネットワーク ファイル リポジ...
- 質問101 侵入テスターがサーバーを侵害し、権限をエスカレートすることが
- 質問102 ソフトウェア会社は、侵入テスト担当者を雇って、データベース
- 質問103 いつ URL http://192.168.0-1/validate/user.php にアクセスする...
- 質問104 Nmap スキャンの結果は次のとおりです。 Nmap 7.80 ( https://nm...
- 質問105 侵入テスターは、インターネットに接続されたネットワーク デバ
- 質問106 侵入テスターは、特権ユーザーのパスワードが 30 の異なる Linux...
- 質問107 侵入テスターは、1 つのエンゲージメントで使用される次のスクリ...
- 質問108 侵入テスターがクライアントの Web サイトを探索しています。テ...
- 質問109 侵入テスト担当者は、侵入テストの最後にトラックをクリーンアッ
- 質問110 企業は、共有ネットワーク帯域幅を持つクラウド プロバイダーを
- 質問111 ある会社は、クラウド サービス プロバイダーから脆弱性スキャン...
- 質問112 侵入テスターがサーバーの脆弱性を悪用し、ペイロードをリモート
- 質問113 アクティブなサービスの列挙の過程で、ペネトレーション テスタ
- 質問114 侵入テストの最終レポートは、審査のために理事会に提出され、承
- 質問115 組織内で侵入テストを実施するには、実行できる演習の性質と種類
- 質問116 ペネトレーションテスターは未知の環境テストを実施し、後の評価
- 質問117 侵入テスターは、システム管理者に次のコマンドを提供して、ター
- 質問118 侵入テスターは、会社の業務の中断を最小限に抑える必要があるク
- 質問119 評価中、ペネトレーション テスターは、対象企業の Web サイトを...
- 質問120 ペネトレーション テスターは、ネットワーク スイッチの脆弱性を...
- 質問121 システム管理者と技術スタッフが閲覧できる侵入テストレポートの
- 質問122 Nmap スキャンは、Web サーバーとデータベースで開いているポー...
- 質問123 侵入テスターは、組織のソース コード管理ソリューション内のア
- 質問124 次のツールのうち、Web アプリケーションのセキュリティ評価を手...
- 質問125 コンプライアンスベースの侵入テストは、主に次のことに関係して
- 質問126 侵入テスターは、攻撃者が物理アクセス制御システムに使用される
- 質問127 侵入テスターは、Web サーバーに対して脆弱性スキャンを実行する...
- 質問128 ペネトレーション テスターがコード リポジトリを発見し、パスワ...
- 質問129 侵入テスターは次のコマンドを実行します。 curl -I -http2 http...
- 質問130 侵入テスターは、ROE によって許可されている概念実証攻撃を...
- 質問131 侵入テスト活動が終了し、最初の調査結果がクライアントとレビュ
- 質問132 企業組織との契約を準備する際に、侵入テスト活動を開始する前に
- 質問133 侵入テスターは、PCI DSS v3.2.1 準拠の金融システムでテストを...
- 質問134 クラウド セキュリティ評価を実行するには、次のツールのうちど
- 質問135 自動車業界向けの組み込みソフトウェアを開発している会社は、製
- 質問136 次のうち、企業のハント チームが最終レポートで最も関心を持っ
- 質問137 侵入テスターは、VoIP コール マネージャーで新たにリリースされ...
- 質問138 ペネトレーション テスターが、最高経営責任者 (CEO) の社内の企...
- 質問139 会社から要求された評価を行っているペネトレーション テスター
- 質問140 パブリック クラウドのアカウントとリソースを管理するためのル
- 質問141 侵入テスターは、モバイル クライアントのラップトップ上の Wind...

